Q: What do we know about recent observations of GNSS interference and spoofing in Eastern Europe? What lessons can we learn regarding civil user mitigation of these threats? What can we learn from recent incidents and their impact on civil aviation?
ZIXI LIU, SHERMAN LO, JUAN BLANCH, YU-HSUAN CHEN, TODD WALTER AND SAM PULLEN, STANFORD UNIVERSITY
A: GNSS serves safety-of-life applications in aviation (e.g., precision approach and landing operations), land vehicles and marine users. One threat to these applications is radio frequency interference (RFI). A variety of RFI events affecting GNSS signal bands have been observed over the many years of GNSS usage [1]. RFI leading to unexpected loss of GNSS navigation forces reliance on backup sensors and operational modes. While this is tolerable if sufficiently rare, equipping and planning for these events increases the cost and complexity of safety-critical navigation. Spoofing of GNSS signals also has been observed in the last few years and is more worrying because it could cause GNSS to output hazardously incorrect information and thus pose a direct threat to user safety.
Since the Russian invasion of Ukraine in February 2022, RFI and spoofing that appears to be both intentional and malicious has been observed in Eastern Europe [2, 3]. Most Western observers believe the Russian military is the source of these events, and its purpose is primarily military [2, 4]. However, these events also affect civil users and pose hazards that might not be intended but are no less real. This article examines what we have observed from recent RFI and spoofing in Eastern Europe, how it has affected civil aviation, and lessons for civil user safety and operational efficiency.
Observation Using ADS-B Messages
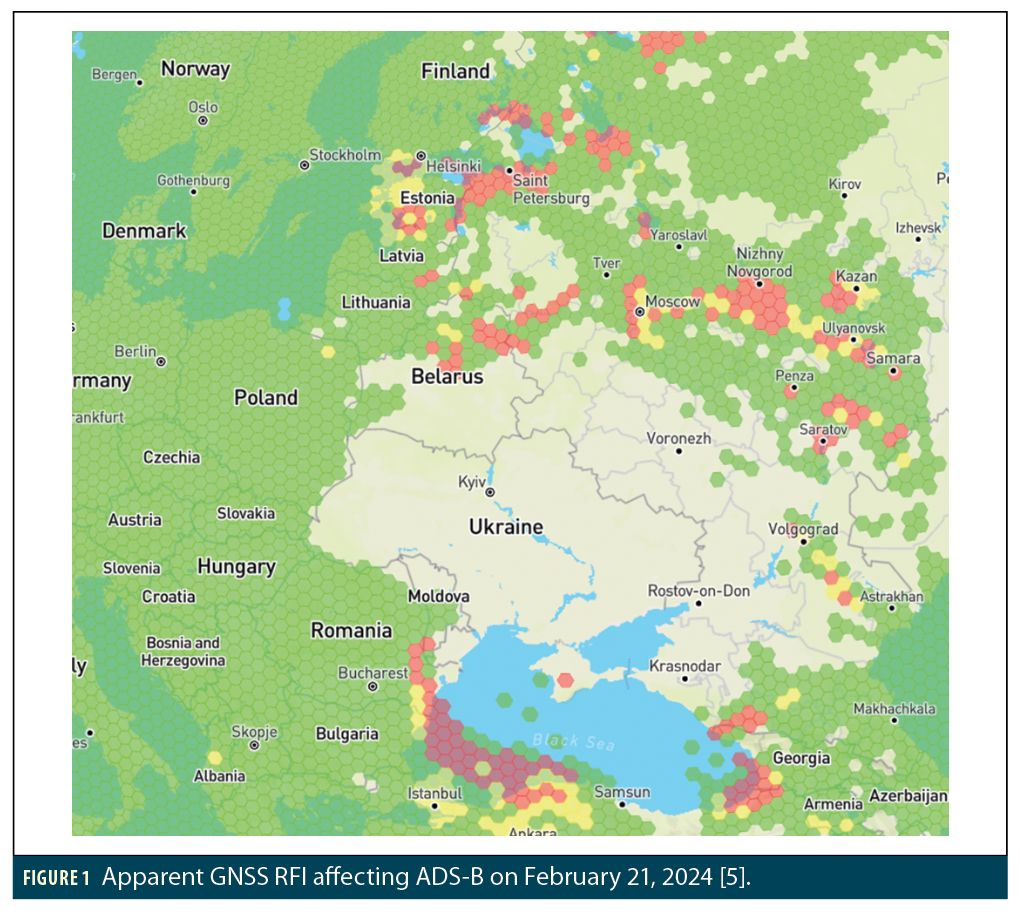
Automatic Dependent Surveillance (ADS)-B messages broadcast by aircraft are an important source of information regarding the timing and effects of GNSS RFI, and this information is now readily available online (e.g., at GPSJam, managed by John Wiseman [5], which uses data from ADS-B Exchange [6]). Figure 1 from [5] shows an example view of GNSS RFI affecting ADS-B on February 21, 2024. The colors on the map indicate regions where at least 98% of aircraft report good ADS-B accuracy (green), where between 90% and 98% of aircraft report good accuracy (yellow), and where fewer than 90% of aircraft report good accuracy (red) based on the NACp parameter defined below. The locations in red on this map have seen frequent GNSS RFI and spoofing events.
