 Equations
EquationsDuring the past two decades, the Global Positioning System, together with other GNSSes, has become an essential element of the global information infrastructure, with myriad applications in almost every facets of modern businesses and lifestyles, including communication, energy distribution, finance and insurance, and transportation. Ever-growing dependence on GNSS creates strong incentives to attack civil GNSS, for either an illegitimate advantage or a terrorism purpose.
During the past two decades, the Global Positioning System, together with other GNSSes, has become an essential element of the global information infrastructure, with myriad applications in almost every facets of modern businesses and lifestyles, including communication, energy distribution, finance and insurance, and transportation. Ever-growing dependence on GNSS creates strong incentives to attack civil GNSS, for either an illegitimate advantage or a terrorism purpose.
Unfortunately, security is not a built-in feature of GNSS open service. It has been known that low-received-power, unencrypted civil signals are vulnerable to jamming and spoofing attacks. Jamming is the intentional broadcast of a high-power “blocking” signal at the GNSS frequency. Hence, jamming is disruptive but usually detected by the receiver whenever it stops tracking satellites.
Unlike jamming, spoofing is a much more sophisticated attack. A spoofer intentionally broadcasts a counterfeit GNSS signal that overpowers the authentic signal so as to manipulate a victim receiver’s report-ed position, time, or both. Spoofing poses a greater security risk because it is deceptive and usually undetected by a Standard Positioning Service (SPS) receiver.
So far, a variety of methods have been proposed to harden civil GNSS receivers against spoofing attacks. These defensive methods can be generally categorized into three groups: external assistance, signal statistics, and cryptographic authentication. The first group performs consistency checks against metrics external to the GNSS subsystem, such as the information from inertial sensors, odometers, cellular networks, and high-stability clocks. The second group performs statistical tests on features inherent in GNSS signals, including angle of arrival, signal quality, signal power, and multipath. The third group relies on cryptographic, unpredictable information carried by GNSS signals. The Additional Resources section near the end of this article provides a list of some of the key papers and articles describing these various types of spoofing defenses.
Unlike the first group of methods, cryptographic methods need no additional hardware. In comparison to the second group, cryptographic methods enable users to differentiate authentic signals from counterfeit signals with higher confidence, especially in a complex environment where the statistics of authentic signals can be highly unstable.
Three types of cryptographic spoofing defense have appeared in recent literature. The first option, known as navigation message authentication (NMA), inserts public-key digital signatures into the navigation message. Another strategy is to interleave spread-spectrum security codes (SSSC) with normal civil GPS spreading codes so that parts of spreading sequences are periodically unpredictable.
Both NMA and SSSC require significant modifications to the legacy GPS signal structure. Consequently, they are unlikely to be implemented in the coming decade due to the static nature of GPS interface specification (IS) and long deployment cycles.
The third approach relies on codeless cross-correlation of unpredictable encrypted military P(Y) code between two civil GPS receivers. With little or even no modification to the GPS IS and the hardware of current GPS receivers, this approach is not only promising but also practical today. However, this approach in a centralized client-server approach requires dedicated reference stations at secure locations, which implies a considerable setup and maintenance cost.
This article will show that cross-correlation-based spoofing detection can be performed in a cooperative manner that incorporates information from other nearby GNSS receivers, without the requirement of high-quality, secure dedicated reference stations. The reliability arises from assistance provided by low-cost and even “unreliable” peers, which are voluntary but can be spoofed or dishonest.
Signal Authentication from Cooperative Peers
The cross-correlation spoofing detection borrows the idea from the dual-frequency GPS codeless receiver, which correlates the L1 and L2 P(Y) codes in order to find the differential delay between the phases of two codes. The spoofing detection basically correlates a snapshot of L1 signal from the receiver to be authenticated (hereinafter referred to as the “user receiver”) with a snapshot from the cross-check reference receiver; both snapshots are known to contain the same part of P(Y) code.
Although the P(Y) code is known by neither receiver and although its received version is noisy and may be distorted by a narrow-band RF front-end, a high correlation peak can still appear if neither receiver is spoofed or if both receivers are spoofed by the same spoofer. A low correlation peak appears when one of the receivers is spoofed and the other is not, or when both receivers are spoofed by different spoofers who counterfeit different P(Y) codes.
The signal authentication architecture proposed by S. Lo et alia and M. L. Psiaki et alia is in a centralized client-server approach, where each user receiver is served by a single dedicated reference receiver.
