A look at the performance of the Galileo E1-B Open Service Navigation Message Authentication (OSNMA) in various scenarios, elucidating its logic and workflow and shedding light on its functionality and intended purpose.
ALI PIRSIAVASH, ALI BROUMANDAN AND SANDY KENNEDY HEXAGON’S AUTONOMY & POSITIONING DIVISION
Given their low power and public structure, civilian GNSS signals are susceptible to any in-band interference and counterfeit signals, thus need to be protected. GNSS cryptographic protection involves encryption and/or authentication techniques to safeguard GNSS signals from being used by unauthorized users or manipulated by counterfeit transmitters. Galileo Open Service Navigation Message Authentication (OSNMA) is a prominent example of GNSS authentication.
In OSNMA, corresponding data is embedded within the Galileo I/NAV message transmitted over the E1-B open service signal. This process uses message authentication codes generated with a key that is broadcast with some delay. The key is part of a pre-generated, one-way chain whose root can be publicly verified and is transmitted in reverse order of its generation. Enabling OSNMA as a security feature necessitates the essential cryptographic functions to validate the received secret keys, retrieve the authentication codes and verify the authenticity of the navigation data, which is not trivial to implement.
How Does OSNMA Work?
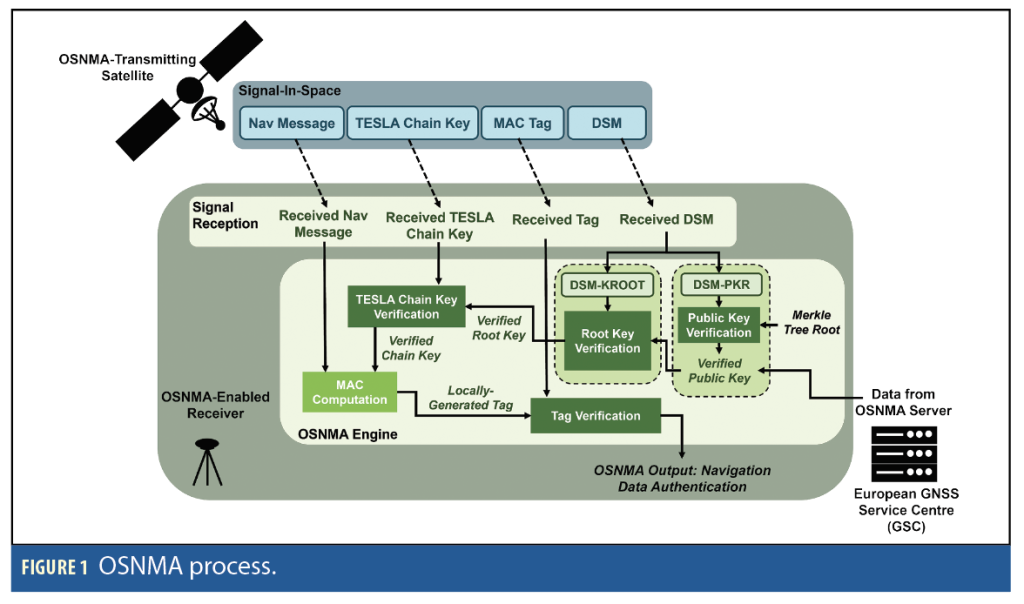
Figure 1 provides a high-level illustration of the OSNMA process, based on the Timed Efficient Stream Loss-tolerant Authentication (TESLA) protocol where the authenticating key is broadcast with delays for all satellites, enabling auto- and cross-authentication of data from different satellites.
The OSNMA data is broadcast within the reserved bits embedded in the odd page parts of a nominal Galileo E1-B I/NAV message, consisting of an 8-bit Header and Root Key (HKROOT), and a 32-bit Message Authentication Code and Key (MACK). During a nominal sub-frame, 15 pages are transmitted every 30 seconds to build up a set of 120-bit HKROOT and 480-bit MACK messages. HKROOT provides a Digital Signature Message (DSM) containing the Public Key Renewal (PKR) and Root Key (KROOT) information. MACK messages include the TESLA chain key and the authentication tags used to verify the authenticity of the navigation data [1-4].
