The following is a partial transcript of a talk given to the National PNT Advisory Board Executive Committee (PNTAB ExCom) on December 9, 2021. It connects GNSS signal authentication, by both Galileo’s OSNMA and the proposed GPS Chimera signal, with developing PNT capabilities in 5G telecom technology, and further, with software-defined radio (SDR) capabilities aboard some GNSS satellites that could place GPS in the second tier.
LOGAN SCOTT, LS Consulting
Let’s talk about some practical systems for signal authentication. This usually involves two aspects. One is data authentication, which is basically proving the 50-bit-per-second data stream is correct and came from the satellite. That’s a pretty straightforward thing to do in that the satellites can be uploaded with the data along with the digital signatures. And in receivers, you can go off and check that.
Ranging authentication is a little bit more difficult, but it’s probably the more important one to do. Basically what you’re doing is you’re establishing the provenance of the pseudoranging codes. This is typically done by inserting cryptographic-based watermarks into the signal.
So when we talk about the satellites, it’s a fairly complex modification to a non-SDR satellite, but it’s a very straightforward modification to an SDR-based satellite. One of the things you’re going to hear here, is SDR is good for a lot of things.
As far as the receivers go, it’s a modest modification to this, because you need some memory to take an RF snapshot, and the snapshot I’m talking about can actually be smaller than the one you take on your phone. This is not a huge amount of memory. This is pretty small.
Let’s take a look at Galileo first. One of the key things that they had was a decision back in 2017, to sign a law, and it’s a marvel of simplicity in that it basically says, there’s a problem, go fix it. That’s the entire text of it right there. As a consequence, the Galileo people went off and started trying to figure out how to fix it.
So you now have Galileo Open Service Navigation Message authentication (OSNMA) in a public testing phase, and it is currently being broadcast by 20 Galileo satellites.
This is not an operational system. It’s in public test phase, but there is an intention to go operational in the 2023 timeframe.
The key materials that you need in order to process this signal are being made available on servers and it is publicly available material. This key material, I should emphasize, is not sensitive in the sense that I could hand it to a spoofer, I could hand it to just about anybody, and they’re not going to be able to make any real use of it. It strictly is the public side of a private-key/public-key authentication system.
What are their stated intentions? With regards to data authentication, it is on the E1B single component; this is basically near an L1 frequency. On the ranging authentication, which they have announced, they’re saying that’s going to be on the E6 frequency band, and that is also one of the FCC proscribed signals. So that’s going be an interesting policy question, how you deal with that? Because it is a critical need and capability that GPS does not have.
Some of the important features: they are publishing the keys, you basically have to touch the receiver once at birth, if you want, and you give it some key material and you’re good for life. The reason for that is they have over-the-air rekeying mechanisms that allow you to constantly update your key material as needed. It’s not like you have to go in there every few months and reload the receiver. It’s good for life.
The other thing that is really key is they authenticate satellites that are not transmitting OSNMA. In other words, they have a cross-authentication capability. Looking at the protocol, with cooperation from the State Department, they could actually authenticate GPS signals, as well as Galileo—that is within the protocol capability.
How long does it take to authenticate? The time to first authentication is around three minutes 95% of time. Now I’m talking with Ignacio [Fernández Hernández of the European Commission], he thinks he can push that to about 100 seconds, and I believe it.
In terms of current coverage, basically 98% of the world is covered right now in a test phase. Now, the European receiver manufacturers are very active in developing OSNMA capability. They’re testing it, they’re learning a lot.
The Europeans are also looking at putting ranging code authentication on the E1 signal. If they do that, then now they open themselves up to something I call fast-channel authentication. I’ll get to that in a moment.
Here’s my core assessment on Galileo. Congratulations and well done. It’s a superb job of engineering, it’s the world’s first civil satnav authentication system. They have a strong vision, they have the leadership support to go off and do it. I wish I was talking about GPS, but this is what the situation really is.
With regards to Chimera, that’s the U.S. system that we’re working on. That actually had its origins in the film industry back in the 2002 timeframe. We had Barry Glick, founder of MapQuest, we had Mark Feiler, president RKO Pictures, and Morgan Fairchild, famous film actress, they’re all involved in the origin of this signal. The signal’s characteristics is basically it’s got data authentication, and there’s two forms of message signing that are possible. One is keep it simple stupid, which is what the AGT 100 is, and then a more advanced version called TESL. That basically allows you to do things a little bit faster.
