A Department of Homeland (DHS)-chartered May 2021 report concludes that PNT threat and resilience concerns are not as dire as some have made them out to be, and that funds for backup could be spent elsewhere. Why this runs counter to other recent government reports is not clear, nor is the fallout from this divergence of Congressionally mandated views. The Department of Transportation has distanced itself a bit from this report by the RAND Corporation—and even its issuer, the DHS, seems to have done so.
This column breaks down the 286-page DHS report written by the RAND Corporation, “Analyzing a More Resilient National Positioning, Navigation, and Timing Capability.” The document seems to both complement (no pun) and contradict the Department of Transportation’s (DOT) earlier Complementary PNT Report. It is unclear how Congress will react to it, or how it may ultimately impact federal budgets and programs.
Late to the Party?
In §1618 of the Fiscal Year 2017 National Defense Authorization Act (FY 17 NDAA), Congress required a timely, full, and joint DHS, DOT and the Department of the Defense (DOD) study “to assess and identify the technology-neutral requirements to backup and complement the positioning, navigation, and timing capabilities of the Global Positioning System for national security and critical infrastructure.” This was supposed to be due no more than one year after the date of enactment.
Three and a half years after the deadline, RAND, a nonprofit, nonpartisan, public-interest research organization, which runs the DHS’ Homeland Security Operational Analysis Center under contract, published this “partial response.”
While the DOT supported the effort, the DOD did not. As such, the report solely focused on domestic non-military PNT issues associated with critical infrastructure.
Interestingly, the FY17 NDAA requirement was actually fulfilled, at least from the DOT perspective, by a DHS report submitted to Congress in April 2018: the Report on Positioning, Navigation, and Timing (PNT) Backup and Complementary Capabilities to the GPS National Defense Authorization Act Fiscal Year 2017 Report to Congressßß. That report found:
• GPS IS NOT THE ONLY SOURCE OF PNT DATA. Other sources are available for purchase, and include alternate space-based systems and constellations, terrestrial beaconing, time-over-fiber, cellular and wireless signals, and local terrestrial systems.
• APPLY PNT PRINCIPLES. Whatever the PNT source, users must apply the principles found in Executive Order 13905, Strengthening National Resilience Through Responsible Use of Positioning, Navigation, and Timing Services.
• NO INCENTIVES FOR NON-GPS PNT. Unless non-GPS PNT sources are free/low-cost or provide a unique benefit deemed valuable by the user, there is no reason to assume users will adopt new non-GPS PNT sources more widely than they have.
• MANY SECTORS RELY ON PNT. Disruption would cause significant costs, delays, or degradation of functions and service.
• SECTOR NEEDS DIFFER. Some sectors require very precise timing, while in others position and navigation precision is more important.
• CHOICES WILL CAUSE ANY FAILS. Critical infrastructure that ceases to operate due to GPS disruptions will do so because of design choices associated with a lack of information, cost, efficiency, and other considerations—not because of a lack of available options.
• DECONFLICTION NECESSARY. New non-GPS PNT systems that are designed without considering existing PNT systems may simply compete with existing systems rather than fill perceived backup gaps.
• NO ONE SOLUTION. No single PNT system, including GPS, can fulfill all user requirements and applications.
• PUBLIC-PRIVATE DEVELOPMENT NEEDED. Position and navigation backups must be application-specific, developed in coordination with industry owners and operators.
• TIMING IS THE EASIEST PROBLEM TO SOLVE. Timing requirements are simple, with a minimal acceptable precision of anywhere between 65-240 nanoseconds.
That same earlier FY17 Report made these four recommendations:
• TEMPORARY GPS DISRUPTIONS: End users should be responsible for mitigating temporary GPS disruptions. The Federal Government can facilitate mitigation for various critical infrastructure sectors, but should not be solely responsible for it.
• PNT DIVERSITY AND SEGMENTATION: Adoption of multiple PNT sources will diffuse the risk currently concentrated in wide-area PNT services such as GPS.
• SYSTEM DESIGN: PNT systems must be designed with inherent security and resilience features.
• PURSUE INNOVATION THAT EMPHASIZES TRANSITION AND ADOPTION: Incorporating PNT signal diversity should take into account factors such as business case considerations, financial costs, technical integration, and logistical deployment.
What’s New?
This newest RAND report doesn’t add much other than to cast a bit of doubt on the extent of monetary impacts that a GPS outage will actually have on critical infrastructure.
