Table 2: Cooperative GNSS Authentication
Return to main article: “Cooperative GNSS Authentication”
By Inside GNSSReturn to main article: “Cooperative GNSS Authentication”
By Inside GNSS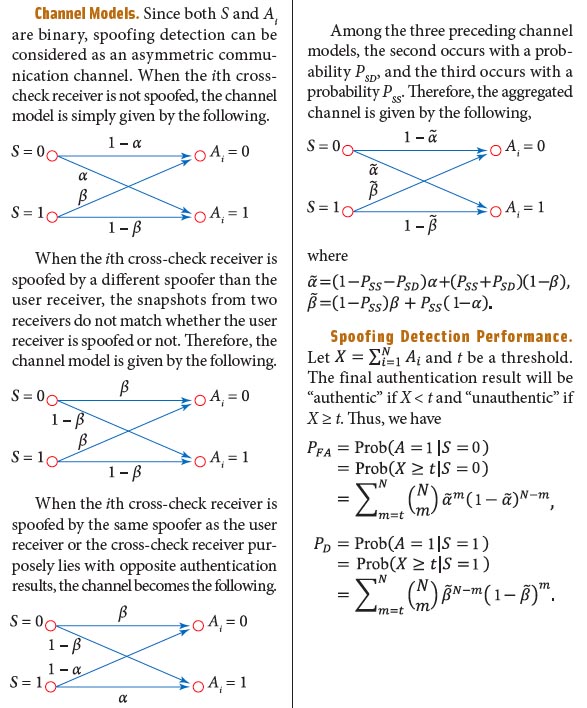 Equations
EquationsDuring the past two decades, the Global Positioning System, together with other GNSSes, has become an essential element of the global information infrastructure, with myriad applications in almost every facets of modern businesses and lifestyles, including communication, energy distribution, finance and insurance, and transportation. Ever-growing dependence on GNSS creates strong incentives to attack civil GNSS, for either an illegitimate advantage or a terrorism purpose.
By Inside GNSS Kalman state update equation
Kalman state update equationNavigation — if you are reading this magazine, you almost certainly have some level of interest in navigation technology, which has seen an incredible explosion in use within many different fields.
By Inside GNSSReturn to main article: "Adding Intelligence to Receivers"
By Inside GNSSReturn to main article: "Adding Intelligence to Receivers"
By Inside GNSSReturn to main article: "Adding Intelligence to Receivers"
By Inside GNSSReturn to main article: "Adding Intelligence to Receivers"
By Inside GNSS