As far as the authentications, there’s actually two authentication channels for ranging. One is the fast channel and one is the slow channel. The fast channel allows you to authenticate once every six seconds, the slow channel once every three minutes. This is going to be broadcast by the NTS3 satellite, and that’s planned for launch in the 2023 timeframe. It’s going to take about 18 months to field new signal starting from scratch with that satellite, but the Chimera and several variants are already running.
When we launch that satellite, we’ll see one Chimera signal and then four coming out of the same satellite.
The data signing process: You get a signature once every three minutes, and then that signature for the data signing, that’s used to drive the slow channel marker key. Mostly the signal is just regular L1C signal, but there are these markers stuck in there. And then we have the six-second marker keys, those because of the slower rate of our data channels we can’t support sending those keys directly over the air. So you have to get those out-of-band.
You might think, well, I’ve got to connect to the internet. Well, we had a serious offer from a CEO of a multi-billion dollar company who provides worldwide authentications to transport those keys. And so at least in principle, if you had those fast channel keys or keys being broadcast by a worldwide augmentation system, you would have six-second capabilities to authenticate. Once every six seconds, you’re able to authenticate your signals.
As far as receivers go, it turns out there’s actually some commercial receivers out there already that have the requisite parts. Some snapshot receivers take a snapshot of the RF. Think about the size of the picture that you take in your phone, and then send via text message. It’s pretty small. And the reason a lot of receivers already have this in there is they’re using it for jamming signature analysis. They’re using it as part of their acquisition engine and so again, a lot of them will already have the hardware in there. It just becomes a question of having signals available so that you can go off and do authentication.
To authenticate a signal, basically, it’s two parts: verify the data, so that’s a digital signature algorithm and then for ranging authentication, you basically collect RF snapshots, before the key’s republished, and then you look and see if the marker range equals the clear signal, right?
The signal is designed to operate in the mud. In other words, the nominal C0 that you get are quite high. This signal is designed so that if you can track it, you can authenticate it. There are more sophisticated processing algorithms than what I’m showing you here, but this is the basic performance of three very simple algorithms.
I’m going to argue that navigation message authentication is a step in the right direction, but it’s not sufficient. You need the watermarks too. There’s a lot of civil receivers that never read the data. And so they’re going to have to use some other method, preferably watermarks, in order to verify their location. And OSNMA does not provide a basis for proving location to remote users. And again, that is really the key problem to be solved. I don’t think it is a solved problem at this point, but watermarks are a move in the right direction.
All this will not be complete unless I talk a little bit about 5G. Positioning is an important thrust in support of connected vehicles and the Internet of Things. It’s an important business. In China they have 11 different ministries that are involved in this. They have allocated spectrum to go off and do this, and they are doing this as a key business thrust in 5G.
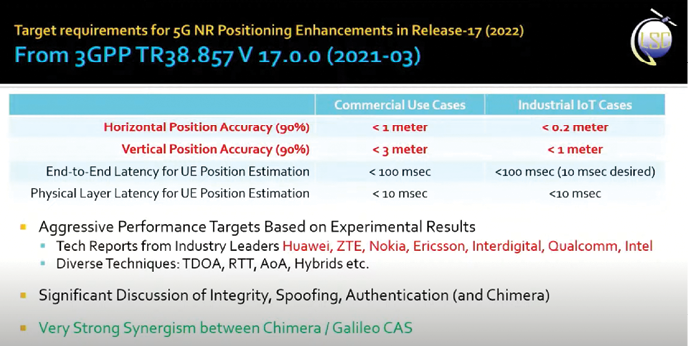
One of the things that has happened, if you take a look at the target requirements for 5G NR positioning enhancements in Release-17 (2022), this is basically what their objectives are in terms of accuracy: Horizontal position accuracy (90%), <1 meter commercial use case, <0.2 meter industrial IoT cases. Vertical position accuracy, <3 meter and <1 meter, respectively.