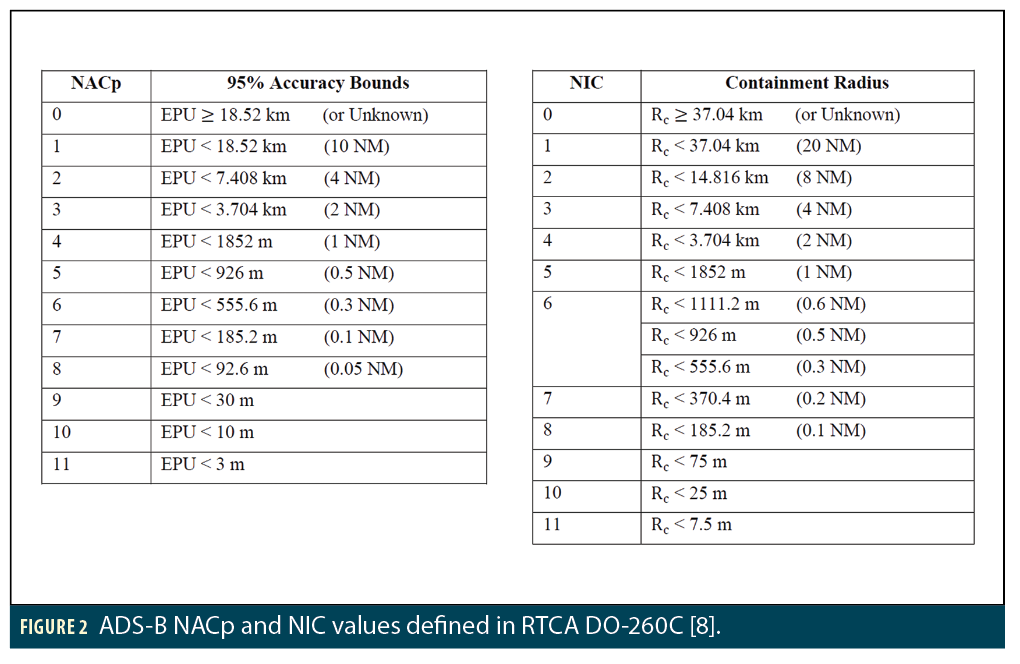
Our research also uses data collected from the OpenSky network [7] and ADS-B Exchange [6]. It contains GNSS-derived position information from aircraft along with built-in accuracy and integrity indicators known as Navigation Accuracy Category—Position (NACp) and Navigation Integrity Category (NIC), which provide the transmitting aircraft’s estimate of its GNSS position quality. NACp gives the 2D horizontal error radius that is expected to bound the current horizontal position error with a probability of 95%, while NIC does the same for the much higher probability of 99.999%, meaning that no more than one error exceeding this radius should occur in 100,000 samples.
Figure 2 shows values for both NACp and NIC as defined by the RTCA ADS-B MOPS (DO-260C) [8]. Note that higher integer values correspond to smaller error bounds and thus better performance. The ADS-B equipment performance requirements defined in [9] state that, under normal circumstances, aircraft NIC values must be 7 or higher. As shown in Figure 2, a NIC of 7 corresponds to a horizontal containment radius of 370.4 meters, while a NACp of 7 corresponds to a 95% horizontal error bound of half that (185.2 meters). These error magnitudes are much larger than would be expected of the GPS Standard Positioning Service (SPS) under anything close to “normal” conditions [10]. Thus, NIC values lower than 7 suggest an anomaly is present, of which RFI denying GNSS service is the most likely cause in locations where we have already determined that RFI is occasionally present. While this information from ADS-B does not directly observe the presence of RFI, it shows the impact on civil aviation of the RFI that is present.
