One of the great engineering successes of the International Civil Aviation Organization (ICAO) and its expert panels is the standardization of globally harmonized Communication, Navigation and Surveillance (CNS) systems. These standards, sometimes supported by more detailed industry standards, provide safe and interoperable services between aircraft and the ground and space systems supporting them. A key safety ingredient of these standards is that they are completely open, such that manufacturers know how to build their systems in a way that performance is uniform everywhere they are implemented around the globe. It is a considerable challenge, however, to keep an overview of all the aspects — knowing for instance that open standards means anyone wanting to spoof these systems can obtain corresponding standards and exploit vulnerabilities — and focus mitigation efforts on the most relevant weaknesses. Hopefully, we will be able to remain a step ahead of the evolving security threat in all these areas.
While in many cases, safety and security mechanisms are very similar, here they diverge completely: open standards mean that anyone who wants to fool or fake these systems can look up the corresponding standards to build capabilities which exploit every vulnerability. Of course, ICAO has recognized this issue, and security has risen to the top of the agenda (https://www.icao.int/Security/Pages/default.aspx, Additional Resources). In Europe, the issue is acknowledged in the recently published Radio Navigation Plan and worked on by EUROCONTROL, EASA and others.
The first ICAO Annex 10, Volume 1 standards incorporating GNSS appeared with its Amendment 76 in 2001 (Additional Resources). Only 17 years later, GPS L1 avionics (with some form of augmentation to meet aviation performance requirements) have become standard equipment for almost all passenger-carrying flights. Meanwhile, ICAO is busy preparing for the next generation of GNSS standards with dual-frequency and multi-constellation (DFMC) capabilities. Similar to the consumer world, but at a much slower pace due to the safety critical and certified environment, GNSS is making its way into numerous ground and aircraft systems to support a diverse range of applications.
For a variety of reasons, which include security concerns, the notion of sole-means GNSS discussed over a decade ago (GNSS Sole Service Feasibility Study, Additional Resources) to support seamless GNSS operations has been abandoned. Given that GNSS is not aviation-specific, but a shared system not under direct aviation control, ICAO and its member States recognize that alternative CNS capabilities will remain necessary. The 12th Air Navigation Conference tasked ICAO to investigate the “need for and feasibility of” an Alternate Positioning, Navigation and Timing (A-PNT) system (Additional Resources). The preliminary conclusion is that while GNSS is evolving from a supplemental means to a primary means, the terrestrial navigation aids (ILS, VOR, DME) will evolve from their conventional, primary role to what some call a “Minimum Operational Network” to help ensure safety and continuity of operation in cases of GNSS outages.
EUROCONTROL has been actively engaged in the development of mitigations against GNSS vulnerabilities, with the aim to make aviation use of GNSS as robust as possible while finding the right balance for retaining conventional capabilities. ICAO included the resulting “GNSS RFI Mitigation Plan” in its GNSS Manual, ICAO Document 9849, 2017 edition. A measure implemented at the European regional level is the inclusion of GPS Outage Reports by pilots in the EVAIR database (Figures 1 and 2). EVAIR stands for EUROCONTROL Voluntary ATM Incident Reporting, where GNSS issues are one among many others.