Real Risks. Overblown Impacts?
The RAND report validated that various threats could destroy, deny, or trick GPS signals. On the one end of the spectrum, acts of war can erupt into state-level nuclear exchanges. Extreme space weather events can impact space systems. Both would have large scale to catastrophic effects. On the other end, localized GPS jamming or spoofing, whether negligently or intentionally caused, would likely have localized and short-lived effects. Other natural or intentional events of varying scope and duration, such as PNT terrorism, computer system failures, or simple communications breakdowns remain in the realm of the possible. Similarly, PNT and GPS back-ups could also be vulnerable to these and other threats, such as terrestrial systems which seem more susceptible to physical attacks.
While acknowledging that insufficient data exists “to make defensible probability estimates,” the report nevertheless concludes that, aside from unfathomable nuclear holocaust, virtually all other GPS disruption or loss scenarios would have small-scale impacts lasting only a few days. Only a geomagnetic storm implied economy-wide disruption. Even this, the report says, would last for only a few days. Major assumptions on the short-lived nature of these impacts include that law enforcement would catch perpetrators of intentional acts and that already-existing complementary tech, old fashioned pre-GPS practice, and/or steadfast American gumption would keep the economy grinding on.
Hundreds, Thousands of Millions in Losses
Estimated economic costs resulting from the varied threats to PNT from a nationwide outage, “range, on a daily basis, from a low estimate of $785 million to a high value of $1,318 million.” Based on 2018 rates, likely nation-wide aggregate losses by economy sector, in millions of dollars per day (unless otherwise noted), follow:
• Consumer Based-Location Services (cell phones and apps)—$94M;
• Commercial Road Transport—$141M
• Emergency Services—ranges from $11M to $72M with median at $32M
• Agriculture—ranges form $42M to $514M based on time of year;
• Construction—$24M;
• Surveying—$7M
• Aviation—$6M
• Railway—$100,00
• Telecommunications—$40M (day 1) up to $456M (after 30 days);
• Electricity Generation/Transmission—$9M
• Finance—$9M;
• Port Operations—$224M, aggregate 30-day outage $6.7B
• Mining—$32M
• Oil & Gas Exploration—30 day outage $1.5B
Estimates drop by orders of magnitude when one makes reasonable assumptions about alternate available systems and the projected short duration of any PNT outages.
So Many Alternatives
According to the findings, many alternative sources and technologies already exist to increase national PNT resilience and robustness. No one-size-fits-all solution exists because users have different needs, such as:
• Precision Timing on Networks—modern communication networks, including financial networks and electrical power networks, need a common time standard for tightly synchronized operations. Examples include emergency services Land Mobile Radio systems and Financial Services high-frequency trading networks.
