Authentication is an essential problem in the field of communication: confirming that a pretended identity of a user or transmitted information does, in fact, really correspond to the true identity or source.
Authentication is an essential problem in the field of communication: confirming that a pretended identity of a user or transmitted information does, in fact, really correspond to the true identity or source.
In the context of a face-to-face conversation, we can authenticate the communication by recognizing the voice and the look of one’s conversational partner. A letter can be authenticated by identifying the handwriting of its sender, and in small, wired local area networks the originator is apparent by following the cable connections. This situation changes fundamentally in the scope of modern communication over wide area networks or radio links.
Circumstances also vary the importance of authentication. We may not care that the author of a cooking recipe is indeed Paul Bocuse, as long as the ingredients and preparation instructions produce an excellent meal. On the other hand, it is important to know that the originator of an application for payment is indeed the plumber who repaired the toilet or the electrician who installed the new light fixtures.
Even more important is authenticity in matters of safety- and security-related information. For example, in the handling of a railway level crossing, system operators must be assured that only the signalman is able to raise the gate.
Authentication in GNSS
In the context of satellite navigation systems, the transmission of information takes place over radio links — by their very nature, an insecure data channel.
GNSS communications contain several areas of concern regarding the confirmation of the origin of a message and/or the identity of its sender. In matters involving user segment data links, two different kinds of authentication issues arise: first, confirmation that a navigation signal actually originates from the indicated satellite and, second, proof that the user receiver is authorized to make use of the signal.
Both proofs of identity are relevant for the security of military applications of GPS. On the one hand, it must be assured that a potential foe is not able to gain any benefit from the system, for example, by aiding the navigation of the foe’s cruise missiles with GPS signals. On the other hand, authorized GPS military users need to guarantee that misrouting of one’s weapons by means of spoofed signals does not occur.
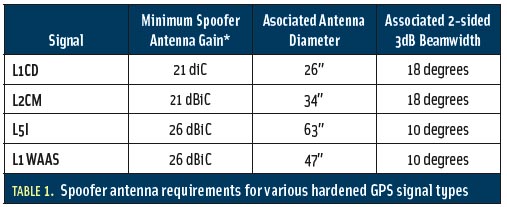
Spoofing denotes the misguiding of users by means of forged signals and manifests itself as an error source in both military and civil GNSS applications. In safety-critical civil realms such as aviation, detection of forged signals must be reliable. . .
(For the rest of this story, please download the complete article using the PDF link.)