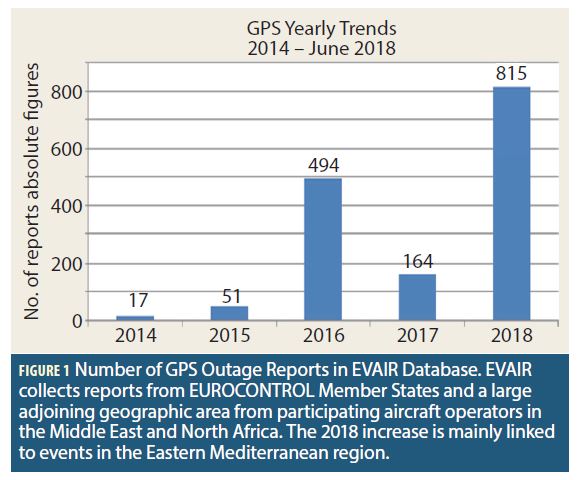
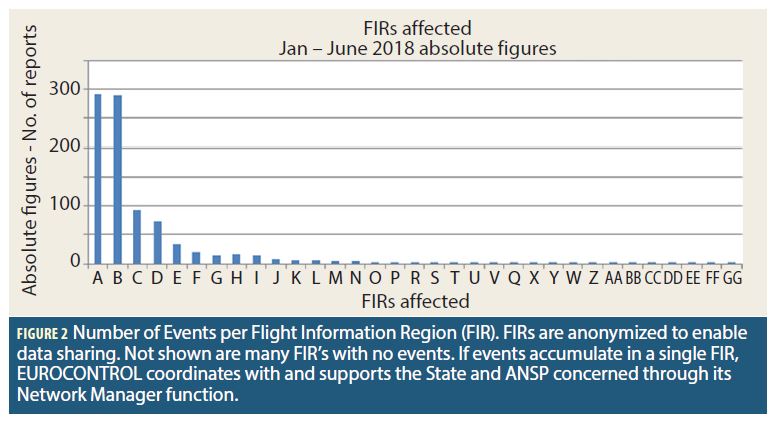
Pilots flying GPS-equipped aircraft over a decade ago were generally not concerned by GPS outages, since they believed “GPS always works”. This is a tribute to the continued quality of service provided to aviation. The three main GNSS vulnerabilities which can cause service outages are constellation weakness, propagation anomalies due to solar activity (ionosphere) and radio frequency interference (RFI). GPS constellation performance has been very good over many years and solar activity has not been dramatic, which leaves RFI as the main vulnerability. One problem with RFI outages was that they were not seen – because aviation did not look for them. Now that aviation is making a more conscious effort to collect pilot reports, we see that GNSS outages due to RFI occur on a still rare, but nonetheless regular basis. Normally, they constitute nothing more than an operational nuisance due to the redundant CNS capabilities on board aircraft and on ground. A lot more could be said on normal interference mitigation, including unintentional interference, intentional interference not directed at aviation and intentional RFI directed at aviation. However, this is not the focus of this article. Depending on the definition used, spoofing can be seen as either a special form of radio frequency interference, or as a completely separate category. Recently, the lines between spoofing and jamming have started to blur, as there can also be spoofing for denial of service, where a receiver locks up due to anomalous data – there is no RF overload but the result for receiver operation is still more or less the same.
Spoofing Mitigation and the CNS Security Context
The civil aviation position on GNSS spoofing some years ago was simple: it is not our problem. Spoofing was considered an advanced military capability, and therefore outside of the scope of civil aviation. If it would happen, the military would be called in to manage the situation and the affected airspace would be closed. Similar to the evolution of normal RFI to an actively managed topic, the view on spoofing is also changing. Triggered in part by the Hannover GNSS repeater incident (Naerlich, Additional Resources) it is now recognized that a variety of in-between spoofing stages exist, starting at badly adjusted repeaters and evolving to whatever any reasonably skilled, unreasonable tinkerer can obtain legally and cobble together with a modest investment.
It is important to recognize that currently, aviation is not shamelessly exposed to spoofing without any defense. While some may complain about the diverse outdated and spectrum-inefficient multitude of CNS systems used by aviation, this redundancy is essential to detect when there are unusual outputs from the GNSS sensor and to be able to continue the operation to a safe landing. Pilots are trained to detect and deal with equipment malfunction in every phase of flight. However, one must admit that when thinking through the worst case, sophisticated terrorist spoofing attack scenario, these defenses may be insufficient. Therefore, it has been agreed between ICAO, RTCA and EUROCAE to improve robustness against RFI and spoofing in next generation GNSS avionics. The only problem is to define what this “improvement” should look like. A number of aviation GNSS and security working groups are currently working on this.