• Moderate-Accuracy Positioning of People and Road Vehicles—typically on smartphones and similar devices, used by the public and many commercial industries for directional, logistical and similar applications.
• High-Accuracy Positioning of Equipment—for surveying and the guidance of expensive equipment for construction, mining, drilling, or agriculture.
• High-Reliability Positioning in Aircraft Landing—required in vertical position accuracy
• Low-Accuracy Positioning of Aircraft and Ships En Route—needed in wide-area coverage possible far from shore or land
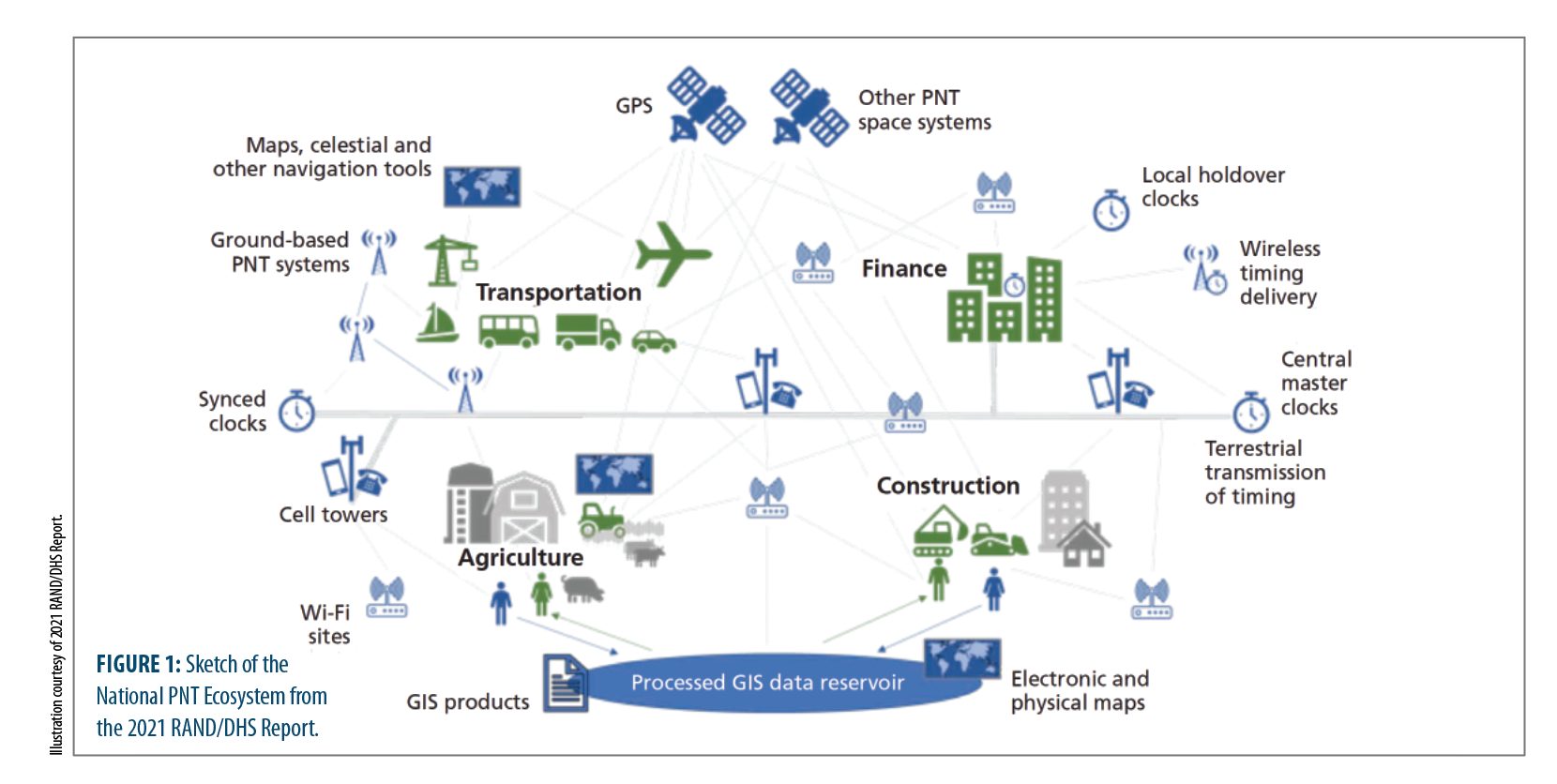
Alternatives for these needs run the gambit of other wireless PNT signals, RF “signals of opportunity” (like Locata which is used over defined areas, such as ports and mines, where GPS reception might be unreliable or impossible), wireless time signals, wired time signals, user equipment-based solutions and PNT resilience technologies. These solutions can cross user-need categories. Many of these alternative PNT technologies or supplemental systems already exist but have not been widely implemented; others are in earlier stages of development (see Figure 1).
Of all of these, the report locks onto “one seamless backup for GPS”—other GNSS constellations that use similar signals in the same radio band, such as Galileo, GLONASS and BeiDou. That said, the U.S. prefers not to depend on adversary sat systems. That leaves Galileo, which itself experienced a significant outage in December 2020.
Threats Don’t Justify Backups
Cost drivers for complementary tech include new space infrastructure, new terrestrial infrastructure in covered areas, and individual user costs to utilize for PNT. Other than stating, “even costs of tens to hundreds of dollars per user could add up to substantial costs over relevant user bases,” the report outlines no other dollar figures for these “costly” systems (possibly because detailed cost estimates for potential alternative PNT systems are proprietary to various firms). Yet it concludes, “If the costs of a national GPS disruption are at most in the tens to hundreds of millions per day—and if any single backup system would mitigate only a portion of those costs—then the risk does not justify more than modest government investment in any single backup system.”
Take jamming in an urban area, as an example. To have more than a localized effect, someone would have to intentionally stage a large number of jammers of different levels of power and reach around the city to disrupt GPS. More than a hundred such local attacks per decade would be needed to match the costs of the cheaper alternative PNT systems to hedge against this possibility. “Given the complete absence of such attacks to date,” the report notes, “the threat of such attacks does not come even close to justifying investments in the backups or alternatives we examined.” Spoofing, on the other hand, can be readily detected in any sensitive applications through integrity monitoring, in RAND’s opinion.