This architecture has several disadvantages. First and foremost, it requires considerable investment in the reference stations, not to mention the maintenance cost. Second, because a small number of reference stations is preferred due to cost considerations, the limited number of reference stations further limits the availability and robustness of the service, and also limits user capacity. Third, a limited number of reference stations at known locations are vulnerable to organized, targeted jamming and spoofing attacks, and loss of a majority of the reference stations could paralyze the authentication service.
Realizing these disadvantages, in this article we propose a GNSS signal authentication architecture in an ad hoc, cooperative approach. The fundamental difference from the centralized client-server approach is that our architecture uses multiple voluntary peers (hereinafter referred to as “ad-hoc cross-check receivers” or simply “cross-check receivers”) as references.
In our proposed authentication architecture, the signal received by the user receiver is checked against that received by each cross-check receiver. Each such check provides a “decision” as to the authenticity of the signal received by the user receiver, and an aggregation of these decisions leads to the final decision regarding the reliability or authenticity of the GNSS position.
The cooperative approach is superior to the centralized client-server approach in terms of cost, availability, user capacity, and robustness. However, one should be aware that each ad-hoc cross-check receiver is less reliable than a dedicated reference receiver. First, a mass-market GNSS receiver, especially one embedded in a smartphone, may not be as good as a dedicated geodetic-grade receiver in terms of the antenna and the signal conditioning circuit. Second, a cross-check receiver may be “dishonest” so that its authentication decision is falsified, even always opposite to the honest decision. Besides, a cross-check receiver can also be spoofed, and sometimes may be spoofed by the same spoofer if it is not sufficiently distant from the user receiver.
We shall further show in this article that our proposed approach is actually robust against these factors. In fact, the spoofing detection performance improves exponentially with the number of cross-check receivers involved in an authentication solution.
Candidate Structure of Authentication System
There are several approaches for implementing our proposed authentication system. These differ from one another mainly in where correlations are computed.
One approach is to distribute correlation computation to either cross-check receivers or a cloud service. Another option is to compute all the correlations in a centralized way, either by the user receiver itself or by a third party, which requires authentic position and/or clock information of the user receiver.
This section will present a candidate structure in which cross-check receivers compute the correlations. This structure is attractive because of its good privacy protection: the cross-check receivers need not release their collected snapshots of GNSS signals to anybody.
Figure 1 depicts a scenario of this structure, and the whole procedure is explained in detail in Table 1. In Figure 1, a user receiver wants to know whether its received signal is authentic or not; so, it randomly chooses N peers as cross-check references. The user receiver and all cross-check receivers agree to collect a snapshot of baseband GPS signal at a GPS time in the immediate future. The user receiver sends its snapshot to the reference receivers via secure channels. Then each reference receiver correlates its own snapshot with the one from the user receiver, and decides if the signal received by the user receiver is authentic or not. The user receiver collects the decisions from all three reference receivers, and finally determines the authenticity of its received signal by an appropriate statistical measure. Because snapshots of GNSS signals have to be transported over a communication network, a security protocol, such as transport layer security (TLS) or IPsec, is used to avoid man-in-the-middle attacks.
The authentication process can be performed in near real-time, and the time delay mainly depends on data collection, communication, and computation. According to M. L. Psiaki et alia, a snapshot of approximately one second is generally needed for reliable spoofing detection. A narrow-band GNSS front-end usually has a bandwidth of 2.4 megahertz, and one-second one-bit quadrature-phase samples yield 2.4 megabits of data.
Current 3G/4G cellular networks typically take one second or less to upload or download the data. The time of computation depends, but a rule of thumb is that a receiver must have the capability of processing one-second data within one second. Because the time required for sending/responding to requests and aggregating decisions is usually negligible, the authentication process can take as short as four seconds.
It is worth nothing that our cooperative authentication does not require highly reliable spoofing detection for each cross-check receiver and thus allows a much shorter snapshot to be collected. Therefore, four seconds is a very conservative estimate.
Analysis of Spoofing Detection Performance
Essentially a statistical hypothesis test, any spoofing detection has a probability of making two types of errors: false alarm and missed detection. This section is devoted to a rigorous analysis of the probability of these two types of errors in cooperative authentication.