A 100% guarantee of safety and security is only possible if flying is stopped altogether. Therefore, a residual security risk will always remain when operating an aircraft, including any risks posed by GNSS spoofing. The question is, what level of risk is acceptable and responsible. In many everyday situations, wearing a bullet-proof vest would be more secure. Most people have unconsciously decided that given the perceived magnitude of the security risk, this is not necessary. In most regions of the globe, experience justifies this decision. While the spoofing threat can appear to be less likely than a stray bullet, for a public commercial activity of flying multiple passengers through the air in large metal tubes at high speeds, a more structured and reasoned approach by appropriate experts is necessary.
For safety assessments, aviation uses a risk assessment matrix (Figure 3). The greatest risk reduction priority is on issues which have both a high probability of occurrence and severity of impact. In security assessments, it can be very difficult to accurately estimate the probability of occurrence, since this is in large part driven by random decisions of humans with above average irrationality. An easier and more productive method is to replace the probability of occurrence axis with feasibility. The view that can be taken is that if a certain threat scenario can be easily accomplished while causing a severe impact, sooner or later some single ignorant individual or hostile organization may try it (i.e., setting the probability of occurrence to 1 in terms of risk management). Expert security risk assessment teams review all possible threats and evaluate what barriers can mitigate those threats, implementing or strengthening them through a security risk management system if necessary. An important principle is to limit the “success probability” of an attack: if the likelihood of being able to achieve a serious impact is low while the risk of exposure or detection is high, the scenario should lose attractiveness even for deviant personalities.
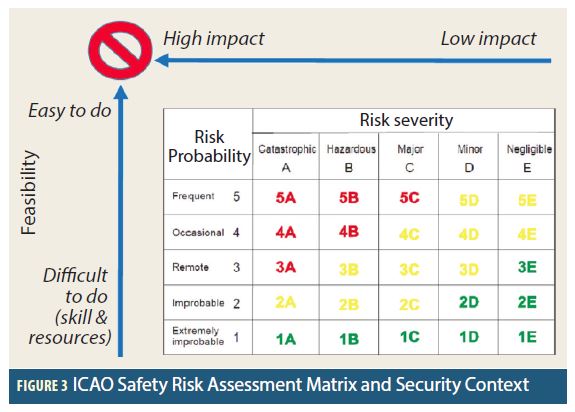
While this logic has merit, security experts need to remember that people will always do unexpected things, without fully realizing the consequence of their actions. A good example are powerful laser pointers, which some people have pointed at aircraft in flight without realizing the dangers they can cause to flight crews. But a laser pointer is also a much simpler consumer product which can be purchased and used without any effort. Purchasing a spoofer kit online and upgrading it to point with a directional antenna at an aircraft carrying passengers and crew quickly leaves innocent territory.
In some cases, mitigations can be surprisingly innovative. In a recent case near a major European airport, a “bored individual” pretended to be an Air Traffic Controller, talking to aircraft on final approach using a hand-held VHF transceiver. A very pragmatic solution was implemented during the several weeks needed to track down the individual. Because “the kind of people that do these things are usually men” (as stated by a colleague close to the investigation), only female Air Traffic Controllers were assigned to manage the approach in question, and pilots requested to only talk and listen to instructions from a female controller.
Therefore, when analyzing future spoofing mitigation mechanisms in next generation, aviation GNSS receivers, some inherent constraints need to be accepted:
• Barring premature replacement due to rising oil prices, a typical transport category aircraft lasts 30 years, with at most a minor avionics upgrade around mid-life. Some manufacturers are still selling SA-unaware GPS receivers! Given the much faster evolution of spoofing threats and associated technical capabilities, some anti-spoofing measures could lose their effectiveness relatively quickly. Aviation will always lose a technology cat and mouse race.
• Even security measures are subject to cost constraints. For example, additional drag (fuel consumption) and installation complexity means that advanced technology such as Controlled Radiation Pattern Antennas (CRPA) will not become a realistic option for civil air transport aircraft.
