A look at the four major categories of spoofing attacks and how Swift Navigation’s Skylark™️ Precise Positioning Service can mitigate against them.
Global Navigation Satellite Systems (GNSS) underpin modern positioning, navigation and timing (PNT), enabling precise positioning for applications ranging from aviation and autonomous driving to logistics and infrastructure monitoring. However, GNSS spoofing—a technique where attackers manipulate positioning data to mislead receivers—has become an increasing threat. Once considered a niche concern, spoofing incidents are now rising because of the availability of low-cost software-defined radios (SDRs), open-source spoofing tools, and their increasing use in geopolitical conflicts.
The impact extends beyond military targets and into commercial aviation, autonomous driving and logistics, where secure and reliable positioning is critical. Recent events underscore the severity of this issue. GNSS disruptions in Ukraine have reportedly been used to jam and mislead military drones and aircraft, as well as commercial vessels navigating the Black Sea. In the Middle East, airspace over Lebanon, Syria, Jordan and Israel has experienced GNSS anomalies, forcing pilots to switch to alternative navigation methods and raising concerns over aviation safety in the region.
While these attacks often target aerial and maritime navigation, their effects extend to ground-based positioning as well. GNSS-dependent systems—including autonomous vehicles, industrial robots, and fleet management solutions—can experience severe disruptions if spoofed signals cause drift, position jumps, or complete navigation failures.
To understand the full scope of GNSS spoofing, this article examines four major categories of spoofing attacks:
• RF spoofing at receivers: Directly misleading user devices.
• RF spoofing at Continuously Operating Reference Stations (CORS): Compromising reference stations to distribute false corrections.
• Correction data tampering: Intercepting and modifying correction streams.
• Server data injection: Injecting false GNSS observations into correction processing servers.
We will explore how GNSS correction services like Swift Navigation’s Skylark Precise Positioning Service play a vital role in mitigating spoofing attacks and securing navigation systems against the growing risk of signal manipulation. Skylark is a real-time, cloud-based GNSS correction service designed for accuracy, reliability and safety at a global scale.
Using proprietary atmospheric modeling, Skylark corrects GNSS errors caused by ionospheric disturbances, clock drift and orbital inaccuracies, improving positioning precision from several meters to just a few centimeters. Its carrier-grade network of reference stations is built and operated in partnership with mobile network operators who secure and maintain them as critical infrastructure, including their backhaul connectivity. By continuously validating satellite data and leveraging its secure, AWS-based cloud infrastructure, Skylark detects and rejects spoofed signals before they can impact users, ensuring robust and trustworthy positioning in contested environments.
Tap or hover to reveal how Swift detects and defeats spoofing attacks:
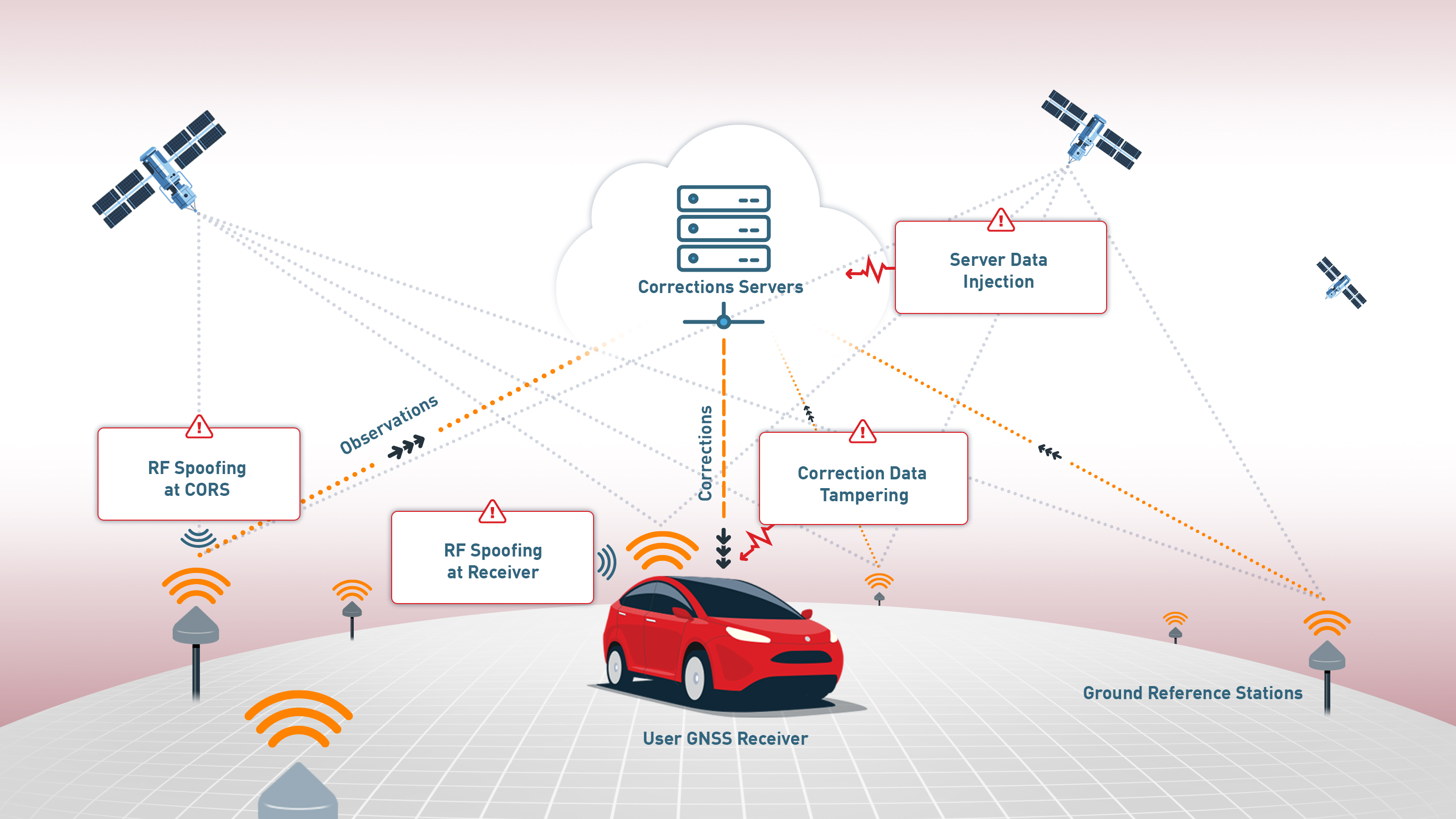
RF SPOOFING AT RECEIVER: DIRECTLY ATTACKING USER GNSS EQUIPMENT
Attack Overview
RF spoofing involves broadcasting counterfeit GNSS signals to override real satellite transmissions. This can mislead standalone receivers in vehicles, aircraft or mobile devices into computing incorrect positions.
The most basic approach is meaconing, a passive form of RF spoofing that replays genuine GNSS signals without modification. This technique does not require the attacker to generate satellite navigation data—only to record and rebroadcast it.
More elaborate approaches involve generating new, artificial GNSS signals rather than replaying old ones. This requires:
• Custom signal generation: Attackers must create satellite-like signals that match the expected structure while leading the receiver to a false position or time. This includes using the most up-to-date real ephemerides to maintain credibility.
• Real-time adaptation: To effectively spoof a moving target, attackers must continuously adjust the spoofed signal’s timing and Doppler shift, mimicking real satellite motion. Where motion sensors are included in an integrated solution, the spoofing must also mimic the actual motion of the target as observed by the sensors.
• Multi-frequency complexity: High-end receivers rely on multiple GNSS signals (L1/L2/L5, multi-constellation), making it exponentially more difficult to spoof all of them consistently.
Regardless of the method, RF spoofing typically involves amplifying the counterfeit signal to overpower authentic GNSS signals while also jamming unspoofed frequencies, forcing the receiver to track the spoofed signal.
Possible Defenses
• Authenticated ephemeris: Advanced correction services, such as Skylark, provide verified ephemeris data, allowing receivers to detect mismatches between real and spoofed signals.
• Sensor fusion: If GNSS-based velocity and position contradict IMU and odometry data, a sophisticated positioning engine, such as Swift Navigation’s Starling PE, will identify the inconsistency and report the event.
• Multi-constellation protection: Spoofing multiple GNSS systems simultaneously is extremely difficult. High-end receivers validate signals across multiple constellations, prioritizing trusted signals and rejecting anomalies.
• Future authentication measures: Services like Galileo Open Service Navigation Message Authentication (OSNMA) will allow receivers to cryptographically verify that ephemeris data originates from authentic satellites, making spoofing even more difficult.

RF SPOOFING AT CORS: ATTACKING GNSS REFERENCE STATIONS
Attack Overview
Instead of targeting a single user device, an attacker could spoof GNSS signals at a CORS used in correction services such as Real-Time Kinematic (RTK). This could result in the widespread distribution of erroneous corrections, impacting industries such as autonomous navigation, land surveying, and fleet management—
potentially causing significant financial and operational disruptions.
A compromised CORS also could enable more targeted attacks, such as misleading law enforcement tracking, manipulating high-frequency trading timestamps, or disrupting a competitor’s GNSS-based services.