You’ll notice they’re pretty good. Now this is not signal-of-opportunity stuff. This is where you’re basically doing two-way ranging, you’re doing angle of arrival, lots of techniques there. These numbers are not some Cramer-Rao bound that some grad student computed, these are the kind of performance that they’re actually getting. If you look at who’s doing this, it’s Huawei, ZTE, Nokia, Ericsson, the usual people in 5G. And there’s very significant discussion of integrity, spoofing, authentication, and even Chimera, in this document.
Something that you should also be aware of is a very strong synergism between 5G and Chimera range authentication. I can’t go into details, but it’s there, trust me on this. There is something you can do to make this make the range authentications much more secure if you’ve got some of the 5G capabilities.
When you look at 5G, another thing to understand is that 3GPP, the base stations are basically software-defined radios. As such, whenever you do a major modification to the system, it’s not like you build out a whole bunch of infrastructure. You basically upload software. The 3GPP or the cellular industry has developed procedures for managing innovation and incorporating innovation over the years that is extremely effective. There’s basically a two-year major release cycle. A very important thing that’s going be happening next year or so is Release 17.
Software-Defined Receivers
If you want to understand SDRs as an evolutionary scale, here’s how it works. 3G first fielded in 2001, now being retired, typical data rate was around 384 kilobits per second. When we talk about 5G, the stuff that’s being deployed now, there is a factor of 26,000 improvement. That’s what a an SDR learning scale and evolutionary scale is all about. Much of it is done as a software deployment. In other words, there’s a way to evolve the system.
So as the Board is thinking about how to build a comprehensive strategy with regards to PNT, I’m going to argue that you really need to take this into account. This is deployed infrastructure. There are 417,000 cellular base stations out there and there is a $30 billion a year capital expenditure. They exceed GPS expenditures. When you look at the current deployments, coverage is not bad.
Now, a lot of people say yeah, but it’s got GPS dependencies. Well, yes, it does. It needs timing to an accuracy of about one microsecond. Not particularly challenging. You can get that from diverse GNSS sources. In other words, if GPS goes out for whatever reason, you can use other systems. It’s very unlikely all four systems will go out simultaneously.
So don’t discount 5G as a possible way to prove security. I know the Chinese are not. This is a major thrust in China.
Trouble with Current GPS Launches
Now I’m going to get myself in trouble. Parting recommendation, and this is going to be a little harsh. The greatest risk is taking insufficient risk. And I would argue that as a nation, one of the riskiest things we can do right now is to continue to launch satnav satellites that have a 15-year lifetime and do not have software-defined radio.
I spent the last six years designing signals for NTS3. I’ve had the privilege of working with a great team of people and have learned a tremendous amount about how to create secure systems, and how to create radio navigation systems that are very different than what we’re doing right now.
Just imagine that we had an SDR system on orbit. If something like Chimera or Galileo authentication came along, and we wanted to incorporate some feature, it’d be about 18 months to get the signal on orbit. And then after that, you go through a testing phase and so on, but you can respond to unforeseen needs. The Chinese are beginning to claim that their satellites have a capability to upload. What that actually means, I don’t know, but they may be SDRs.
Let’s contrast that with a situation where you don’t have SDR. Now you’re basically betting that you can see more than 20 years into the future. I don’t know about you, I’m good at this future stuff, but I’m not that good. I just can’t see that far into the future. I could argue that—this is where I’m really going to get trouble—if you don’t have SDR on orbit, you’re basically bringing a knife to a gunfight. That’s really the situation there.
When I look at the Chinese architecture, I’ve been following it for many years, it’s resilient. The reason it’s resilient is because it doesn’t have its basis in one single strong system. It’s a whole bunch of different systems, and it has an ability to be resilient. With that, I’ve probably got myself in a lot of trouble, but this is an honest assessment of where I see us in the United States right now.
Authors
Logan Scott has over 40 years of military and civil GPS systems engineering experience. He has been an active advocate for improved civil GPS location assurance for over 20 years and was the first to describe how civil navigation signals could be authenticated using delayed key concepts central to the Chimera signal. Logan is a Fellow of the Institute of Navigation and a Senior Member of IEEE. He is the author of Interference: Origins, Effects, and Mitigation in PNT21 and holds 46 US patents.