• More generally, civil anti-spoofing technology should not rely on advanced military technology subject to ITAR (International Traffic in Arms Regulation).
• Any adopted measure should not risk causing additional harm. An example is the strengthening of cockpit doors and access control post the 9/11 attacks. These played a contributing role in the crash of Germanwings flight 9525 in 2015 <https://en.wikipedia.org/wiki/Germanwings_Flight_9525>. Some spoofing mitigation measures could reduce simple jamming robustness or continuity of service.
• In general, solutions need to be globally interoperable, accessible to all, and safe.
Another aspect is balance across all CNS systems. Any effort spent on GNSS, as increasingly relevant as it is, needs to be balanced against other vulnerabilities. Making an analogy to securing a house, it makes no sense to spend a fortune on a double bolted steel front door if there is a back door which remains completely open. The comparison is useful but has its limits, because navigation has some different features compared to communication and surveillance. The primary client of navigation is the aircraft and the pilot, and positioning systems have a direct link to flight guidance systems. For communication and surveillance systems, the primary client is air traffic control, using it as a tool to ensure aircraft separation. So if an attacker wants to affect the path flown by an aircraft rather than just causing confusion, navigation systems are the obvious target.
GNSS Spoofing and Aviation Navigation Systems
Introducing the notion of path illustrates that this can be done in two possible ways: either change the desired path or change the indicated position. In the first case, a new desired path can be defined, where the navigation system will accurately lead the aircraft to its falsified destination. In the second case, the falsified position needs to be controlled in a way that its interaction with the defined path leads to the desired wrong path. So for an aircraft on a final approach, the indicated position could be increased in altitude in order to cause flight control commands which make the aircraft descend below path. Both of these mechanisms quickly reveal the significant benefit of independent altitude and heading, be it barometric or a radio altimeter, or from a gyro-compass (horizontal heading), respectively. In general it can be observed that the more critical the operation (size of aircraft / number of passengers / traffic density of airport), the more safeguards are in place, including altitude warnings in ATC systems based on surveillance sensors. Due to controlled flight into terrain (CFIT) being one of the major safety risks, many safeguards have been developed which are also efficient against security threats.
The importance of safeguarding the reference path has already been recognized in GBAS standards. The objective of a precision approach guidance system is to get the aircraft as close as possible to the right spot on the ground, at a location with a runway, into the so-called touchdown box. GBAS broadcasts the Final Approach Segment (FAS) definition to its users through the VHF Data Broadcast (VDB). A relatively obvious target is for a spoofer to try and inject a false path and send it to an aircraft in a VDB message slot. Due to this, an authentication scheme has been developed that will make spoofing GBAS very difficult. The scheme is a requirement for Cat II/III operations and a recommendation for Cat I. In other GNSS-based approach and landing systems, the path is defined using an aeronautical database, where numerous integrity checks are performed in a relatively closed data chain, limiting path definition falsification to insider attacks.
But what about other, non-GNSS-based approach and landing guidance systems? The ICAO GNSS Manual contains the following statement: “It is considered that the spoofing of GNSS is less likely than the spoofing of traditional aids because it is technically much more complex” [7, section 5.3.5]. Indeed, expert judgement (without a detailed analysis and actual testing) suggests that spoofing an ILS is simpler than spoofing GNSS. But even that is not as trivial as a rough evaluation suggests. Many of the same safeguards are in place for ILS also, including an independent barometric altitude check. Falsifying ILS guidance was even a topic of a major Hollywood movie: “Die Hard 2” and Windsor Airlines Flight 114. Not surprisingly, it contains many inaccuracies, while in many decades of actual global operations, no attempts of ILS spoofing have been recorded.
