GPSPATRON has developed a system to monitor GNSS signals around specific areas of operation and issue user alerts to the presence of spoofing. The Lithuanian company, registered in the European Union, provides several anti-spoofing and anti-jamming products and services: GP-Cloud, GP-Probe, GP-Blocker and GP-Simulator.
Spoofing is a problem worldwide, but especially prevalent in the MidEast and regions around and in Russia, which regular employs spoofing for various purposes, among them to protect political leaders from potential drone or other attacks. Spoofing directed at such targets affects all receivers in the vicinity, including those used for surveying, vehicle navigation and critical infrastructure, so it is important, sometimes safety-critical, for all users to receive timely alerts to the presence of spoofing.
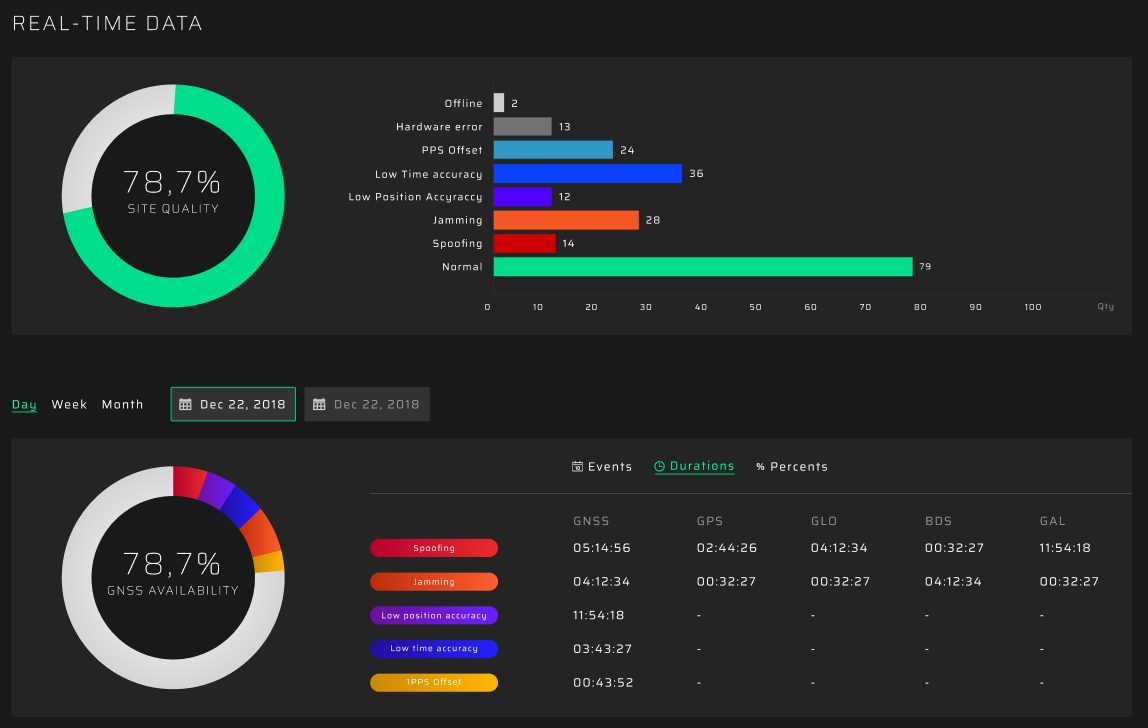
GPSPATRON’s method for detecting intentional coherent spoofing analyzes the spatial characteristics of the GNSS signal with a system of three-channel GNSS probes and a cloud service. GP-Probe measures GNSS signals with three RF channels, estimating the spatial signal parameters and transmitting raw data to the company’s GP-Cloud for real-time processing. GP-Cloud processes real-time data from GP-Probe, estimates the accuracy of time and position for all GNSSs, saves all signal parameters (SNR, pseudo-range, residual, phase, etc.) of each satellite to the database. If the parameters go beyond the set limits, users receive relevant notifications in real time. In case of failures of several elements of critical infrastructure, these customers will have the capability to analyze all stored data.
Generally, the company states, it can detect fake signals at a distance of a few kilometers, so it recommends placing GP-Probes every 1.5 kilometers in an area of interest, to ensure coverage, detection and alerts.
The company’s website contains a video explanation that differentiates the four types of possible spoofing attacks:
- Non-coherent or asynchronous
- Coherent or synchronous
- Coherent with multiple transmitters
- Meaconer
and explains why its solution requires three GNSS antennas to ensure the detection of all possible types of attacks. A second video demonstrates how a GNSS receiver behaves under synchronous and asynchronous attacks.
For time servers, the company also offers a GP-Blocker product to protect against high-power/military-grade GNSS spoofing. The GP-Blocker is an RF switch with 110 dB of RF isolation level and an embedded L-band GNSS jammer. The GP-Blocker is installed between the time server and its GNSS antenna. If GNSS spoofing is detected, GP-Blocker disconnects the GNSS antenna from the time server antenna port, the time server loses satellite signals, and switches to “Hold Over” mode. This maintains accuracy of the PPS signal under GNSS spoofing.
According to the company, spoofing is used widely in Russia to combat drones. Spoofing usually lasts a few to ten minutes. Anti-drone systems simulate the coordinates of the nearest airport, forcing the drones to land. GLONASS and GPS spoofing are always performed jointly. Galileo is blocked.