RFI Events in the Baltic Sea Region
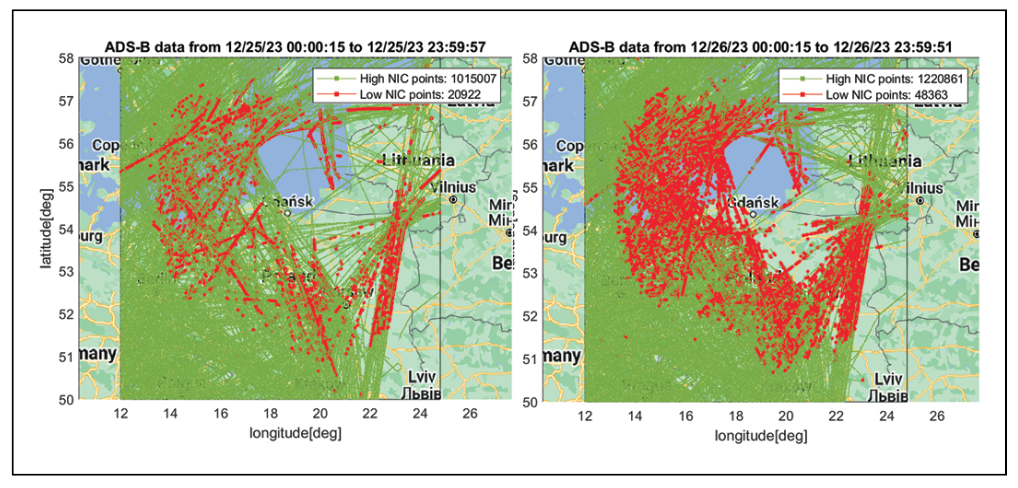
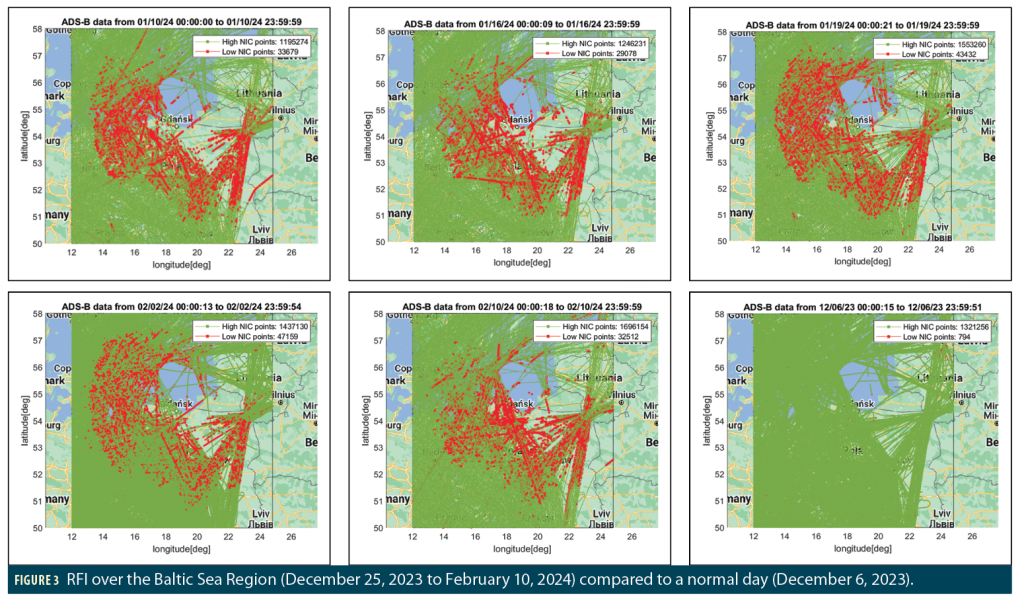
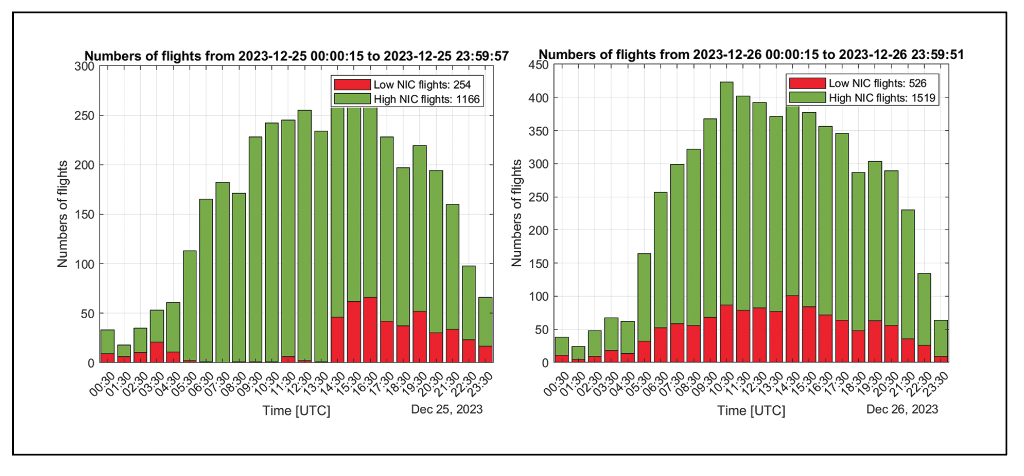
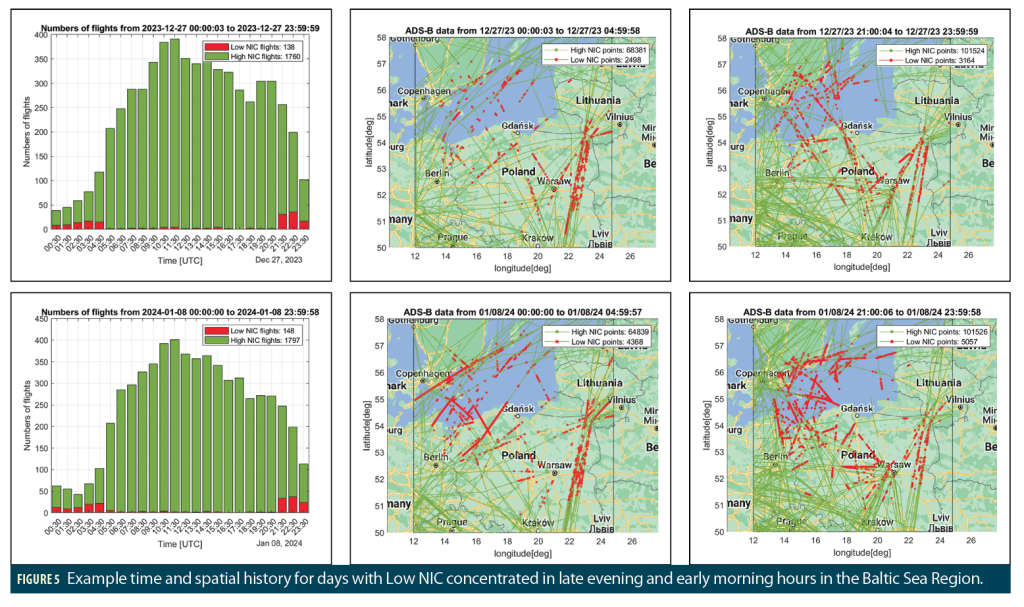
An increase in interference to GPS signals in the Baltic Sea region was observed to begin on December 25, 2023, and is continuing at the time of writing. Figure 3 shows examples of significantly affected days in which ADS-B messages suggest the presence of high-powered RFI. Each map shows the reported locations of aircraft sending ADS-B messages over the course of a day from midnight-to-midnight UTC. Most of these points have NIC values of 7 or higher (“High NIC”) and are shown in green, while the smaller set of points with NIC below 7 (“Low NIC”) are shown in red. As explained earlier, the points in red have containment radii far above typical for GPS SPS, suggesting the presence of RFI. The red points extend over a large region centered on the southern shore of the Baltic Sea from Gdansk (Poland) eastward to the Lithuanian border and include the Kaliningrad Oblast of Russia isolated between Poland and Lithuania. The lower-right map in Figure 3 shows an earlier example day (December 6, 2023) that appears to have little or no RFI for comparison. The handful of scattered red points on this map suggest temporary navigation problems unique to particular aircraft.