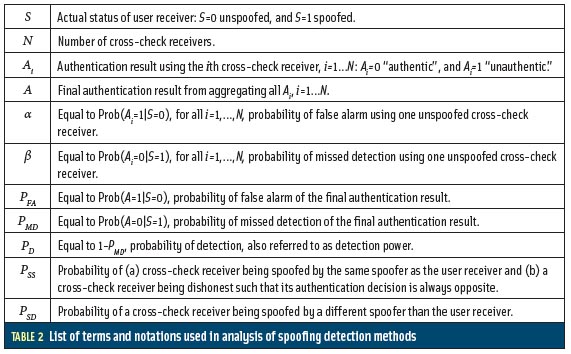
Assumptions and Notations. In order to simply the analysis, we assume that all ad-hoc cross-check receivers have the same detection performance, namely, the same probability of false alarm and the same probability of missed detection. Additionally, a cross-check receiver can be spoofed with a certain probability, and the spoofer can be the same as or different from the spoofer of the user receiver. Table 2 summarizes the notations used throughout this article.
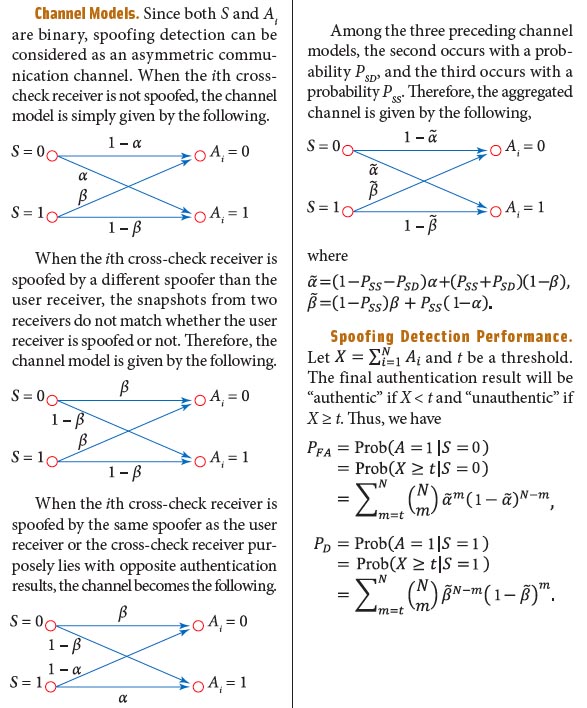
Channel Models. Since both S and Ai are binary, spoofing detection can be considered as an asymmetric communication channel. When the ith cross-check receiver is not spoofed, the channel model is simply given by the following:
See equations in the inset photo (above right), including Spoofing Detection Performance.
From the four preceding equations, we can see that PSD only affects PFA, while PSS affects both PFA and PD. Because PSS deteriorates performance more significantly than PSD, in practice it is wise to choose cross-check receivers far from the user receiver in order to reduce PSS.
Numerical Examples. We assume that α = 0.001 and β = 0.15 for the following reason. M. L. Psiaki et alia have shown that for a narrow-band GNSS receiver with an ideal ADC, a 0.4-second correlation interval leads to a detection power PD ≥ 0.95 when PFA = 0.0001 and C/N0 ≥ 40 dB-Hz. This is equivalent to α = 0.0001 and β = 0.05. In cooperative authentication, ad-hoc cross-check receivers may be of low cost and low quality. Therefore, α = 0.001 and β = 0.15 represent a reasonable and very conservative assumption.
Figure 2 shows the receiver operating characteristic (ROC) curves for two cases: all cross-check receivers are reliable (PSS = PSD = 0); cross-check receivers can be spoofed or dishonest with probabilities PSS = 0.1 and PSD = 0.1. Figure 2 shows that increasing the number of cross-check receivers always improves performance.
It can be seen that when cross-check receivers are spoofed with such large probabilities, four unreliable cross-check receivers are sufficient to match the performance of a single reliable, low-quality cross-check receiver, and seven can match a single reliable, high-quality reference receiver.
Figure 3 and Figure 4 show probability of missed detection and probability of false alarm, both as functions of the number of cross-check receivers. Four cases are considered in the figures: PSS = PSD = 0, PSS = 0.02 and PSD = 0.18, PSS = PSD = 0.1, PSS = 0.18 and PSD = 0.02.
From Figure 3 we can see that for a constant PFA, PMD decreases approximately exponentially with the number of cross-check receivers. Figure 4 shows a similar behavior. Even though the probability PSS = PSD = 0.2 is overly conservative, a modest number of cross-check receivers provides a sufficiently low probability of missed detection and false alarm.