At the receiver end, the process may be initialized by retrieving and verifying the public and root keys depending on the stored information available when the receiver starts. When the public and root keys are not available, the receiver must retrieve them, either directly from the European GNSS Service Center (GSC) OSNMA server or using the Galileo Signal-In-Space (SIS) and DSM-PKR message. In the latter case, the public key is verified using the Merkle root, as detailed in the Galileo OSNMA Receiver Guidelines [1].
The verified public key is used to verify the TESLA root key and associated chain parameters, sent in the DSM-KROOT message. The verified TESLA root key can then be stored and used for the verification of the TESLA chain keys broadcast within the MACK message. Once the chain key is verified, the OSNMA module takes parts of the navigation message to generate a local replica of the authentication tag to be matched with the one received from space and determines the authenticity of the taken navigation message.
More details on OSNMA message structure and retrieval, and the authentication process can be found in the Galileo OSNMA User Interface Control Document (ICDs) and Receiver Guidelines plus other scientific papers and reports published by the European Union [1-4].
Putting OSNMA to the Test
A prototype implementation of OSNMA was investigated across a variety of static and kinematic field tests to evaluate the availability and reliability of the authentication service under different authentic and inauthentic scenarios. The following OSNMA results are color-coded. Blue refers to the events where authentication cannot be performed due to the lack of valid data required for OSNMA verification. This is usually the case in a cold start when the receiver is still waiting to receive data and set the crypto parameters. This also can be the case in satellite rise and fall or when OSNMA data reception is interrupted and does not include all the information required for authentication.
Yellow and red indicate events where all data required for OSNMA (authenticating data and that to be authenticated) is available, but verification fails. This may happen when the navigation message is corrupted and cannot be corrected due to the propagation environment or interference, or an unauthorized signal with either invalid OSNMA data or an invalid navigation message is being received. Green designates events where all data required for OSNMA is available and authentication is verified.
To quantify the availability of the OSNMA service across various environments, the occurrence percentile for each authenticity event is computed. This percentile is determined by dividing the number of event occurrences by the total number of OSNMA epochs where the navigation message is accessible, and Galileo satellites are within the receiver’s view and being tracked at the end of the 30-second OSNMA subframe. In an authentic scenario, the green or “authenticated” event percentile serves as a metric for OSNMA service availability, indicating when a receiver can rely on the navigation message in its navigation solution or for any other potential application.
Static Test in Open Sky
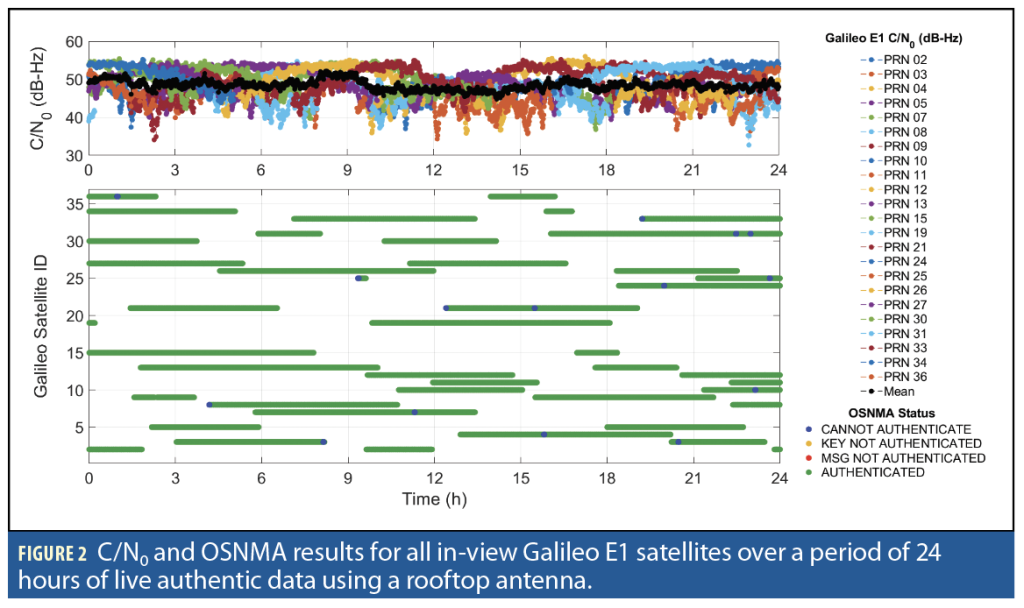
The OSNMA solution was first tested over 24 hours of open-sky live authentic data to set a benchmark for its nominal performance. The receiver antenna was a GNSS-850 antenna from Hexagon|NovAtel located on a rooftop in Calgary, Alberta, Canada under open-sky, low-multipath conditions.
