Laboratory tests explore how commercially available receivers respond to meaconing and spoofing, with the goal of developing useful test methodologies and metrics to assess receiver robustness and resilience to real-world spoofing threats.
Commercial GNSS receivers display a range of responses to simulated GNSS spoofing attacks performed in laboratory conditions. Receivers can sometimes behave in a confusing manner or even cease working altogether in the presence of counterfeit constellation signals, even though the receiver is not fully spoofed by the signals.
The tests were undertaken in two major parts: three commercially available receivers were presented with a very simple meaconing/replay example, and subsequently were subject to GPS spoofing at ranges of 10m, 50m and 100m. During the spoofing attacks, the power of the replica (counterfeit) GPS signals was gradually raised and then lowered. During the simulated GPS spoofing scenarios, the horizontal position error (HPE) and root mean square (RMS) of the residuals were closely monitored for each of the receivers.
The definitions of “resilience” and “robustness” as widely used in the field of protection of critical infrastructure can also be applied to GNSS spoofing, where the two terms are not necessarily equivalent. Defining these terms separately can lead to some advantages in defining meaningful test metrics.
We present a generalized approach to defining meaningful, comparable test metrics that can be used to evaluate the performance of GNSS devices to spoofing. There is a clear need to understand and mitigate known vulnerabilities in a timely manner in the commercial sector to prevent so called “zero-day exploits.” Finally, we discuss how the proposed spoofing test frameworks could be expanded and used to drive significant improvements in the assessment of safety or liability critical systems performance.
The Need
The cost of the equipment needed to carry out a spoofing attack has fallen significantly over the past few years and new technology—programmable software defined radios (SDRs)—have also become available. The expertise required to carry out a spoofing attack has also decreased with much of the code required to program a SDR to act as a GNSS signal transmitter becoming widely available on the internet.
Nation states have also acquainted themselves with the application of GNSS spoofing.Iincidents of GPS spoofing have occurred around the world and several high-profile incidents have been reported, namely the spoofing of commercial shipping in the Black Sea and the “circular” spoofing of shipping near the port of Shanghai. Under many of these threat scenarios it is not just the targeted receiver that is affected by the attack. Whilst we have seen much in the way of anecdotal data on the impact of spoofing on commercial receivers, quantitative data relating to the impact of spoofing on commercial GNSS receivers is not widely available. As the chances of encountering a spoofing signal steadily increase there is a need to understand how receivers will respond to the types of threat they will typically encounter.
GNSS Spoofing
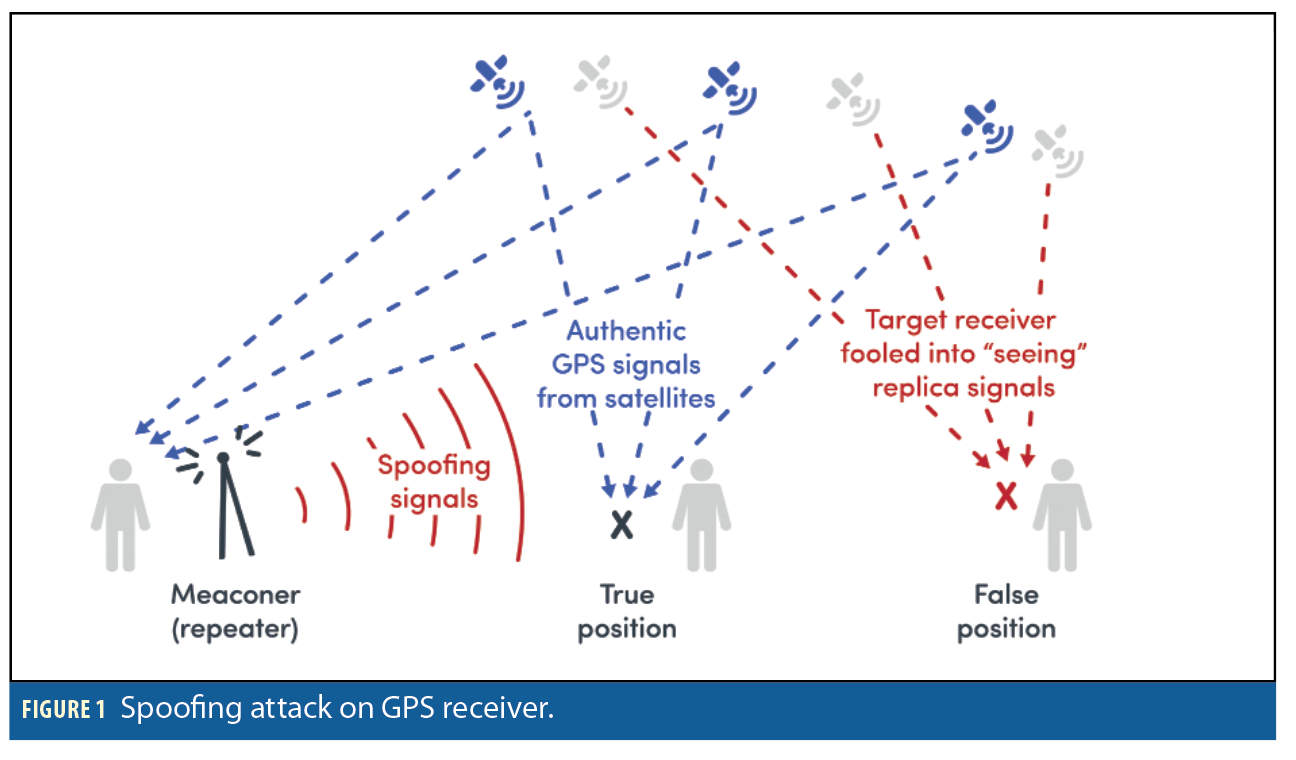
Figure 1 shows an example GNSS spoofing attack on a receiver with the goal of forcing it into generating a false position report. If the target receiver has no protection against spoofing attacks, and if the attacker initially manages to align the replica signals accurately with the position of the target receiver, the receiver will lock on to the fake signals and can then be steered by the attacker to appear as if it were in a false position. As well as determining the position of the target receiver, the attacker has to ensure that the transmitted signals will arrive at the target receiver with a reasonable power level.
