Someone has updated 19th century American slang to resonate in the 21st century’s international commerce and shipping scene. A mysterious new electronic weapon has surfaced in China, spoofing GPS signals in a way that experts have never seen before.
To”shanghai” someone traditionally meant to drug and stow them away onboard a ship, outward bound on a long journey, quintessentially across the Pacific to Shanghai, China. In essence, tricking them.
[Photo by Robynne Hu on Unsplash]
A party or parties in that same city, now the world’s busiest port, is falsifying GPS data to trick ships into thinking they are somewhere else, and/or to trick harbor police into thinking the perpetrators are not there at all. Thousands of GPS spoofing incidents have occurred in Shanghai since July 2018, peaking in July 2019. They are peculiarly and uniquely different from any other spoofing noted around the world — notably different from Black Sea and other Russian-related incidents. They continue to puzzle one of the leading researchers in GPS signal spoofing, professor Todd Humphreys, director of the Radionavigation Laboratory at the University of Texas at Austin.
“This is a moderately sophisticated spoofer,” Humphreys said. “Somebody is transmitting a spoofing signal affecting ships up to 20 km away. The signal spoofs a location on a circle with radius from 84 to 200 meters and rotates counterclockwise with a period from 60 to 68 seconds.”
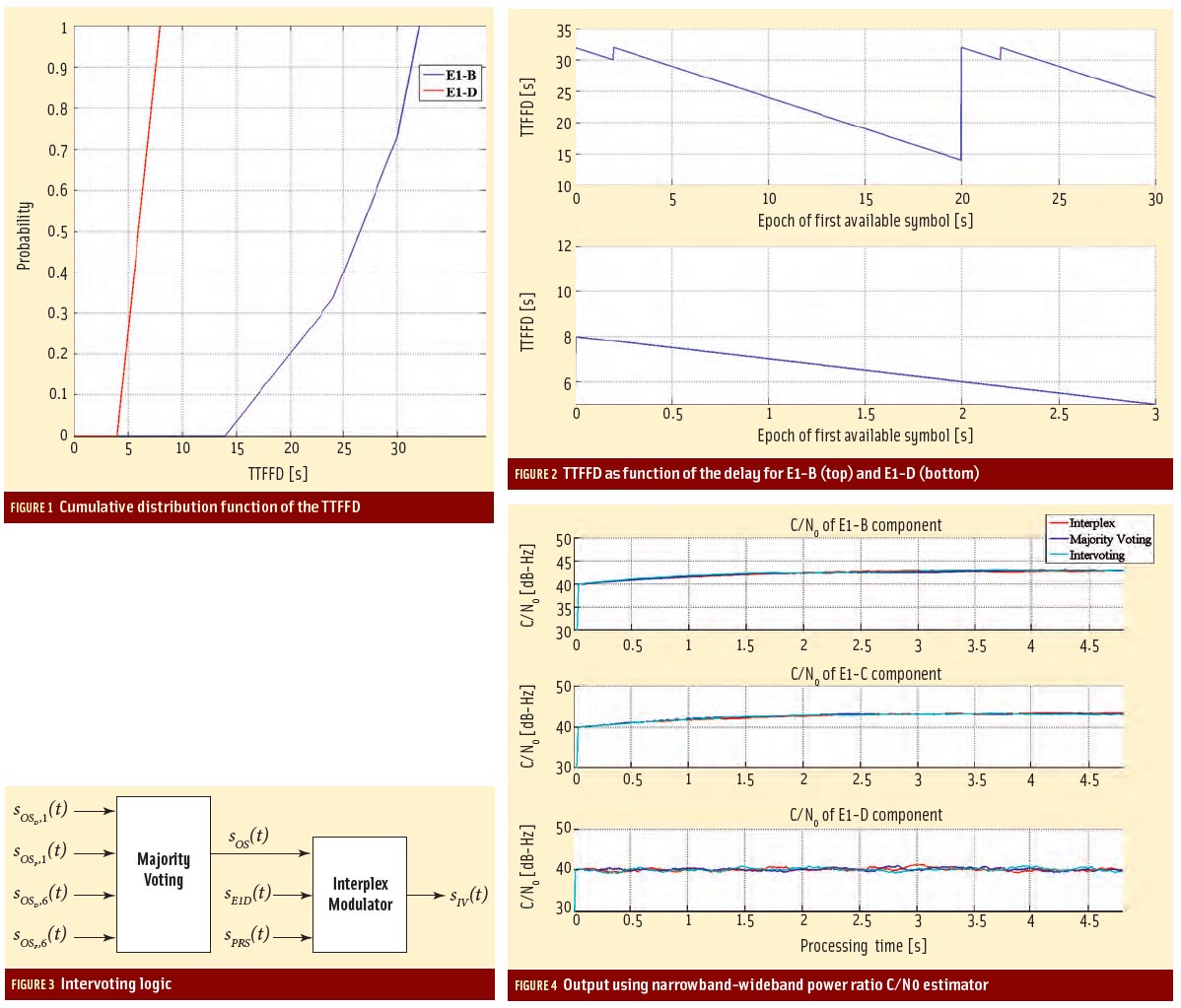
Neither Humphreys nor researchers at the Center for Advanced Defense Studies (C4ADS), a nonprofit that analyzes global conflict and security issues, had ever seen data like this before. It shows ships jumping every few minutes to different locations on the circumference of large circles centered on a chemical manufacturing plant.