A sensitive topic such as spoofing aviation navigation and guidance systems can’t be taken lightly and must be updated as the security situation evolves. Relying on a long history without any events may not be reliable indicator of the future, especially as it is very difficult to monitor for spoofing threats. How do we know we have been spoofed? We may observe some anomaly but it is very difficult to find out if it was a simple equipment malfunction or a targeted spoofing attack. The only thing that can be said with reasonable certainty is that there is no civil record of targeted spoofing attacks which actually lead to accidents. All aircraft accidents are investigated thoroughly and typically include a long list of contributing factors. It is unlikely that an attacker manages to select a flight ahead of time which is experiencing several safety issues just to mask a major security issue.
Nonetheless, the GNSS Manual statement above may need to be revised at some point: yes, it is technologically a lot more advanced to spoof GNSS. However, with advances in digital signal processing, capabilities are becoming available where not much specialized radio frequency engineering knowledge is needed anymore for an attack. Traditional, old-fashioned aviation navigation systems still use a lot of very specific, analogue technology, which is not appealing to tech-savvy experimenters. GNSS on the other hand is a lot more software-centric and in use by many different applications in many different contexts. This results in a cross-domain risk where capabilities developed for other GNSS purposes could be modified and used against aviation.
Closing Open Doors: Threat Scenario Analysis
So how do we apply due diligence to mitigate against GNSS spoofing risks in this evolving aviation CNS context, taking into account its inherent limitations? The first step is to assess threats and risks and then close any doors which can reasonably be closed. But how does one know which doors to pick, especially when accurate threat data is hard to obtain? While many things can and are being done at the operational level, the remainder of this article will discuss what could be done in next generation, DFMC GNSS receivers. This needs to consider the operational context of aviation GNSS receivers: the multipath environment is relatively benign and dynamic, accuracy requirements are generally not demanding with common use of carrier smoothing, and tracking loops need to be able to deal with normally encountered dynamics effects. Another key aspect is that it is difficult to access an aircraft GNSS antenna directly, so most spoofing injection scenarios will be non-coherent and may often follow a first jam, then spoof pattern. Even if the attack does not foresee a jamming first, getting the spoofing signal level just right at the aircraft antenna is not trivial, therefore leading to spoofing attacks which may first jam the receiver.
A natural start is the simplest, unintentional spoofing scenario, where a single data point exists: badly installed or malfunctioning GNSS repeaters. The German Air Navigation Service Provider (DFS) pointed out in the discussion following the Hannover incident that current GPS receivers are dumb: even if they are on an aircraft in flight, they will be happy to display a static position when fully locked on to the repeater. But how will the receiver know when its aircraft is in flight? A simple solution for this could be the weight-on-wheel switch, used by numerous avionics systems. But introducing a new connection to a GNSS receiver raises new complexities. What if the weight on wheels is out of service? Would this impact the GNSS receiver? With any interface, a dependency is created. This may lead to inconsistencies in certification levels, if the new external component is not developed to the same rigour. Therefore, the preferred solution will always be to detect dynamic state by the receiver itself, before relying on an external interface. Also, all the in-between scenarios where the aircraft receiver is tracking a mix of real satellites and the repeater signal need to be considered. So a defense at the range tracking level seems to be preferable over a position domain monitor. On the other hand, maybe some logic can be applied which enforces realistic trajectory evolution, respecting Newton’s laws? OK, but then this may involve a considerable computational load. As engineers, we are eager to speculate about many possible solutions. When doing so, it quickly becomes apparent that even a relatively trivial spoofing mitigation function against the most basic threats is far from simple to implement.
Following the logic applied in the RFI mitigation plan, the next area to consider is spoofing where aviation is not the intended target. In general, spoofing is an intentional act, since knowledge of the victim receiver characteristics and functions is required to design the attack. Furthermore, it is normally only effective against a single target. Therefore, the potential for aviation to suffer collateral damage from spoofing not directed at aviation is minimal. It helps that successful spoofing requires insertion of signals at the same power level as GNSS, which means that only a very badly designed spoofing attack with inappropriate amounts of power could result in collateral jamming. But are there possibilities to carry out spoofing attacks which impact more than a single target receiver? At extended ranges, differences in propagation losses become less significant, possibly creating the opportunity for a multi-receiver impact. While it will not be possible to control multiple receivers by injecting different trajectories from a single source, common errors might be possible. This would more likely cause confusion than sensor outputs leading to an actual threat. While far from a scenario with demonstrated feasibility, one area of concern here could be data spoofing; a denial of service attack leading to a receiver to lock up, needing a factory reset. Just like any other product, GNSS receivers are not tested against every conceivable version of non-ICD-compliant signals. For example, the reaction to false ephemeris data is hard to predict. Here more work is needed to see if a spoofing attack could be set up which could disable all receivers transitioning through a given area.