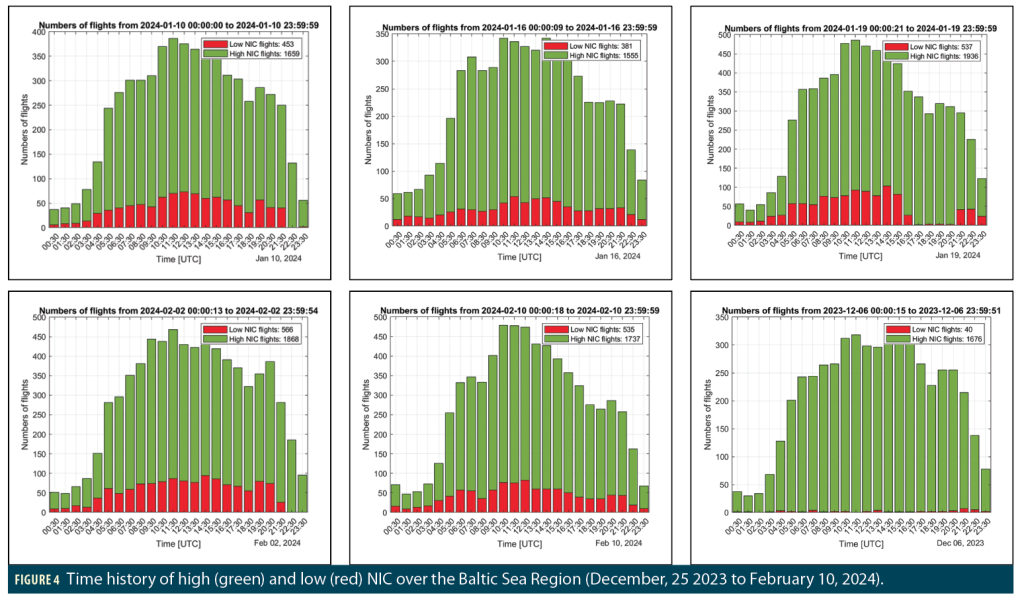
Figure 4 shows bar charts of the number of High NIC (green) and Low NIC (red) samples during each one-hour interval for the same days shown in Figure 3. While some of these days (e.g., January 10 and 16 2024) have fractions of Low NIC observations that remain similar throughout most of the day, others (e.g., December 25, 2023, and January 19, 2024) have higher Low NIC ratios at different times of day (late afternoon on December 25, morning on January 19). These patterns, along with different behavior on different days, suggest the RFI causing these observations is tuned to specific activities and is not unintentional (which might cause it to be active continuously). Note the times indicated on the x-axis are in UTC, which is one hour behind local time in Poland and two hours behind in Lithuania and Kaliningrad.
We have looked at all days between December 25, 2023, and February 10, 2024, and found some spatial and temporal characteristics related to the Baltic disruption. First, most of the days were only affected during early morning (0000-0500 UTC) and late evening (2100-2400 UTC). Only some of the days shown in Figures 3 and 4 have been affected for almost the entire day. This further suggests the motivation for this RFI could potentially be related to underlying (possibly military) activities limited to those hours or those days. Second, most of the jammed days have similar affected regions in terms of size, shape and location. Figure 5 shows similar maps and bar charts for some example days with those characteristics.