In the top panel of Figure 2, the Galileo E1 Carrier-to-Noise density ratio (C/N0) values are shown for all satellites in view under a 5-degree elevation cut-off angle. The average C/N0 over all tracked satellites of Galileo E1 signals is shown in black and is above 45 dB-Hz for almost the entire time. The bottom panel presents the corresponding OSNMA results for a tracking receiver (no initialization) connected to the rooftop antenna.
Except for some sparse epochs, mainly in the cross-authentication or fall and rise of the satellites, the navigation message is authenticated with 99.87% availability and no yellow or red flags.
Kinematic Test Across Environments
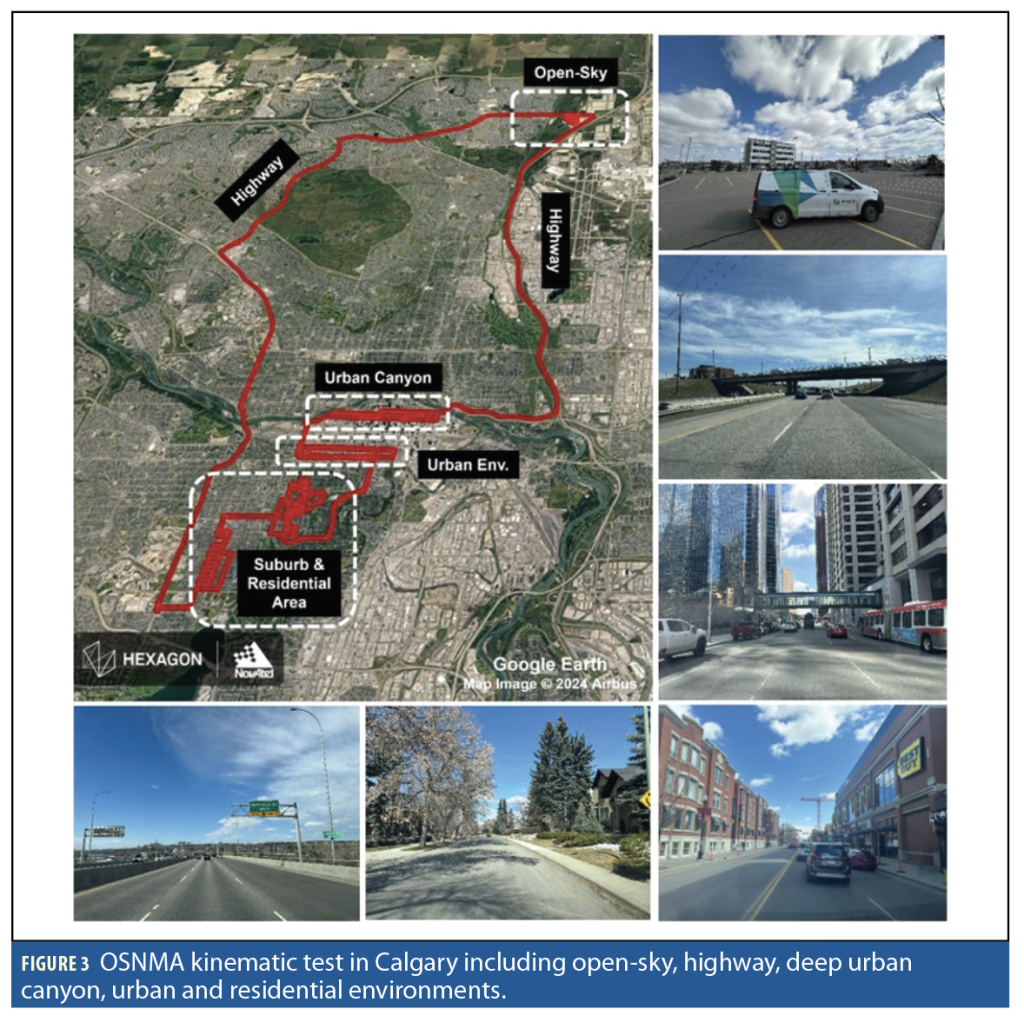
In a kinematic test, the availability of OSNMA service was examined under various conditions and environments, as illustrated in Figure 3. The data collection campaign involved a 5-hour test drive conducted in Calgary, using an OSNMA-enabled receiver connected to a GNSS-850 antenna mounted on a test van.