The next level up would be some sort of meaconing or replay attack where the spoofing signal source is not static, but following some realistic aircraft dynamics. It is beyond the scope of this article to describe all the various ways in which this could be done other than to say that generating the spoofed reference trajectory and transmitting it to the aircraft in real time are not easy either. Any sort of attacks at the dynamic range or position domain done to actually try and misguide the aircraft are, luckily, quite challenging. We abandon the reflection on spoofing scenarios at this point: this topic is quite sensitive, and it is not appropriate to go into full detail in a publicly accessible magazine. Primarily, we aim to explain that for a good number of scenarios, a good number of defenses are already in place and expected to be effective. Furthermore, next generation GNSS receiver designs should consider these scenarios and see which additional defenses can be implemented. As a minimum, the defenses must be effective against the most common and simple threat, GNSS repeaters and other forms of “simple” spoofing. A variety of options are being studied, ranging from monitoring of AGC, C/N0 and clock bias to more sophisticated methods. Just as important as the actual defense mechanisms is the understanding of the impact of the various spoofing scenarios on actual observables, i.e., how can an aircrew or an internal data recording notice that a spoofing attack is occurring?
Authentication as a Possible Spoofing Mitigation?
One of the more advanced defense mechanisms being studied is authentication. For aviation to use authentication features, a number of factors need to be considered. First of all, public key management represents a fundamentally new mechanism that requires additional overhead. It is unlikely that it will be worthwhile for aviation to implement a public key infrastructure (PKI) just for GNSS alone. If, however, PKI is implemented for many other reasons such as securing communications data links, then by just adding some features for navigation, authentication becomes a lot more palatable. On the GNSS system side, it is also a lot better if there are many other applications using authentication than aviation alone. In general, aviation limits as much as possible to levy unique requirements on GNSS system providers. But finally, the benefits and implementation complexities need to be considered.
On the positive side, authentication is an intrinsic capability, remaining internal to the GNSS receiver, without any new interfaces to other avionics except key loading. As discussed before, one of the main strengths of aviation is the level of diversity and redundancy of systems, leading to a fantastic resilience and integration potential. However, with each more sophisticated integration, system complexity and dependency increase. So finding GNSS-internal solutions has some appeal.
The next question is on application requirements which authentication needs to meet. The most critical navigation operations in aviation are final approach and landing. Current SBAS (EGNOS, WAAS) are capable of supporting Cat I approaches, while navigation data authentication is under discussion for the next generation standards. Cat I operational requirements dictate that authentication needs to respect the 6 seconds time to integrity alert and not negatively impact other performance aspects such as continuity. But strength in authentication is linked to the length of the key. If authentication needs to happen continuously instead of only once at the beginning of the approach, and if it needs to continue to authenticate the signal during the approach, then it needs to be done within the 6 seconds time to alert, while also leaving some room for a missed authentication due to bit errors. When relaxing authentication requirements to something less than near real time, key length can be increased to make it stronger, but then other vulnerabilities become greater again.
More generally, authentication and the need to decode a long key may bring other challenges: if now it becomes possible to just send a short pulse every 6 seconds to knock out part of the authentication sequence, then vulnerability to jamming is increased. If authentication would be adopted, the more sensible approach would likely be to authenticate once or twice before beginning an approach, and then preserve this solution with other monitors in line with the timescales of corresponding threat scenarios. Again, the right design balance would need to be found to ensure that the added complexities actually bring benefit in hardening GNSS against attacks.