Localization of Baltic Sea RFI Events
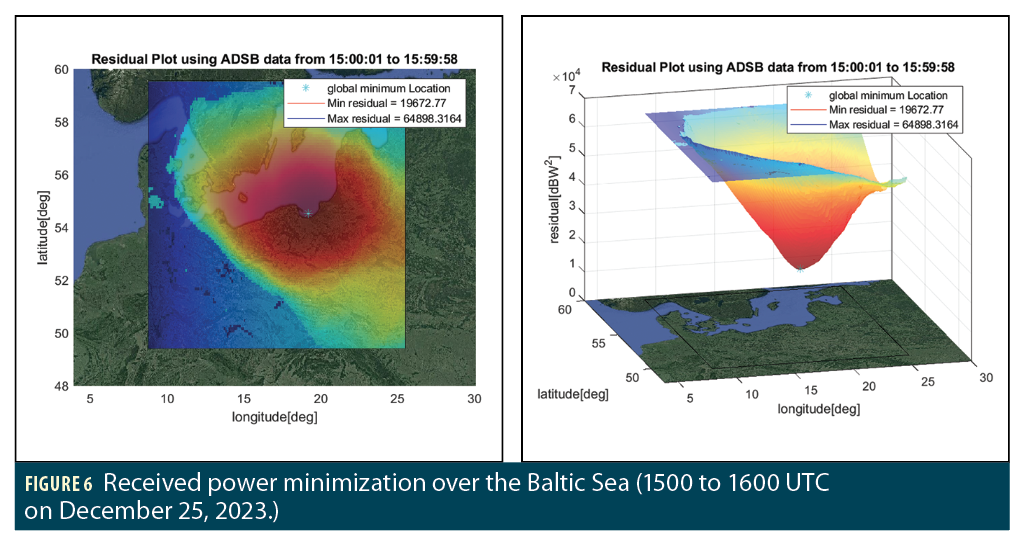
We have developed RFI transmitter localization techniques based on modeling the relationship between ADS-B reported NIC and received jamming power and then using iterative non-linear least-squares to estimate the location where the jamming is strongest (i.e., received GNSS signal weakest) given the locations of the reported NIC values [1, 11, 12]. This method relies on the assumptions of free-space propagation and that the source is a static, continuous, single element, omni-directional antenna. Figure 6 shows a preliminary localization result over the Baltic Sea region between 1500 and 1600 UTC on December 25, 2023. A smooth gradient in estimated power appears on these plots and indicates a minimum near the southern Black Sea coast between Gdansk and Kaliningrad.
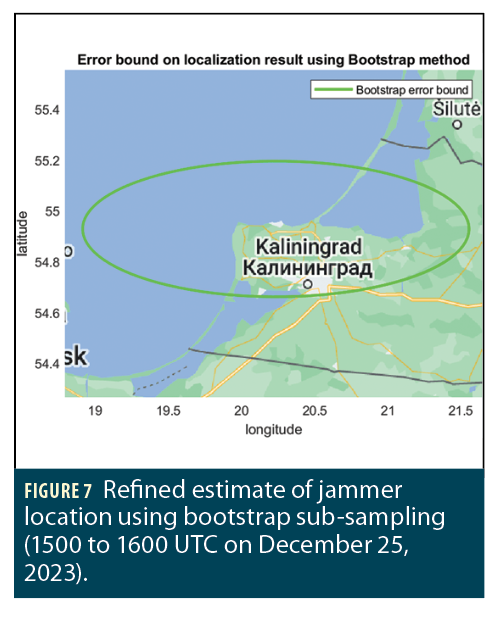
The uncertainty in this initial jammer location estimate can be refined by using “bootstrap” sub-sampling of the ADS-B data and by using data from a day where Low NIC observations are limited to a smaller region around the minimum-power location shown in Figure 6 (January 4, 2024, from 0500 to 2100 UTC). Figure 7 shows a map that, based on data from this day, includes an ellipse with a 95% probability of including the actual jammer location. The overland component of this ellipse includes the Kaliningrad Oblast of Russia, which is the headquarters of the Russian Baltic Fleet and is known to have an extensive array of modern Russian weaponry, including the latest aircraft and missiles [2].
Spoofing Events in the Black Sea Region
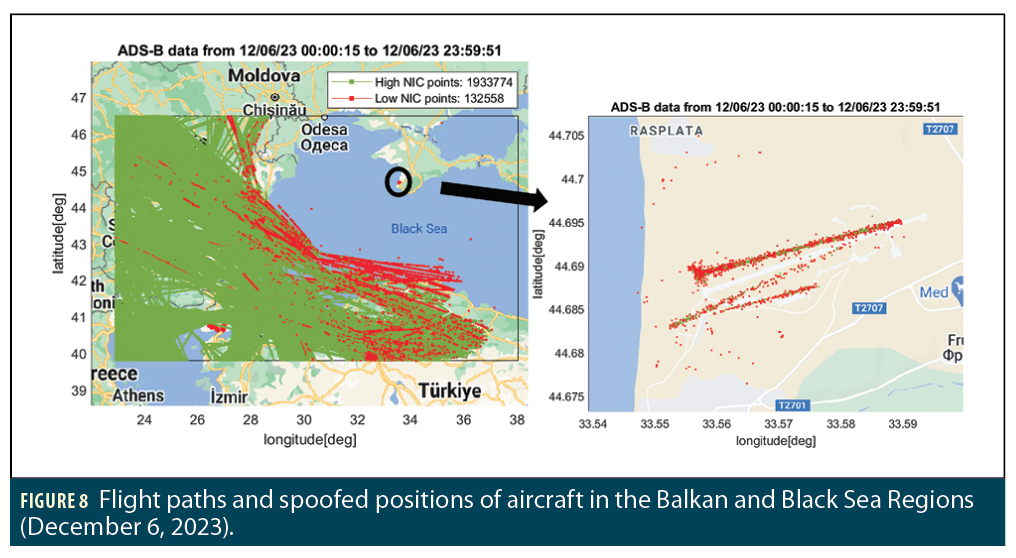
Spoofing of GNSS positions reported by ADS-B has been observed over the Balkans and the Black Sea region. Figure 8 shows an example spoofing event in which affected aircraft were spoofed onto a landing trajectory. The left-hand plot in Figure 8 shows ADS-B positions and NIC values for aircraft passing to the southwest of Russia on December 6, 2023. The right-hand plot shows the location that aircraft were spoofed to. The reported spoofed locations are over the Crimean Peninsula in a small area corresponding to the location of Belbek Airport (33.6º E, 44.7º N), which is now a Russian military airfield that has been periodically attacked by Ukraine since the Russian invasion [4]. The motivation for spoofing vehicle positions to this location is unclear, but the target appears to be military rather than civilian aircraft.