The test commenced in open-sky conditions and progressed through highways, traversing into deep urban canyons within downtown Calgary, urban areas, and residential neighborhoods. On the return route, the test vehicle retraced similar highway paths and ended up with the same open-sky conditions once again. The highway segment of the test predominantly featured open-sky conditions interspersed with overpass bridges and a mix of suburban and urban environments at one end.
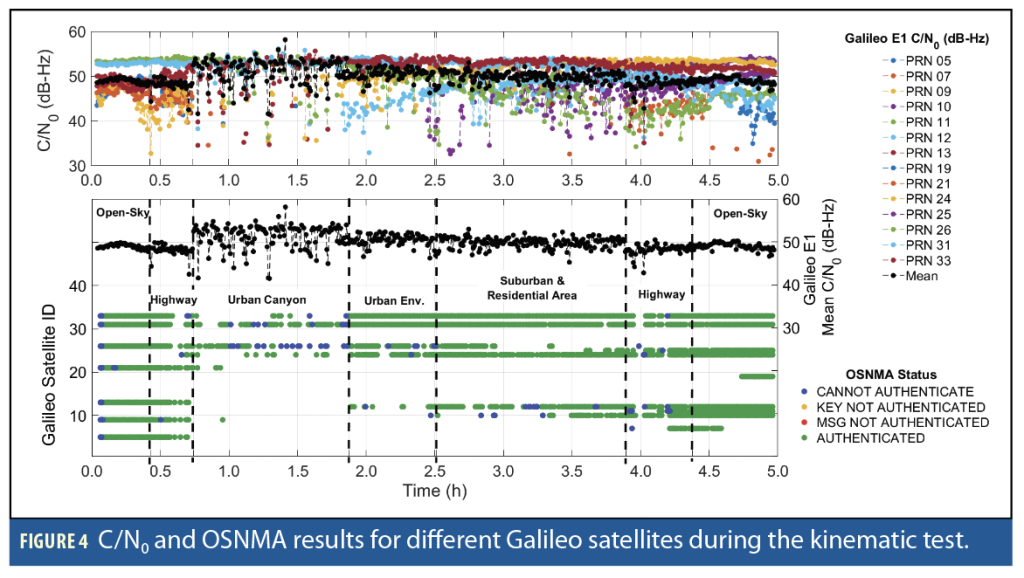
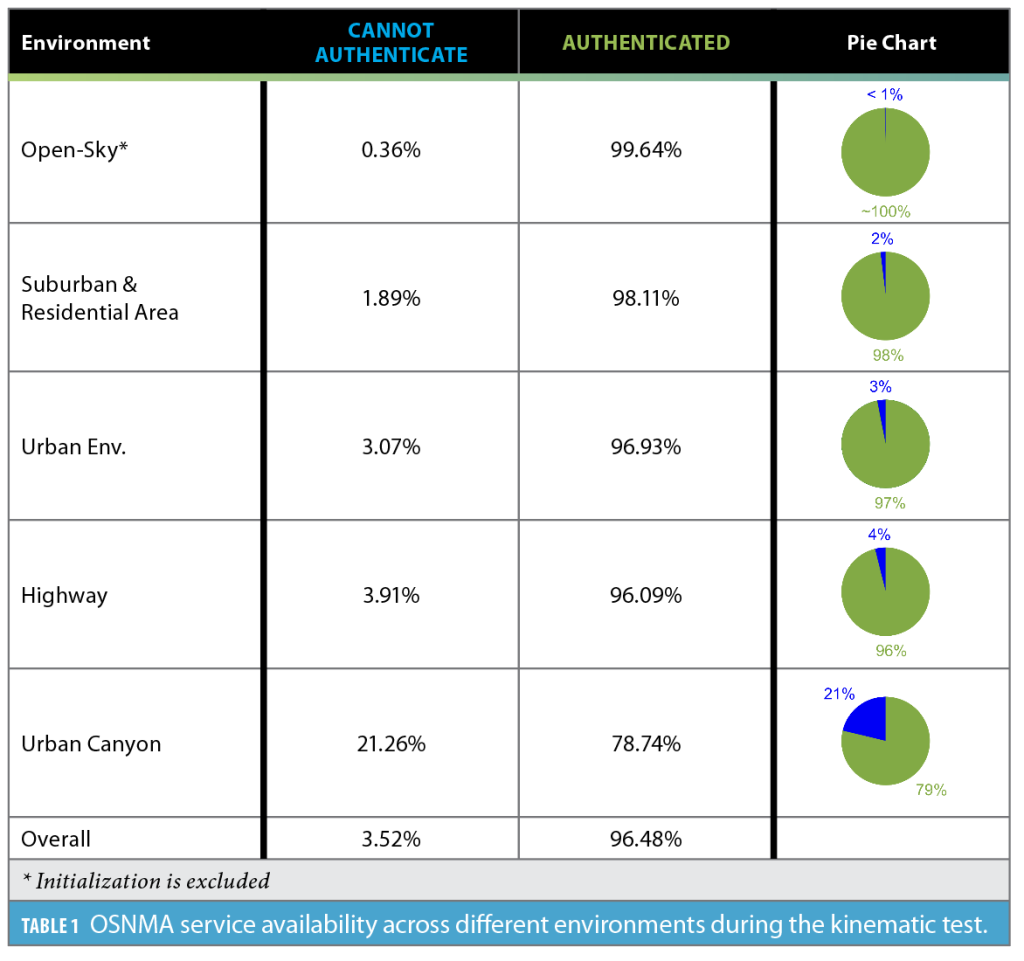
Figure 4 shows the C/N0 values and corresponding OSNMA results for different Galileo satellites. OSNMA service availability percentages are listed in Table 1. At greater than 99% availability with no red or yellow flags, the availability for the open-sky conditions matches the results from the rooftop test. Less than 1% of the open-sky events were blue covering satellite rise and fall, and OSNMA data interruptions.
The OSNMA availability decreases slightly from residential and suburban to urban environments but is in an acceptable range of 97% to 98%. Highway test shows slightly lower availability due to signal interruptions caused by overpass bridges. In the downtown area with an urban canyon structure, the availability drops to less than 79%, with about 21% blue flags when the receiver did not have all the information to proceed with navigation message verification.