Finally it has already been recognized in the community that navigation data authentication will only protect against some spoofing attack scenarios, but not all of them. From an initial analysis and looking at the GNSS signal and guidance elements in descending order of priority, protecting navigation data would come in at the third place after first protecting the guidance path definition and then the main ingredient of the actual navigation solution, pseudoranges. Therefore, the complexities of introducing an authentication feature need to be evaluated against doing other, more simple things, such as adding barometric altitude monitoring (through equipment integration, not replying on pilot monitoring only).
Summary and Conclusion
These arguments should not be understood as aviation closing the door to authentication – it is more a report on ongoing thoughts and discussions. Certainly, increasing security of such an essential CNS element as GNSS in any feasible way is a welcome possibility. However, to judge what best to do and how, an integrated analysis needs to consider many factors and weigh them carefully. This article aims to highlight some of them, and also to educate the GNSS community about the complexities of the larger aviation and CNS system context. Therefore, we encourage further research on the topic of GNSS security in aviation, so that this evolving relationship can converge towards an effective mix of operational measures and real time equipment mitigation functions. This should ensure that GNSS spoofing will remain something that has so far never been found to be a contributing factor to an aircraft accident or incident.
This article has focused on GNSS spoofing attacks directed at aircraft. However, many ground CNS systems also use GNSS for a large variety of purposes, including time synchronization. For ground CNS systems, many of the constraints discussed herein do not apply and are quite similar to other sectors. For such receivers, authentication and many more advanced mitigation techniques are completely feasible options. The scope of this discussion is further limited to the GNSS PVT information as it is obtained by the GNSS receiver through signals from the antenna. It did not look at how the PVT information could be corrupted once it leaves the receiver for further processing. This is also an active area of security analysis, which has commonality with securing system architectures and data channels in general. It is a considerable challenge to keep an overview of all these aspects and focus mitigation efforts on the most relevant weaknesses. Hopefully, we will be able to remain a step ahead of the evolving security threat in all these areas.
Acknowledgements
The author would like to thank Paco Salabert, Pascal Barret and other EUROCONTROL colleagues for their review and helpful discussions.
Additional Resources
[1] Annex 10 to the Convention on International Civil Aviation, Aeronautical Telecommunications, Volume I, Radio Navigation Aids, available from the International Civil Aviation Organization
[2] ICAO, see https://www.icao.int/Security/Pages/default.aspx
[3] European Radio Navigation Plan, European Commission, Version 1, 9 March 2018, available at http://ec.europa.eu/DocsRoom/documents/28325
[4] GNSS Sole Service Feasibility Study, EUROCONTROL Experimental Centre Note No. 04/03, available at https://www.eurocontrol.int/eec/gallery/content/public/document/eec/report/2003/007_GNSS_Sole_Service_Feasibility_Study.pdf
[5] ICAO Doc 10007, Report of the 12th Air Navigation Conference, Recommendation 6/7d, 2012, available from the International Civil Aviation Organization
[6] ICAO Doc 9849, Global Navigation Satellite System (GNSS) Manual, Advance 3rd Edition, 2017 (unedited), available from the International Civil Aviation Organization
[7] Naerlich S., “Treatment of GNSS Repeaters”, ICAO Navigation Systems Panel, Working Group of the Whole, Working Paper 3, Montreal, Canada, 9-18 November 2010
Author
Gerhard (Gary) Berz is a Senior Navigation Systems Expert at EUROCONTROL, where he chairs the Navigation Steering Group on infrastructure aspects and actively participates in a number of working groups, including the ICAO Navigation Systems Panel and the EU/US Working Group C on Next Generation GNSS. One of his main work areas is GNSS RF interference mitigation and spectrum matters. Before joining EUROCONTROL, he worked at skyguide, the Air Navigation Service Provider of Switzerland, and for the U.S. Naval Air Systems Command. He obtained avionics engineering degrees from Embry Riddle Aeronautical University and Ohio University.