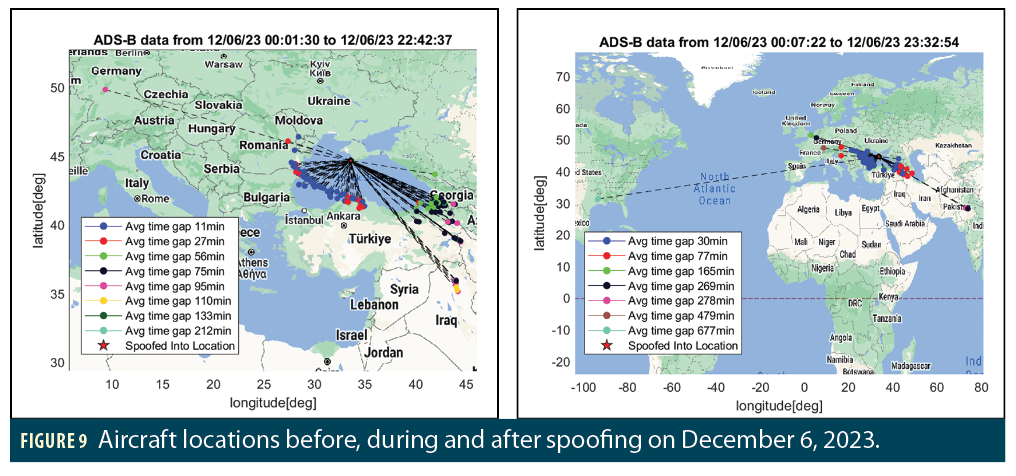
Figure 9 shows aircraft positions before, during and after spoofing on December 6, 2023. The red star in both plots indicates the locations where aircraft were spoofed to, which were mostly over the runway of Belbek Airport as shown in Figure 8. The left-hand plot shows each aircraft’s last observed position before being spoofed, and the right-hand plot shows each aircraft’s first observed position after recovering. The color of each point shows the time difference between the before/after position and the spoofed position. This is due to the lack of ADS-B ground receiver coverage along the coast, as most of these flights were not observed by ground receivers while they were flying over the Black Sea. For instance, for points with gaps longer than 20 minutes (i.e., all points that are not shown in blue in the left-hand plot), aircraft are not being spoofed directly from the “before” position to the “spoofed” position. Instead, the “before” position was the last time the aircraft was seen before being spoofed.
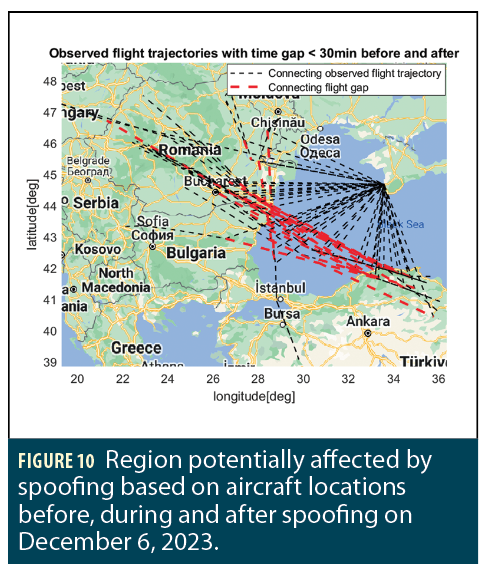
We estimated the region affected by spoofing based on the locations before and after aircraft were spoofed. We focused on aircraft with short time gaps between “before,” “spoofed” and “after” locations to maximize accuracy. Figure 10 illustrates the potential region affected by spoofing using red dashed lines. These are formed by connecting each aircraft’s flight paths before and after being spoofed. This relies on the assumption that the gap between the two components of the original flight trajectory is where the aircraft were actually flying while being spoofed. Therefore, spoofing is affecting the region that contains those gaps. The black dotted lines show the actual reported positions and how each flight jumped from its assumed path to the spoofed location at Belbek Airport.