A spoofing attack could also be mounted to disrupt timing services too (without moving the position of the target receiver) so quantitively understanding the impacts of spoofing attacks on commercial receivers with and without protection becomes essential. For this series of tests the spoofed (false) position corresponds with that of the spoofing source.
Test Methodology
Three representative commercial GNSS receivers in wide use today have been anonymized for this study and are named as Receiver A, Receiver B and Receiver C. Tests also employed receiver user interfaces to monitor receiver response and log NMEA messages.
For all simulated spoofing scenarios a simulator generates simulated live-sky GNSS signals as well as the spoofing signal. In live-sky scenarios, the simulator provides the spoofing signal, and authentic live-sky signals from a roof-mounted antenna are combined with the spoofer signals from the simulator. All testing was carried out as conducted tests in a closed laboratory environment.
Scenario
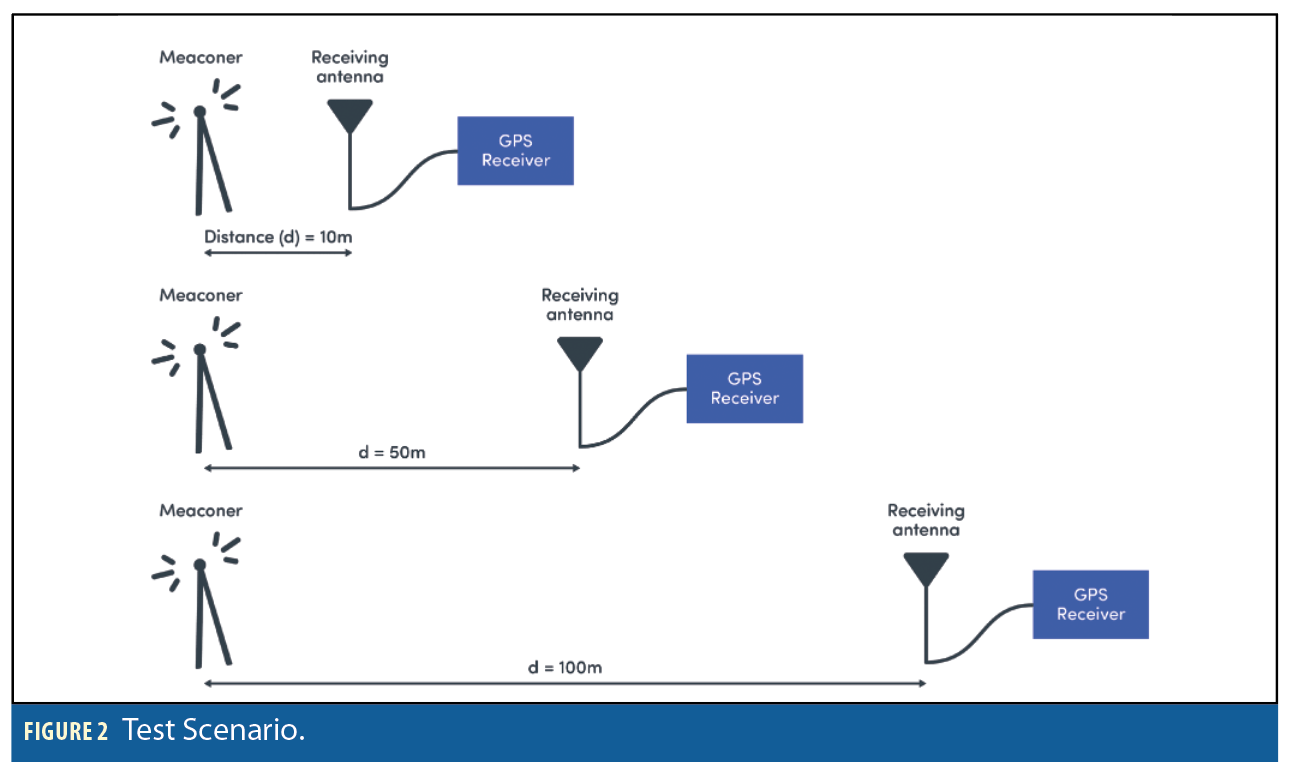
The three sample GPS receivers under test were subject to the following spoofing scenario which simulated a GNSS repeater (meaconer) at a distance of 10m, 50m and 100m from the truth position (see Figure 2).