An attacker can spoof a CORS by manipulating different aspects of the GNSS signals it receives. While large deviations in a station’s reported position are easily detected—because its location is fixed and known—more subtle attacks can be more difficult to identify. By modifying satellite ephemerides and clock data while keeping the CORS’s reported position unchanged, an attacker can introduce hard-to-detect errors that propagate through correction streams, misleading all users dependent on that station’s corrections.
Possible Defenses
• Position anomaly detection: Skylark can detect subtle deviations in a CORS reported position and will flag it as compromised.
• Automated station quarantine: Skylark isolates compromised stations from its correction model while maintaining performance through its network of redundant reference stations.
• Ephemeris voting mechanism: Skylark cross-validates ephemerides across its network of reference stations, rejecting outliers that do not align with network consensus.
• Continuous clock monitoring: Skylark tracks GNSS clock biases in real time; unexpected deviations trigger station quarantine to prevent bad corrections.
CORRECTION DATA TAMPERING: INTERCEPTING AND MANIPULATING GNSS CORRECTIONS
Attack Overview
Instead of spoofing RF signals, an attacker could intercept, modify or inject false GNSS corrections before they reach a receiver. This type of attack can introduce positioning errors without disrupting GNSS signals, making it stealthier than RF spoofing.
Corrections transmitted over unsecured channels, such as unencrypted IP connections or open radio links (e.g., RTCM over VHF/UHF), are particularly vulnerable. Attackers can:
• Block or delay corrections to degrade service (denial-of-service attack).
• Inject false corrections to subtly manipulate positioning solutions.
• Impersonate a legitimate correction provider to distribute incorrect data.
These attacks borrow heavily from cyber-attack techniques, including man-in-the-middle (MITM), packet injection and data spoofing. Just like RF spoofing of reference stations, correction data tampering can lead to significant financial and operational disruptions across industries that depend on high-accuracy GNSS, such as autonomous systems, precision agriculture and infrastructure monitoring.
Possible Defenses
• Encrypted corrections: Skylark secures correction data with encryption, preventing interception and modification by unauthorized parties.
• Authentication and integrity checks: Digital signatures ensure corrections originate from a trusted source and have not been altered in transit.
• Tamper-resistant transport: Skylark transmits corrections over secure, authenticated channels, reducing vulnerability to man-in-the-middle attacks.
• Fallback mechanisms: If corrections fail integrity checks, the receiver disregards them and switches to raw GNSS or dead reckoning.
SERVER DATA INJECTION: COMPROMISING GNSS OBSERVATIONS SENT FOR PROCESSING
Attack Overview
An attacker could inject false GNSS observation data directly into the servers responsible for computing corrections, leading to the widespread distribution of erroneous data. This network-based attack—distinct from RF spoofing—poses significant risks to industries reliant on high-precision positioning, such as
autonomous systems, construction and logistics. Correction services with weak cloud security and data integrity measures are particularly vulnerable.
Possible Defenses
• Secure cloud infrastructure: Skylark runs on Amazon Web Services (AWS), leveraging its built-in encryption, identity management, and network security to safeguard correction data.
• Diversified compute environments: Skylark concurrently uses ARM-based (Graviton) and x86 AWS instances, reducing the risk of single-architecture vulnerabilities.
• Geographically distributed redundancy: AWS Availability Zones provide fault isolation, preventing localized disruptions from affecting the entire correction network.
• ISO 26262-certified safety: Skylark complies with automotive safety standards, ensuring correction services remain secure and functionally safe under stringent reliability requirements.
CONCLUSION
GNSS spoofing is no longer a theoretical risk—it is a rapidly evolving threat that affects aviation, autonomous systems, logistics, and other industries that depend on precise positioning. As spoofing incidents rise due to geopolitical conflicts and the availability of low-cost tools, implementing robust countermeasures is essential to ensure accuracy, reliability and security in GNSS-based navigation.
Swift Navigation’s Skylark Precise Positioning Service is a proven solution for mitigating spoofing threats, delivering secure, high-accuracy GNSS corrections. By leveraging network-validated ephemeris, real-time anomaly detection and quarantining, encrypted correction streams, and a cloud-based security architecture, Skylark ensures trusted GNSS data—even in contested environments.
Available in three variants—Nx RTK, Cx and Dx—based on Virtual Reference Station (VRS) RTK, PPP-RTK, and Differential GNSS (DGNSS), Skylark is optimized for specific applications, balancing accuracy, coverage, complexity, and cost, with precision ranging from 1 cm to 1 meter. Trusted by leading automotive OEMs, Tier 1 suppliers, robotics companies, IoT system integrators, and mobile handset OEMs, Skylark powers more than 10 million Advanced Driver-Assistance System (ADAS) enabled and autonomous vehicles and devices worldwide.
Learn more about Skylark at swiftnav.com, and contact Swift Navigation for expert guidance on securing your precise positioning application in a spoofing-prone world.