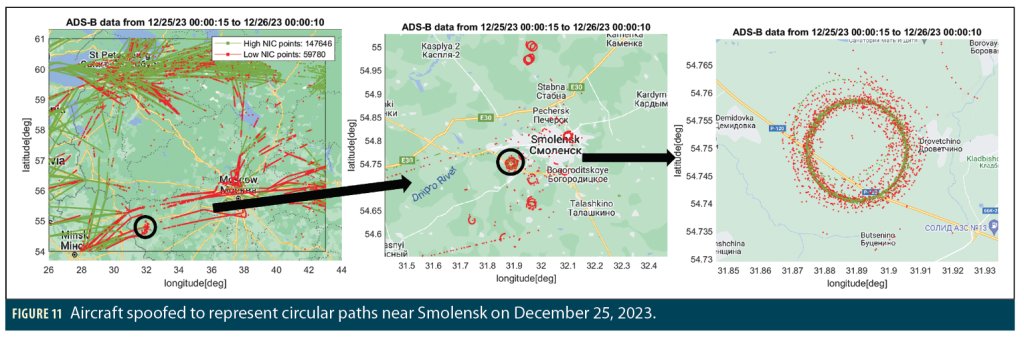
Unusual “Circle” Spoofing inside Russia
Another apparent spoofing of GNSS positions reported by ADS-B has been observed over Smolensk Oblast, Russia, in which aircraft were spoofed into circular trajectories. This type of spoofing was previously observed in receivers onboard ships near China and Iran (using AIS data) [13] and more recently observed in aviation by Zach Clements at UT Austin [3]. Figure 11 shows an example circle spoofing event on December 25, 2023. The reason for spoofing in circles is unclear, but [13] theorizes that (a) this is intended to confuse observers into believing the spoofer is near the center of the circle when it may not be, and (b) reducing the radius of the spoofed circular path can avoid triggering user alerts based on estimating Horizontal Position Error (HPE).
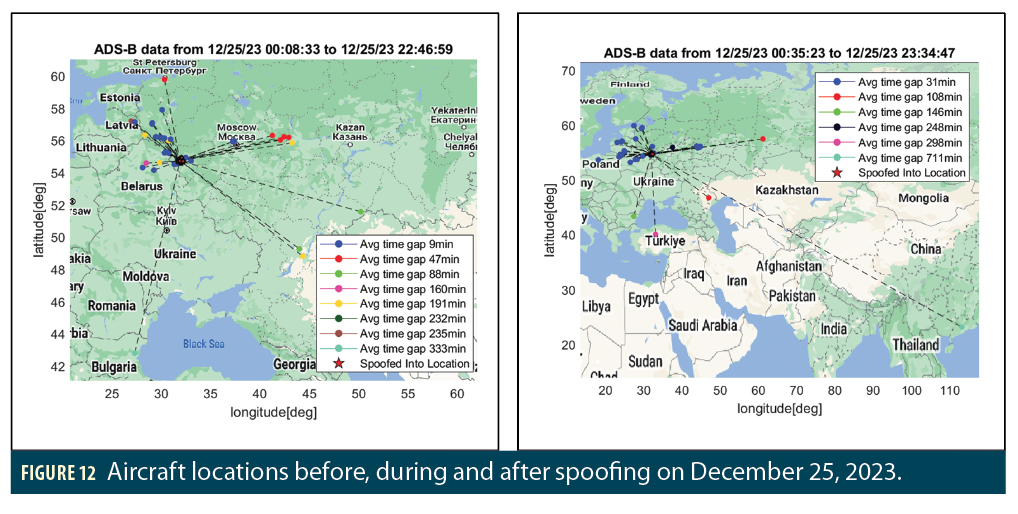
Figure 12 shows similar plots of aircraft positions before, during and after spoofing on December 25, 2023. Compared with spoofing events in the Black Sea region, this circle spoofing affects aircraft from different locations that are far away from each other, which can be observed by comparing the
locations of points colored in blue, red and green. This further suggests there could be multiple spoofers performing similar attacks at the same time. This motivates us to estimate the region affected by spoofing using a different method.
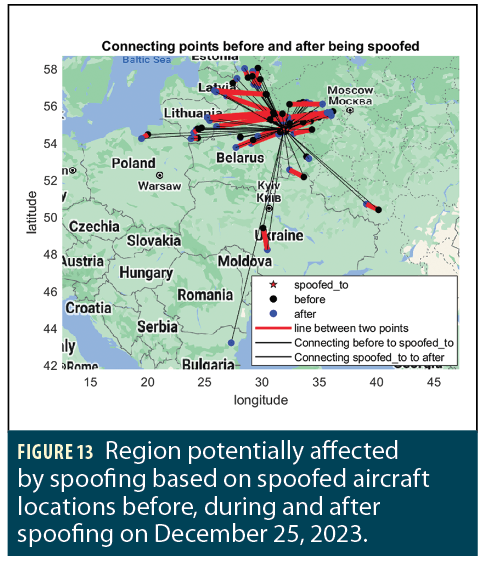
Figure 13 shows the estimated region affected by spoofing based on interpolated aircraft trajectories. Rather than connecting the apparent gaps in each aircraft’s flight path, we estimated where each aircraft was actually flying while being spoofed. We used this interpolated trajectory to identify each aircraft position immediately before being spoofed (in black) and immediately after recovering from spoofing (in blue). By connecting those two interpolated position points, we can estimate the location of the affected region more accurately by filling in the gap from loss of reports due to lack of ADS-B ground reception. The red lines in Figure 13 indicate the estimated regions affected by spoofing. The black lines identify how aircraft jumped from their intended flight paths to the spoofed location and how they recovered back to their original flight paths.
Summary and Conclusions
This article describes what the authors currently know about instances of both RFI (jamming) and spoofing observed in Eastern Europe within or near the borders of Russia. We have observed spoofing directed to a small set of locations at Belbek Airport in the Crimea and into circular movement patterns near Smolensk. These events appear to be caused by deliberate Russian military action based on what we have observed and what others have reported [2, 3]. The purpose of this spoofing is unclear but appears to be targeting opposing (e.g., Ukrainian) military operations.