The spoofing signal is subject to a power ramp throughout the scenario. For the first 15 minutes the meaconer is not active. This allows the receiver under test to acquire and track satellites and to settle into a stable operating regime. When the spoofing signal is activated, it is slowly increased by 1dB every minute until it reaches a maximum power level of –118.5dBm. There is a 5-minute period with power levels of the spoofer set to maximum. The power level is then reduced back to the starting conditions gradually. Following this the receiver is allowed to settle again for a period of 15 minutes with no spoofing signal before being subject to a second spoofing attack with power ramped up by 1dB every minute up to the same –118.5dBm level.
Results
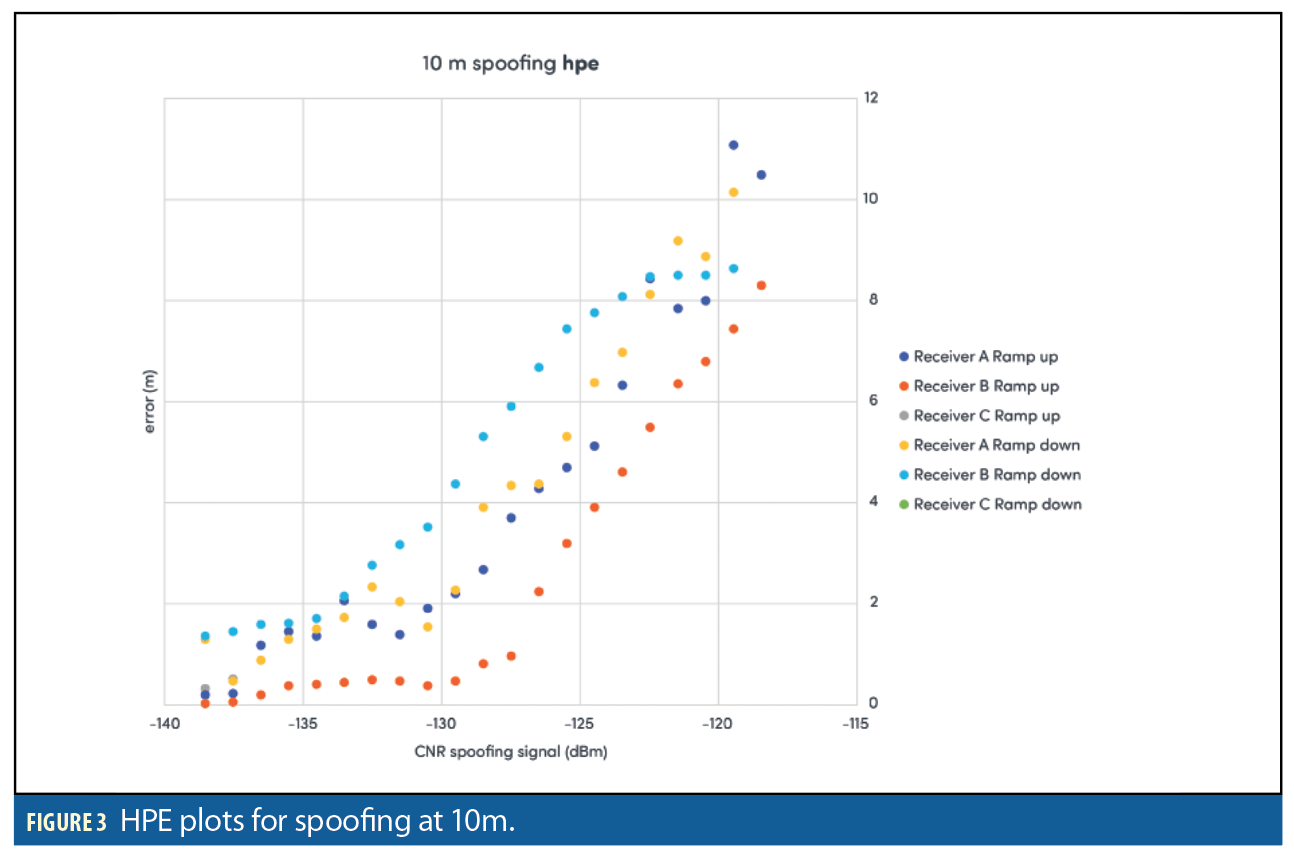
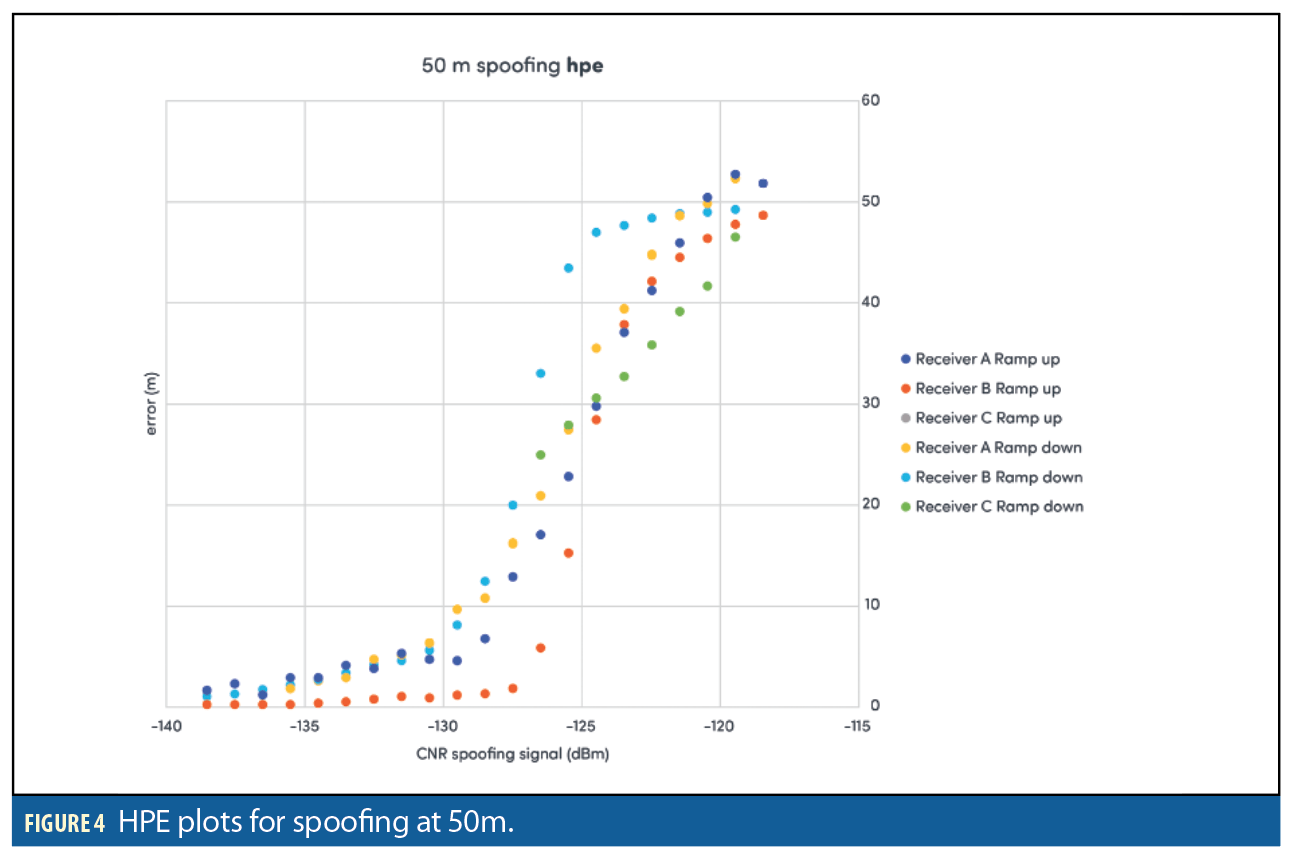
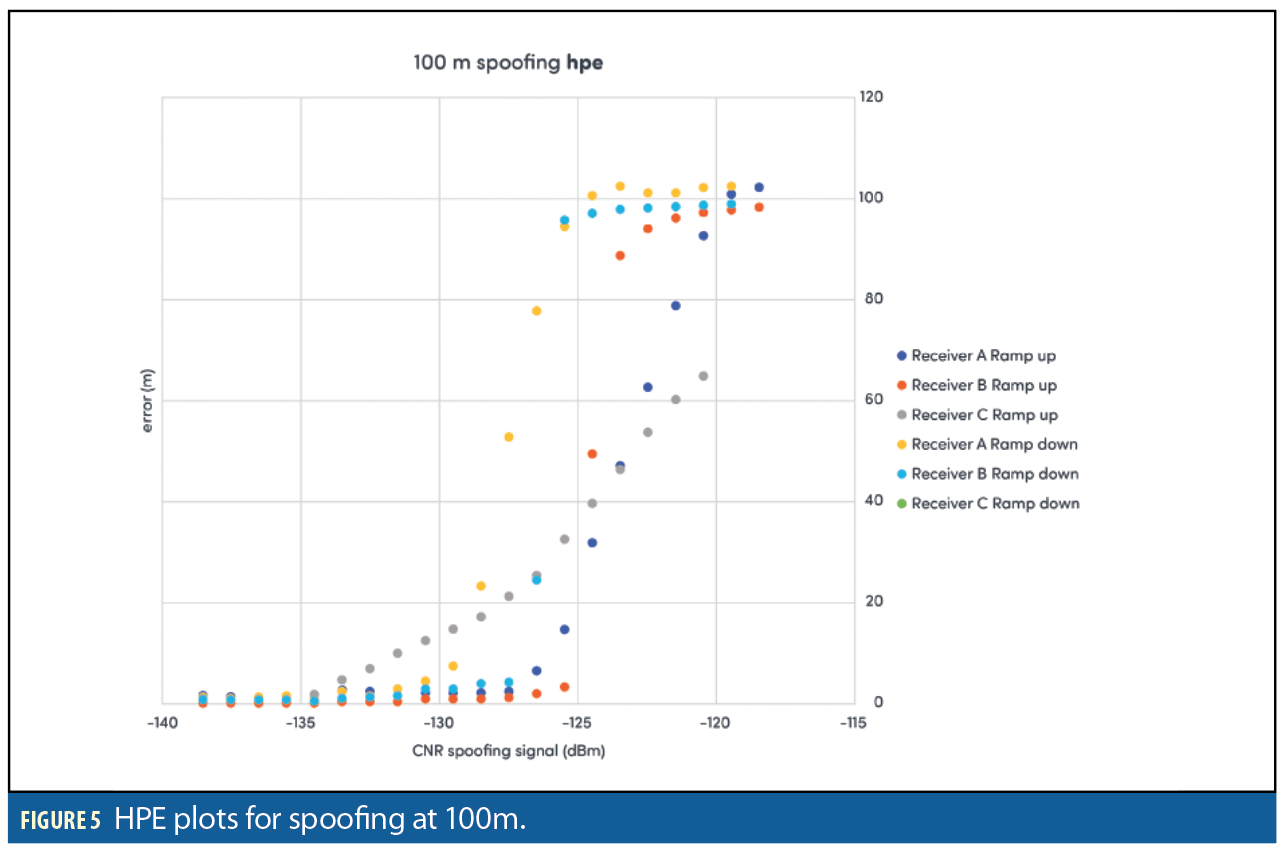
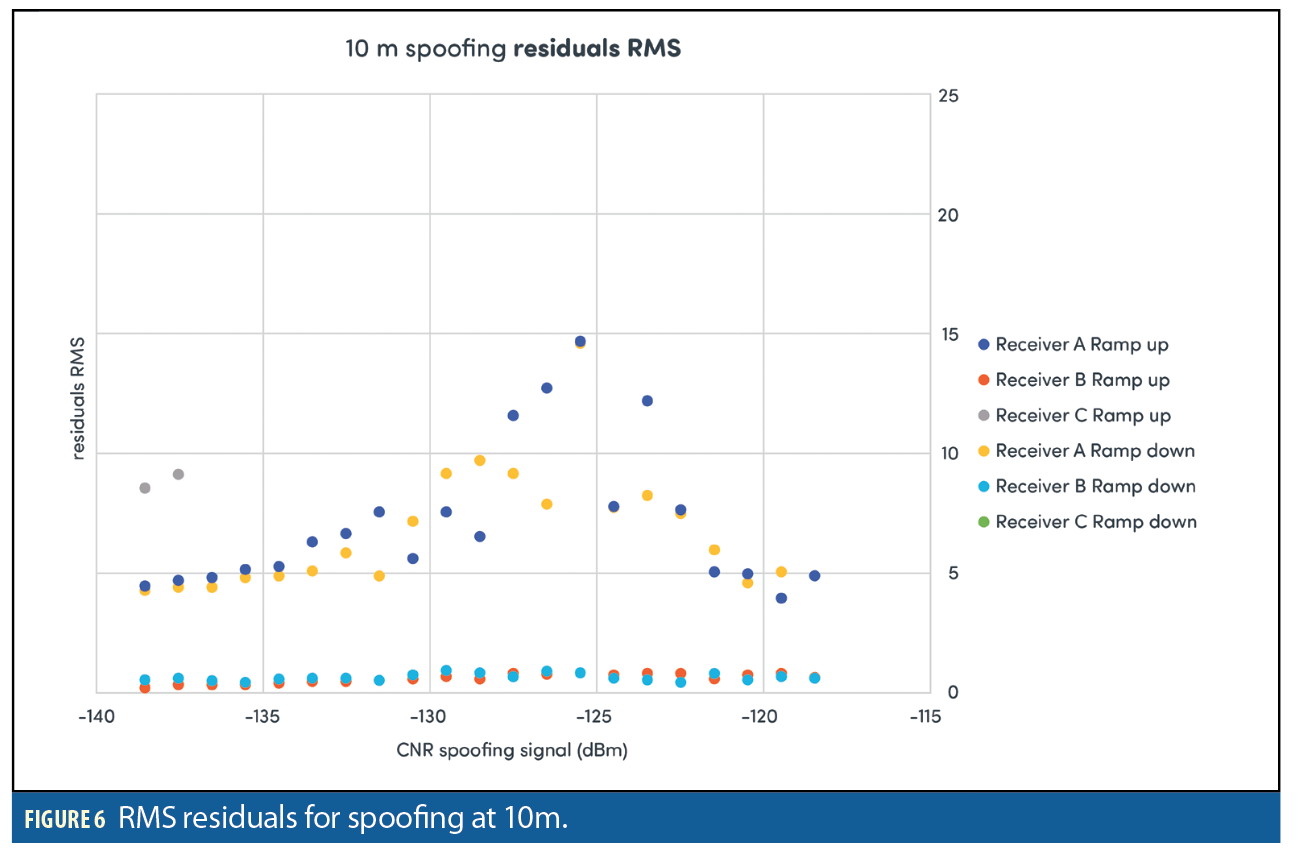
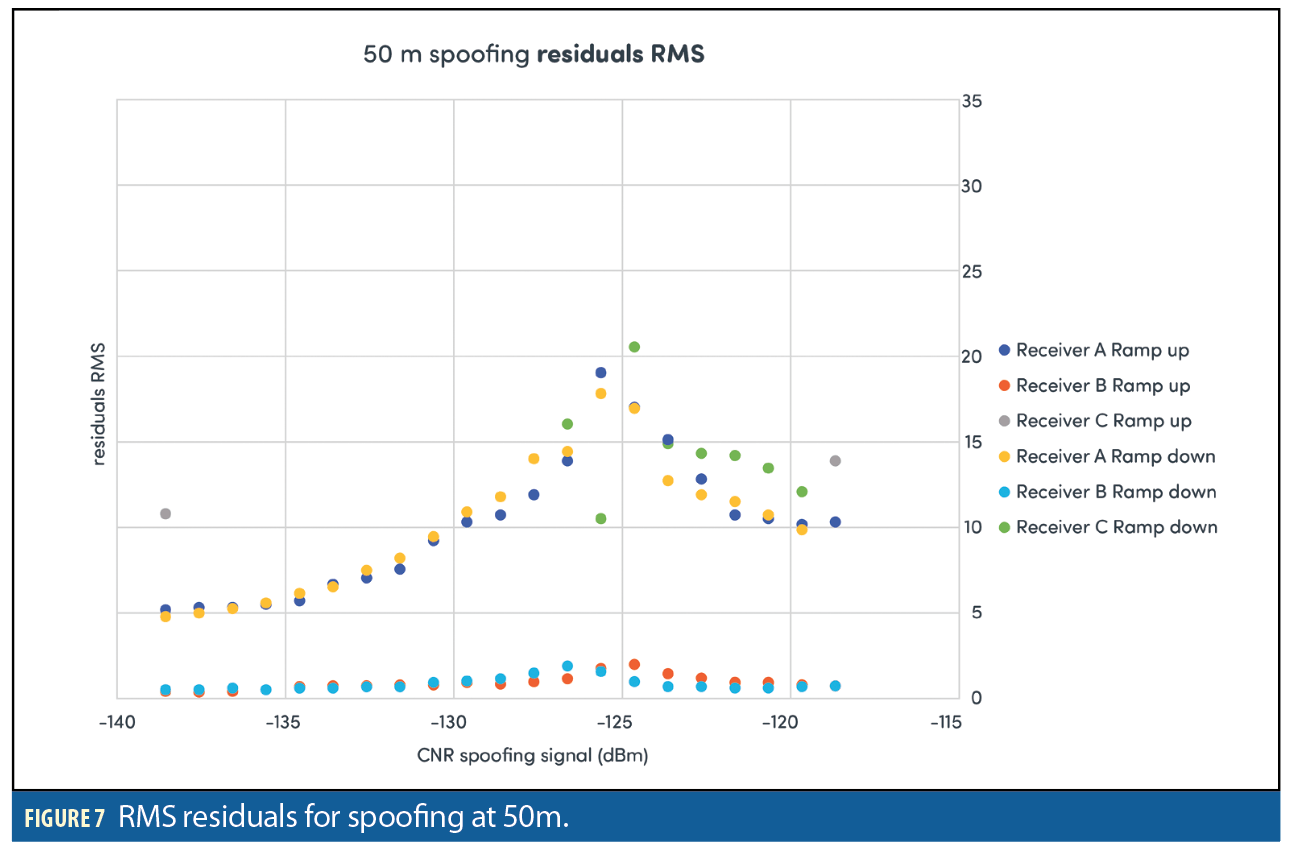
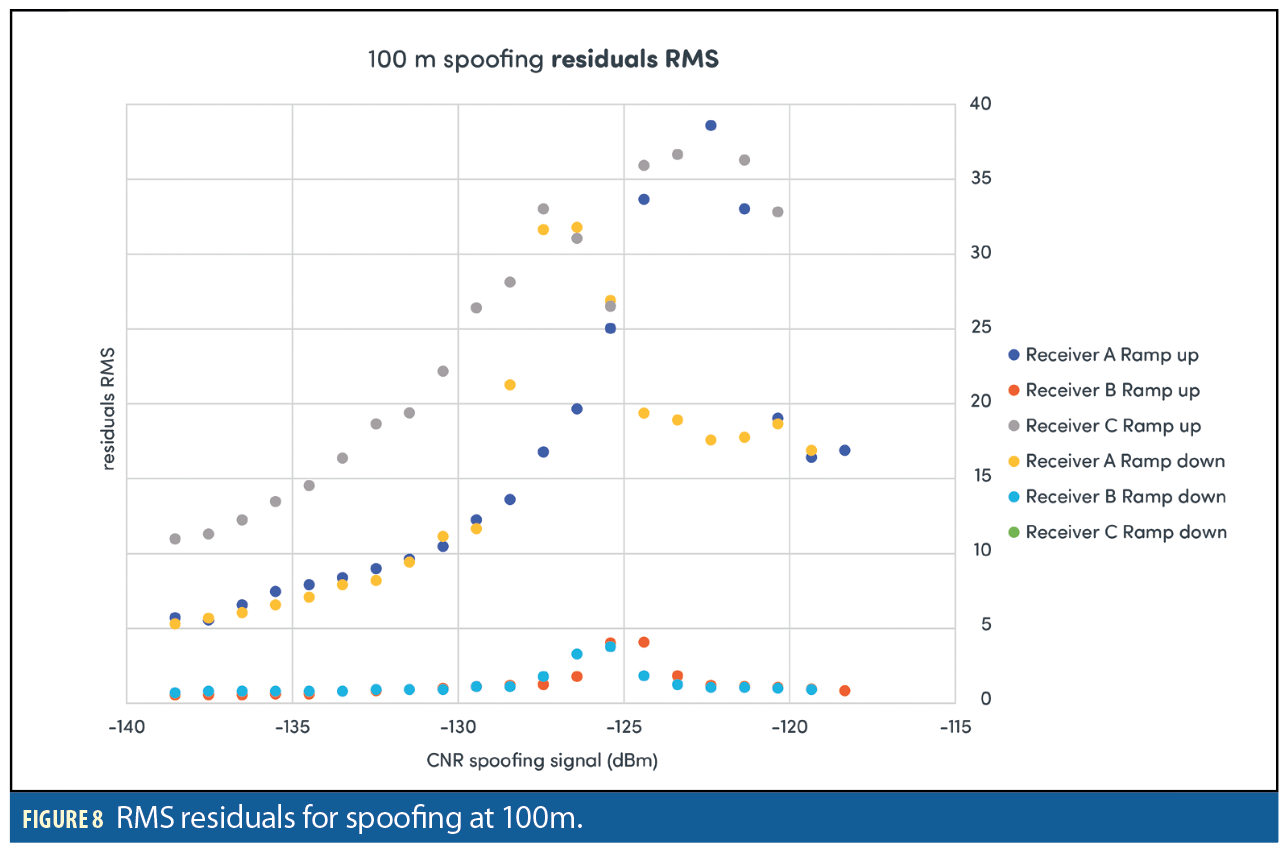
Figures 3–8 show results for the first spoofing attack (first power ramp and power reduction). The plots show HPE and also the RMS residuals for all three receivers. Data recorded from the second ramp-up of spoofer power levels is not shown for reasons of space. The data is in fact very similar to the data recorded from the initial power ramp.
Discussion