Additionally, as foreseen in the previous section, PSS deteriorates performance more significantly than PSD.
Concluding Remarks
Secure, reliable position and time information is vital for many critical civil GNSS applications. This article has presented a signal authentication architecture that relies on a network of cooperative, low-cost receivers.
The civil GNSS signals, together with the encrypted military signals on the same frequency, are sampled by a user receiver and several ad-hoc cross-check receivers at the same time. The samples from the user receiver and each cross-check receiver are cross-correlated in order to detect spoofing. The spoofing detection results from all cross-check receivers are aggregated to reach a final decision regarding the authenticity of the signal received by the user receiver.
This article has validated the concept through a theoretical analysis. We have assumed the cross-check receivers can be spoofed or dishonest. The analysis and numerical examples have shown that the spoofing detection performance improves exponentially with the number of cross-check receivers.
A surprising and powerful aspect of the results is that with a modest number of cross-check receivers, each single cross-check receiver does not have to be high-quality, highly reliable, or highly robust to spoofing attacks.
Additional Resources
[1] Akos, D. M., “Who’s Afraid of the Spoofer? GPS/GNSS Spoofing Detection via Automatic Gain Control (AGC)”, NAVIGATION, Journal of The Institute of Navigation, Vol. 59, No. 4, Winter 2012, pp. 281-290
[2] Bardout, Y., “Authentication of GNSS Position: An Assessment of Spoofing Detection Methods,” in Proceedings of the 24th International Technical Meeting of The Satellite Division of the Institute of Navigation (ION GNSS 2011), Portland, Oregon, September 2011, pp. 436-446
[3] Daneshmand, S., and A. Jafarnia-Jahromi, A. Broumandon, and G. Lachapelle, “A Low-Complexity GPS Anti-Spoofing Method Using a Multi-Antenna Array,” in Proceedings of the 25th International Technical Meeting of The Satellite Division of the Institute of Navigation (ION GNSS 2012), Nashville, Tennessee, September 2012, pp. 1233-1243
[4] Dehghanian, V., and J. Nielsen, and G. Lachapelle, “GNSS Spoofing Detection Based on Receiver C/No Estimates,” in Proceedings of the 25th International Technical Meeting of The Satellite Division of the Institute of Navigation (ION GNSS 2012), Nashville, Tennessee, September 2012, pp. 2878-2884
[5] Dovis, F., and X. Chen, A. Cavaleri, K. Ali, and M. Pini “Detection of Spoofing Threats by Means of Signal Parameters Estimation,” in Proceedings of the 24th International Technical Meeting of The Satellite Division of the Institute of Navigation (ION GNSS 2011), Portland, Oregon, September 2011, pp. 416-421
[6] Humphreys, T. E., and B. M. Ledvina, M. L. Psiaki, B. W. O’Hanlon, and P. M. Kintner, Jr., “Assessing the Spoofing Threat: Development of a Portable GPS Civilian Spoofer,” in Proceedings of the 21st International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS 2008), Savannah, GA, Sep 2008, pp. 2314-2325.
[7] Lo, S., and D. De Lorenzo, P. Enge, D. Akos, and P. Bradley, “Signal Authentication: A Secure Civil GNSS for Today,” Inside GNSS, September/October 2009
[8] Pini, M., and M. Fantino, A. Cavaleri, S. Ugazio, and L. Lo Presti, “Signal Quality Monitoring Applied to Spoofing Detection,” in Proceedings of the 24th International Technical Meeting of The Satellite Division of the Institute of Navigation (ION GNSS 2011), Portland, OR, Sep 2011, pp. 1888-1896
[9] Psiaki, M. L. , and B. W. O’Hanlon, J. A. Bhatti, D. P. Shepard, and T. E. Humphreys, “GPS Spoofing Detection via Dual-Receiver Correlation of Military Signals,” to appear in IEEE Transactions on Aerospace and Electronic Systems.
[10] Scott, L., “Anti-Spoofing & Authenticated Signal Architectures for Civil Navigation Systems,” in Proceedings of the 16th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GPS/GNSS 2003), Portland, Oregon, September 2003, pp. 1543-1552
[11] Wesson, K., and M. Rothlisberger and T. E. Humphreys, “Practical cryptographic civil GPS signal authentication,” NAVIGATION, Journal of the Institute of Navigation, Vol 59, Num 3, 2012, pp 177-193