Previously, controlled reception pattern antennas (CRPAs) were only in the military domain, and highly classified. The need to counter increasing GNSS signal jamming and spoofing in the civil realm has brought CRPAs into limited use there as well. How to test for their efficacy in product design and development?
A free webinar on Wednesday, March 25 from 1:00 PM – 2:30 PM Eastern Daylight Savings Time addresses the topic “GNSS Vulnerability Testing and the Controlled Reception Pattern Antenna (CRPA).” This technically rich, educational event is sponsored by Spirent Communications and Inside GNSS.
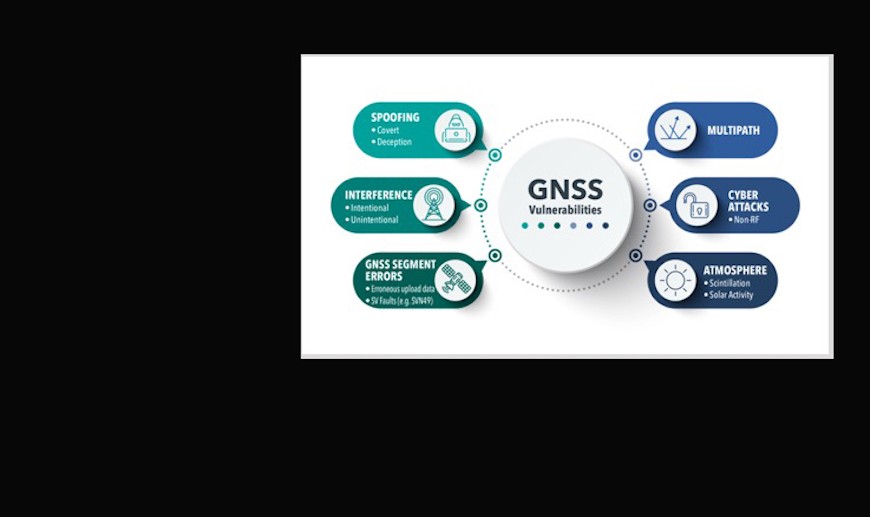
GNSS vulnerability presents many challenges for PNT product designers and users. Interference with safety, reliability and productivity are all serious matters. Leading experts specializing in research and development regarding and simulation and CRPAs — often the first line of defense against jamming — share their perspective and findings in this free webinar.
All those interested in robust PNT signals, safe navigation, autonomous navigation and new product development will profit from the in-depth technical insights afforded by this hour-and-a-half tutorial.
Register now for this free webinar.
The discussion gives a holistic overview of GNSS vulnerability, not simply relative to jamming and spoofing but also:
- cyber attacks and other newly developed efforts to crash receivers;
- efficient RFI simulation testing: modeling the transmitters, how many to model, simulating moving transmitters;
- the full range of risks and trends;
- signal vulnerability from the perspective of CRPA applications;
- key parameters for RFI simulation
- and why it is important to simulate at all phases of product development.
Demonstrations and key takeaways include:
- The advantages of simulation over testing in the field, and what constitutes a good simulator.
- What to look for when selecting a CRPA system for purchase: the performance you should expect.
- The significance and impacts of new signal authentication schemes, set to begin this quarter with Galileo and to be further implemented with testing aboard NTS-3 of the Chimera concept.
- risk assessment in specific scenarios such as autonomous driving.
- what have been the mistakes in testing in the past, the emerging standards and what we can expect in the future.
- Test results and illustrative data.
The expert panel:
 Kimon Voutsis, PhD. Product Manager for High-end PNT Test Solutions at Spirent Communications. Kimon has more than 10 years of professional experience in providing guidance and technical solutions for positioning, navigation and timing applications, to military, governmental and commercial organizations. He holds a Ph.D. in Robust Positioning, Navigation & Timing Applications from the Space Geodesy & Navigation Laboratory, Department of Civil, Environmental & Geomatic Engineering, University College London.
Kimon Voutsis, PhD. Product Manager for High-end PNT Test Solutions at Spirent Communications. Kimon has more than 10 years of professional experience in providing guidance and technical solutions for positioning, navigation and timing applications, to military, governmental and commercial organizations. He holds a Ph.D. in Robust Positioning, Navigation & Timing Applications from the Space Geodesy & Navigation Laboratory, Department of Civil, Environmental & Geomatic Engineering, University College London.
 Oscar Pozzobon, Technical Director, Qascom. Oscar is the founder and technical director of Qascom. He has been working in the domain of GNSS security, authentication and robust navigation for more than 20 years. As technical director he coordinates the four units of Qascom of Engineering & Cybersecurity, Simulation Systems, Advanced Navigation and Attack Detection Systems. He coordinates a number of space programs and activities with the European Space Agency (ESA), the European GNSS Agency (GSA),the European Commission (EC), the National Aeronautics and Space Administration (NASA) and the Italian Space Agency. Since 2008, He contributed to the design and testing of 2 of the 5 Galileo services. His main interests are Space, GNSS and cryptography, where he has issued more than 50 publications. He is adjunct professor at the University of Padova for Satellite Navigation. He has a Master in Telecommunication engineering and a Ph. D. in Aerospace and Satellite Applications.
Oscar Pozzobon, Technical Director, Qascom. Oscar is the founder and technical director of Qascom. He has been working in the domain of GNSS security, authentication and robust navigation for more than 20 years. As technical director he coordinates the four units of Qascom of Engineering & Cybersecurity, Simulation Systems, Advanced Navigation and Attack Detection Systems. He coordinates a number of space programs and activities with the European Space Agency (ESA), the European GNSS Agency (GSA),the European Commission (EC), the National Aeronautics and Space Administration (NASA) and the Italian Space Agency. Since 2008, He contributed to the design and testing of 2 of the 5 Galileo services. His main interests are Space, GNSS and cryptography, where he has issued more than 50 publications. He is adjunct professor at the University of Padova for Satellite Navigation. He has a Master in Telecommunication engineering and a Ph. D. in Aerospace and Satellite Applications.