The main aim of this paper is to examine the suitability of this type of scenario as a benchmarking test, rather than to provide insights into the behavior of the receivers under test. However it can be seen that even when subject to a simple and non-dynamic spoofing scenario used here, the three sample receivers exhibited markedly different behavior. The results also show that the degree to which a receiver can withstand an attack does not necessarily correspond to the degree which a receiver recovers to its original operating state following an attack. Receiver C struggled with the scenarios, often quickly losing lock on the authentic signals and starting to report erratic HPE data. It also often failed to recover completely on ramp down, not locking onto any transmitted signals regardless of their authenticity.
The two other receivers show correlation between the point at which the HPE transitions from minimum to maximum as the spoofer power is ramped up, or vice-versa when the spoofer power is ramped down.
The peak in RMS residual appears to flag the point where the solution begins to be dominated by spoofing signal. If the attack is not detected via the RMS residuals than this does not happen. Note that Receiver B performs significantly better than Receivers A and C at all ranges when it comes to RMS residuals with much lower values consistently although small peaks in the RMS values can be observed on the 50 and 100m distance runs. Also note that when the power of the spoofer is ramped down, a peak in RMS residuals is also observed at the point where the truth signal again becomes dominant.
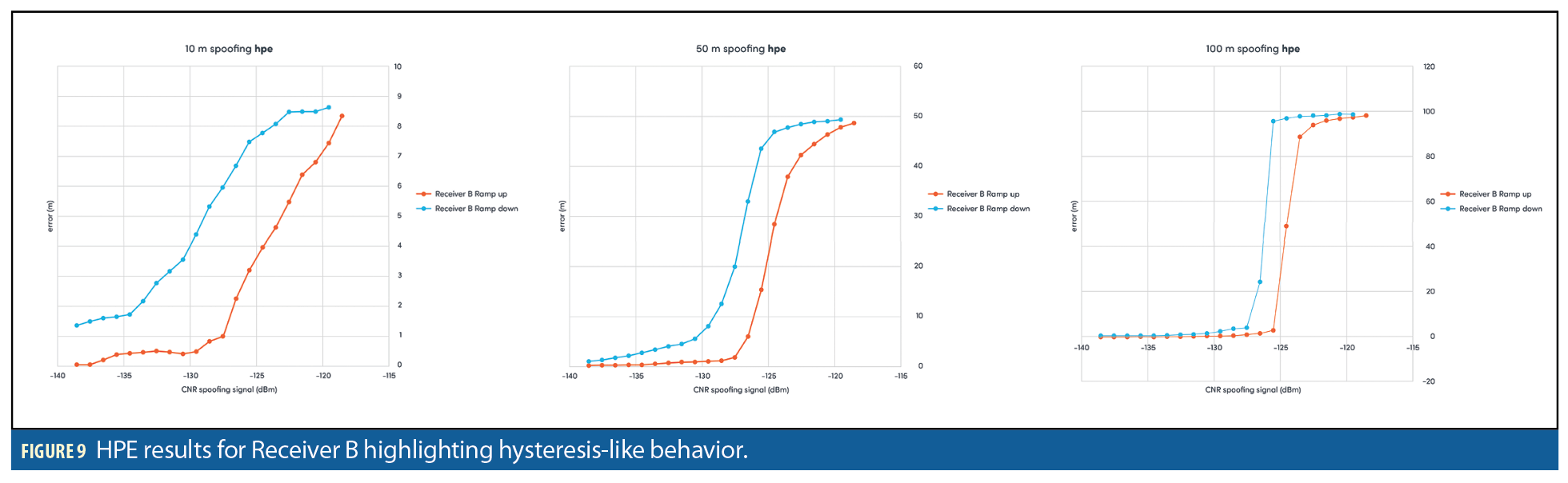
Also striking is that at least one of the receivers in these scenarios appear to exhibit hysteresis-like behavior. Figure 9 shows the HPE response of Receiver B when subject to the ramp-up and ramp-down in power level of the spoofing signal. Hysteresis is often defined as the dependence of the state of a system on its history, and so this is perhaps suggestive of a software-dependent issue to do with output (position) noise reduction. The lack of any similar evidence of hysteresis in the RMS residual plots probably back that up. Receiver B exhibits similar hysteresis in the scenario at both of the other distances (10m and 50m).