So, what’s the plan? The report outlines four cost-effective measures the feds could implement:
• Information sharing and standards for hardening or quality monitoring for those systems now relying on GPS—the federal government should share information with the locals
• Expansion of law enforcement authorities focused on GPS jamming—make it painful for criminals to do this by allowing fines that could be recycled back into buying or maintaining resilient systems
• Timing-only backup through fiber/FirstNet, eLoran, or Satellite Time and Location (which uses the Iridium constellation)
• Expansions of economically successful but geographically limited systems offering high performance (whether 5G, MBS, or other) in neglected areas.
Additionally, maintaining “time-proven, robust fallbacks” to PNT, keeping diverse and dispersed PNT capabilities in the national PNT ecosystem, and designing non-GPS reliant systems are also essential.
Diverging Points of View
This latest RAND Report doesn’t deviate much from DHS’ FY17 Report, at least from a wave-top standpoint. However, when you compare it to DOT’s Complementary PNT Report, the conclusions diverge when it comes to toughening PNT. The breakdown, according to Karen Van Dyke, Director of DOT OST-R’s Office of PNT & Spectrum Management, who contributed information to the RAND report, when it comes to PNT resiliency, follows:
• Protect: GPS/GNSS Performance Monitoring and Interference Detection. DOT agrees with the RAND report on the need for an interference/threat detection capability.
• Toughen: GPS signal authentication and cyber-resilient user equipment. DOT considers this capability to be important, while the RAND report appears to minimize the likelihood that these are threats to GPS that need to be addressed.
• Augment: through complementary PNT service. The Office of the Assistant Secretary for Research and Technology at US DOT, through work authorized and funded under the FY 2018 National Defense Authorization Act (NDAA), has demonstrated mature PNT technologies that complement and could provide a backup to the GPS service in case of a major disruption. Many of these technologies are already commercially available to owners and operators of critical infrastructure. During federally funded research demonstrations, these technologies and their vendors displayed significant potential to mitigate the risks faced by users who rely exclusively on GPS/GNSS services. This finding largely aligns with the RAND report.
VanDyke also points out that, in contrast to the RAND report, DOT believes there is an important role that the federal government, in particular DOT, needs to play with respect to:
• Development of safety-critical PNT requirements and standards for transportation services.
• Development of a PNT vulnerability and performance testing framework of demonstrated and suitable complementary technologies.
• Development of PNT performance monitoring capabilities to ensure PNT services provide operational resilience and achieve safety-critical standards.
Dr. Mikel Miller, Vice President for PNT Technologies at Integrated Solutions for Systems (IS4S), former Air Force (AF) Senior Scientist (ST-00) for PNT Technologies for the AF Research Laboratory, and current program manager for USAF’s Resilient Embedded GPS INS (R-EGI) project, agrees that no one-size-fits-all GPS alternative solution exists and that the feds should play a role.
“While there are a lot of complementary PNT technologies out there,” says Miller, “many have not been employed because they are too difficult to integrate into existing proprietary systems. The biggest challenge is to build a dual-use open-systems architecture (OSA) with open, non-proprietary interfaces that sets the foundation for a PNT ecosystem. Folks are just starting to look at this now.”
This PNT ecosystem will enable 3rd-party developers to plug-and-play their applications and sensors into future PNT air, space, ground, or sea systems—which is directly in line with the Army’s Modular Open Systems Architecture (MOSA) approach.
According to Miller, who is also past President of the Institute of Navigation, the optimal solution may be for the government to own and maintain the integration architecture and allow industry to develop solutions to literally plug into it.
Not only has DOT distanced itself a bit from this RAND Report, incredibly, even DHS seems to have done so. Right up front, the RAND report states, “The results presented in this report do not necessarily reflect official DHS opinion or policy.”
As mentioned, the DOD did not contribute, nor has it not provided its own final assessment on PNT. Instead, the Government Accountability Office (GAO) has recently indicated that DOD needs to do more work to address PNT alternatives (reported online at insidegnss.com/usg-accounting-office-faults-defense-dept-efforts-on-alternative-pnt/).
In the meantime, it would be great if DHS, DOT and DOD would actually get together and provide one true joint assessment as Congress directed. Only then can we truly know whether or not there is something to see, when it comes to PNT, in terms of vulnerability and the need for backup.