Humphreys previewed early data of the phenomena to an audience at ION GNSS+ in September, and they were amazed. “To be able to spoof multiple ships simultaneously into a circle is extraordinary technology. It looks like magic,” he averred.
C4ADS has posted an online video showing the spinning spoofing circles, with the timing displayed beneath it. Some viewers may need to download the video first in order to get it to play, depending on bandwidth issues.
“Using publicly available AIS data from providers such as WindwardOceans, we uncovered new evidence of large-scale GPS spoofing taking place in the Port of Shanghai. The activity forces GPS receivers to report positioning information along a circle near the Huangpu River,” stated the organization.
Humphreys has since analyzed higher-resolution data.
“Focusing in on a particularly clean set of circular points from a single receiver on 14 March 2019, I was able to see from the high-time-resolution data that the receiver was being spoofed around a 200-meter-radius circle with a period between 60 and 68 seconds. I have four clean intervals over which this is the case (same receiver).
“The important conclusion we can draw from this is that the spoofing is not simultaneously causing receivers to appear at different places around the circle, as it seemed from the low-time-resolution AIS data. Rather, the intended spoof location is a point that rotates around a circle. The circle’s radius is usually 100 meters, but changes to 200 meters and then to 84 meters.
“A straightforward explanation for this is as follows: Someone has set up a GNSS signal simulator (spoofer) to generate signals consistent with a circular trajectory.
“But it appears that the simulator is of the somewhat sophisticated type whose data can be aligned with live-sky signals.
“I conclude this from the fact that many of the spoofed locations are not on any circle, which likely indicates that they are the result of a navigation solution that combines authentic with spoofed signals. This is only possible in most receivers if the spoofed signals have an ephemeris time matching that of the authentic signals.
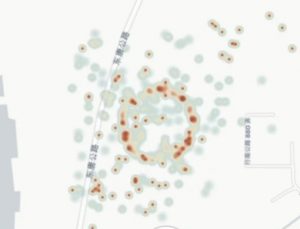
“Here is an interesting plot of the locations ships reported just before being spoofed:
“This indicates that the spoofing is affecting ships from the location of the circle all the way up the Huangpu to the Yangtze (about 10 km) and then along a stretch of the Yangtze that spans about 30 km. Affected ships are also found south of the circle for about 10 km along the Huangpu.
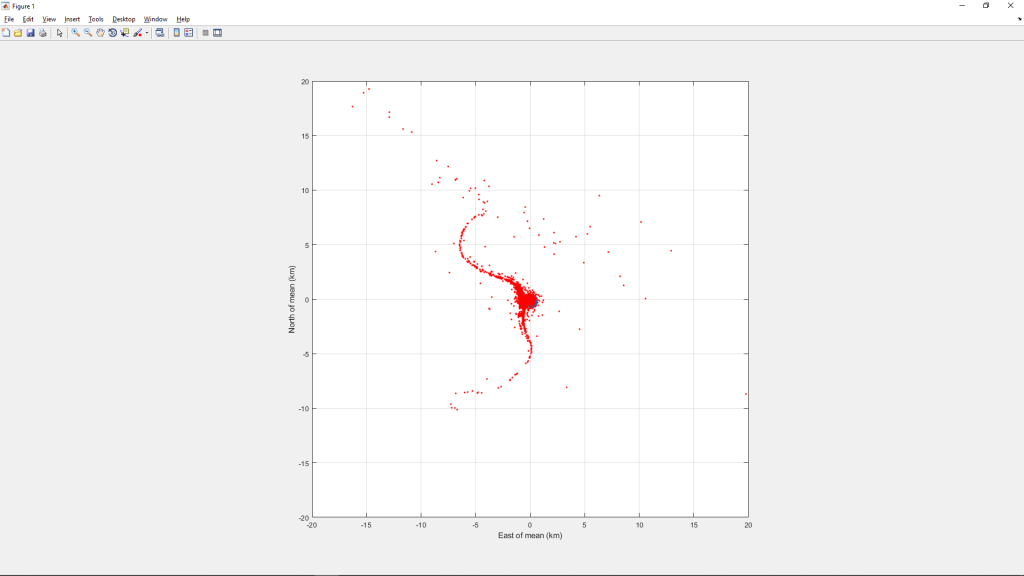
“Here is a zoomed view near the bounding box:
“This view suggests that there is a higher density of prior-to-spoofed locations along the Huangpu just west of the bounding box. This may be due to a higher density of ships in that area, but given that the overall span of the first chart above is roughly centered on the bounding box, I think it’s safe to conclude that the higher density of prior-to-spoofed locations in the above chart indicates that the spoofer’s actual location is near the bounding box (and thus near the circle).
“Open questions:
- Who is behind this?
- Why have they not been stopped in over a year by Chinese authorities?
- They must have access to a high tower or chimney to affect ships as far as 20km away. How did they get such access?”
All conjectures as to the identity and motive of the spoofer(s), so far, lack hard corroborative evidence. It could be sand thieves, illegally quarrying the riverbed for resources termed “soft gold” in Shanghai’s ultra-booming construction market. It could be petroleum smugglers. Both illicit trades are worth millions of dollars.
It could be the Chinese government testing new electronic weaponry. The adjacent South China Sea is a simmering cauldron of shipping conflicts and vulnerabilities and international territorial disputes.
A story by Mark Harris in the MIT Technology Review contains further background on the various possibilities and on the shipboard AIS transponders that are at the heart of this conundrum.