These events are unavoidably affecting civil aviation, as demonstrated by the degradation of ADS-B NACp and NIC parameters that make them observable to us. At least some civil transport aircraft in the regions affected by spoofing report dramatically incorrect locations. Fortunately, to date, civil transport airplanes appear to be able to live with these threats while still operating safely, as they are merely passing over the affected regions.
Acknowledgments
The authors would like to thank the FAA for its support of this research as well as the other members of our laboratory and Prof. Dennis Akos of the University of Colorado for contributing to this research. We also thank the OpenSky Network [7] and the ADS-B Exchange [6] for providing ADS-B data for this study.
References
(1) Z. Liu, S. Lo, et al., “GNSS Interference: Getting to the Source,” Inside GNSS, Vol. 18, No. 3, May/June 2023, pp. 46-51.
(2) S. Willis, “Kaliningrad: Impregnable Fortress or ‘Russian Alamo’?,” CNA in-depth blog, May 15, 2023. https://www.cna.org/our-media/indepth/2023/05/kaliningrad-impregnable-fortress-or-russian-alamo
(3) D. Goward, “Circle Spoofing Comes to Aviation—first the Baltic, now the Mediterranean,” The Resilient Navigation and Timing Foundation, Jan. 7, 2024. https://rntfnd.org/2024/01/07/circle-spoofing-comes-to-aviation-first-the-baltic-now-the-mediterranean/
(4) E. Cook, “Crimea Airbase Attacked as Russians Bemoan Fighter Jet, Troop Losses,” Newsweek, Feb. 1, 2024. https://www.newsweek.com/crimea-airbase-attacks-ukraine-missile-storm-shadow-fighter-jets-russia-losses-1865896
(5) J. Wiseman, “GPSJam: Daily Maps of GPS Interference,” https://gpsjam.org/
(6) “ADS-B Exchange: World’s largest source of unfiltered flight data,” https://www.adsbexchange.com/
(7) M. Schäfer, M. Strohmeier, V. Lenders, I. Martinovic, M. Wilhelm, “Bringing up OpenSky: A large-scale ADS-B sensor network for research,” Proc. 13th Int’l. Symp. on Information Processing in Sensor Networks, Berlin, Germany, April 2014.
(8) Minimum Operational Performance Standards for 1090 MHz Extended Squitter Automatic Dependent Surveillance—Broadcast (ADS-B) and Traffic Information Services—Broadcast (TIS-B). Washington, DC, RTCA DO-260C, Dec. 17, 2020.
(9) Title 14 of the Code of Federal Regulations—14 CFR Part 91. Office of the Federal Register, National Archives and Records Administration, Washington, DC, updated 16 Feb. 2024. https://www.ecfr.gov/current/title-14/chapter-I/subchapter-F/part-91?toc=1
(10) GPS Standard Positioning Service (SPS) Performance Standard (GPS SPS PS), Washington DC, U.S. Dept. of Defense, 5th Edition, April 2020. https://www.gps.gov/technical/ps/2020-SPS-performance-standard.pdf
(11) Z. Liu, S. Lo, et al., “Real-time Detection and Localization of GNSS Interference Source,” Proceedings of ION GNSS+ 2022, Denver, CO, Sept. 2022, pp. 3731-3742.
(12) Z. Liu, S. Lo, et al., “Locating GNSS Interference Sources using ADS-B with Non-linear Least Squares,” Submitted to Navigation (forthcoming).
(13) G. Buesnel, “‘Circle Spoofing’ Is on the Rise,” Spirent blog, Aug. 17, 2020. https://www.spirent.com/blogs/circle-spoofing-is-on-the-rise
Authors
Zixi Liu is a Ph.D. candidate at the GPS Laboratory at Stanford University. She received her B.Sc. degree from Purdue University in 2018 and her M. Sc. degree from Stanford University in 2020.
Sherman Lo is a senior research engineer at the Stanford GPS Laboratory and the executive director of the Stanford Center for Position Navigation and Time. He received his Ph.D. in Aeronautics and Astronautics from Stanford University in 2002. He has and continues to work on navigation robustness and safety, often supporting the FAA. He has conducted research on Loran, alternative navigation, SBAS, ARAIM, GNSS for railways and automobiles. He also works on spoof and interference mitigation for navigation. He has published over 100 research papers and articles. He was awarded the ION Early Achievement Award.
Juan Blanch is a senior research engineer at Stanford University, where he works on integrity algorithms for Space-based Augmentation Systems and on Receiver Autonomous Integrity Monitoring. A graduate of Ecole Polytechnique in France, he holds an MS in Electrical Engineering and a Ph.D. in Aeronautics and Astronautics from Stanford University. He received the 2004 ION Parkinson Award for his Ph.D. dissertation and the 2010 ION Early Achievement Award.
Yu-Hsuan Chen is a research engineer in the GPS laboratory at Stanford University. He received his Ph.D. in electrical engineering from National Cheng Kung University in 2011.
Todd Walter is a Research Professor in the Department of Aeronautics and Astronautics at Stanford University. He is also a member of the National Space-Based Positioning, Navigation, and Timing (PNT) Advisory Board. His research focuses on implementing satellite navigation systems for safety-of-life applications. He has received the Institute of Navigation (ION) Thurlow and Kepler awards. He is also a fellow of ION and has served as its president.