These particular scenarios were performed under ideal benchmarking conditions: the alignment of simulated “live sky” and spoofed signals is almost perfect and there are no environmental variables to consider with the spoofer and receiver in fixed locations. For a scenario designed to evaluate the degree of robustness and resilience of a selection of receivers against a spoofing attack, there is much to recommend this approach, even though the scenario is not typical of real world conditions. In the real world, alignment of spoofer signals with the authentic live sky signals in the target receiver correlators does not always occur. Further, if the spoofing episode is a malicious attack, the attacker will generally find it more difficult to conduct an attack with a high probability of success, especially if there is relative motion between the spoofing source and target system. However it is still important to assess the robustness/resilience of systems against the effects of spoofing, and to understand and document any unexpected system behavior.
Conclusions
Observing the RMS residuals of a receiver during a spoofing attack can provide a good indication as to whether a receiver is spoofed or not. All of the three commercial receivers tested here showed consistently that a peak in RMS residuals occurs when the power of the spoofer reaches the point at which the receiver cannot differentiate between authentic and replica signals. If the power of the spoofer is increased still further the RMS residual values are seen to decrease to normal values, but this is a consequence of the receiver tracking the spoofed signals. The monitoring of RMS residual values could be a promising means of detecting spoofing attacks in a receiver.
The scenario used in these tests was a very simple example of meaconing, with spoofer and receiver under test static, zero time delay added to the meaconer, and both the live-sky and spoofer signals generated by a single GNSS simulator. However the responses of the receivers to this scenario shows that very small variations in the parameters of a spoofing attack can induce a large response in the target receiver. The results may be used to help evaluate the robustness and resilience of receivers to a spoofing attack
It is often much harder to spoof a GNSS receiver in real life than it is when carrying out simulated testing. This is due to spoofing signal alignment and other environmental variables such as multipath aiding the defender in this regard. These tests evaluated the performance of receivers against a perfectly aligned spoofing attack, that is, a worst-case attack for the receiver. Whilst this is irrelevant from the point of view of developing a spoofing benchmark test for commercial receivers, more work needs to be undertaken on the spoofing of commercial receivers receiving authentic live-sky GNSS signals in order to understand the factors that affect successful spoofing of receivers in real-world conditions.
Resilience and robustness are terms that are often used interchangeably in the PNT community, sometimes with definitions that overlap. These initial spoofing studies indicate that a receiver’s resilience to spoofing may not equate to its robustness. Further work needs to undertaken to look at whether there are significant differences and whether a test framework for GNSS receivers should incorporate separate assessments of the resistance to a spoofing scenario and the ability of a receiver to recover to its original state, having been subjected to a successful spoofing scenario.
This work also emphasizes that it is essential that any discovered attacks are reported in the commercial sector so that effective mitigation can be put in place. Responsible disclosure of major vulnerabilities can only help the PNT community to protect users.
Manufacturers
Tests were conducted with a Spirent GSS7000 Radio Frequency Constellation Simulator (RFCS).
Acknowledgment
The material in this article is based on a paper presented at ION GNSS+ Virtual 2020, “Assessment of GNSS Receiver Behaviour in Laboratory Conditions When Subject to Meaconing or Spoofing Scenarios.” Readers are referred to ion.org/publications/browse.cfm for the complete version.
Authors
Francesca Filippi is a student in Electrical and Electronic Engineering (MEng) at Cardiff University. She worked for Spirent Communication as professional services staff member during her university placement year.
Mark Hunter is head of the Professional Services team at Spirent Communication. He has worked for the company as an applications engineer and in other roles in both the U.S. and the UK. He received an honors degree in electrical engineering from Brunel University.
Guy Buesnel is a PNT security technologist, robust position, navigation and timing, with a research interest in PNT systems cybersecurity. He holds a MSc (Eng) in Communications Engineering from the University of Birmingham and is a Fellow of the Royal Institute of Navigation.