The National Institute of Standards and Technology (NIST) is building a new lab that will support work on securing the use of GPS signals.
“We are currently standing up a smart grid cybersecurity test lab, and one of our future research cases for later in this year or early next year, depending on when we finish building this lab, is GPS security,” said Victoria Pillitteri, an advisor for information system security at NIST, which is under the U.S. Department of Commerce.
The National Institute of Standards and Technology (NIST) is building a new lab that will support work on securing the use of GPS signals.
“We are currently standing up a smart grid cybersecurity test lab, and one of our future research cases for later in this year or early next year, depending on when we finish building this lab, is GPS security,” said Victoria Pillitteri, an advisor for information system security at NIST, which is under the U.S. Department of Commerce.
The work is getting under way just as news emerges that the U.S. Air Force is ramping up its cyber security efforts after what Brig. Gen. Kevin Wooton, director of communications and information at Air Force Space Command (AFSC), described as a “big” cyber threat. He told Space News recently that the impetus for the effort had evolved over time but was being spurred by one particularly “big” threat in 2013. He declined to give specifics on the threat.
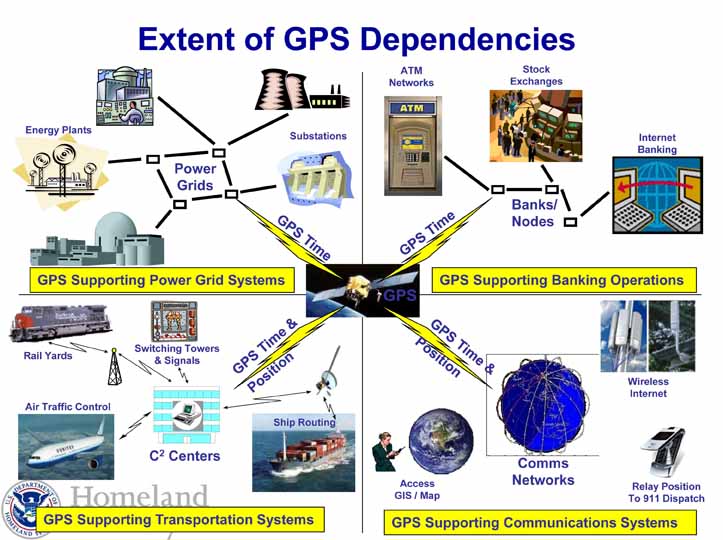
The loss of positioning, navigation, and timing (PNT) signals could be catastrophic to the nation’s power grid, communications network, and other infrastructure. In fact PNT is described as an interdependency that should be considered when assessing risk according to the 2013 National Infrastructure Protection Plan NIPP 2013: Partnering for Critical Infrastructure Security and Resilience
These kind of risks are what NIST wants infrastructure companies to weigh as they use NIST’s new cybersecurity framework. The White House launched the framework effort last February as part of Executive Order 13636, “Improving Critical Infrastructure Cybersecurity.
Issued just a year later on February 12, 2014, the framework sets out a step-by-step program for companies to evaluate their risks, put measures in place to detect and protect against attacks, and then, when attacks do occur, respond and recover as needed. The core of the framework has an extensive list of accepted industry standards for commercial security departments to use as references as they assess their efforts. Although its adoption is not mandatory, legal experts have cited the framework repeatedly as a potential baseline for determining liability when lawsuits are filed as the result of a cyber attack.
Raising PNT’s Profile
PNT, however, is not featured clearly in the plan – at least not yet.
“Anyone reading the 39 pages of the framework would not see PNT showing up,” said NIST’s Director Patrick Gallagher, during a February 19 panel on the framework at the Brookings Institution.
PNT is likely addressed in that core of references, said Gallagher.
“That’s got to be one of those examples of an issue that is imbedded in the standards sets that are in the core, because it points to a particular class of time-critical, position-critical data,” he said.
While the framework can be implemented by any organization, it is particularly aimed at those managing critical infrastructures like transportation and dams. The fact that positioning, navigation and timing is notably absent from the list of 16 critical sectors has been the subject of some criticism from members of the nation’s top PNT experts, the members of the National Space-Based Positioning, Navigation, and Timing Advisory Board.
Gallagher said he was not aware if the Department of Homeland Security (DHS) raised PNT as a specific issue during the period when NIST was putting together the top level of the framework’s structure. It may have come up during one of the workshops held when the framework was being crafted by NIST officials later, he said.
But, Gallagher underscored, the framework can become a way to communicate new information on threats and standards.
“The framework becomes a vehicle . . . for threat-informing the process,” he said. “If there really is a new class of vulnerability, that’s essential to critical infrastructure, particularly cross-sector like (PNT), we’re counting on DHS as a participant in that process to flag that and make sure that we take that back to industry as part of this process and make sure that the framework process doesn’t have that as a gap area. That is something that is explicitly addressed.”
DHS is not the only one empowered to point out areas that need to be addressed, said Dean Garfield, president and CEO of the Information Technology Industry Council. Under the presidential executive order federal agencies are expected to come back their with ideas about the framework. “I think that work is incredibly important as well, so it is not isolated to DHS or NIST but is cascaded broadly within the all the relevant agencies,” he told the Brookings audience.
NIST is beginning work to update the framework starting with a meeting in April on privacy issues. That will be followed in the summer with a meeting on another topic on another topic yet to be finalized.
One official suggested that PNT may be an issue for version 2.0 of the framework.
The matter may also come up as the 16 different sectors work to craft their approach to cybersecurity. For example, power grid experts who discussed the issue with Inside GNSS mentioned work on IEEE’s standard 1588, the standard for precision clock synchronization protocol for networked measurement and control systems, as well as annex K of 1588, which deals with security, as a possible area of effort.
As for the NIST lab, it is already under construction in Gaithersburg, Maryland.
Pillitteri added in response to the question on the security of PNT signals that the NIST team had recently met with a project manger at DHS who is working with MITRE to research security.
GPS security research is in the Science and Technology Division at the Department of Homeland Security, said Lisa Kaiser, a member of the DHS Cyber Emergency Response Team, who was on a panel with Pillitteri at the 2014 IEEE PES Innovative Smart Grid Technologies Conference in Washington.