Jammertest 2023
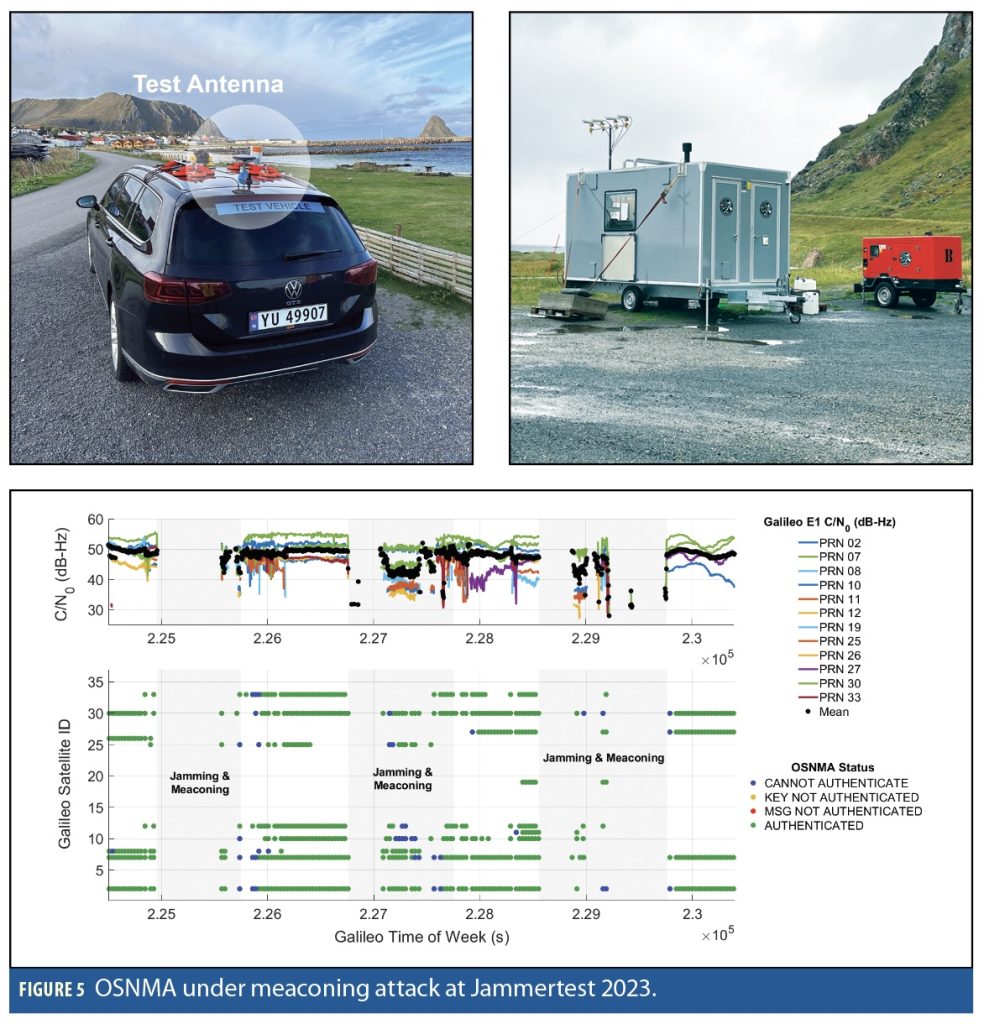
OSNMA performance was further assessed during the Norwegian jamming and spoofing trial Jammertest, which took place in September 2023 at Bleik in Norway. This live over-the-air broadcast testing event encompassed a wide range of jamming and spoofing scenarios. These included several instances of spoofing attacks on Galileo E1, featuring synthetic ephemerides and/or manipulated OSNMA data fields, thereby facilitating the evaluation of the prototype OSNMA implementation. A comprehensive discussion of the results can be found in [5].
Throughout the test, whenever the navigation message or OSNMA data bits were synthesized, OSNMA effectively alerted the receiver to these inauthentic events [6]. However, during meaconing or spoofing attacks involving broadcast (true) ephemerides, the designed OSNMA, lacking any auxiliary time consistency check, provided the receiver with a green light for the authenticity of the navigation message, consistent with expectations.
Figure 5 provides an example of a meaconing attack scenario, where the spoofer tracks genuine GNSS signals and retransmits them to gain control over nearby receivers’ tracking loops. The test vehicle used the GNSS-850 antenna connected to an OSNMA-enabled receiver from NovAtel. Figure 5 also presents the C/N0 values of Galileo E1 signals alongside the corresponding OSNMA results for each satellite.
The meaconing events commenced with a high-power jammer, causing the receiver to lose track of any signals in the L1 band. Following the jamming event, the meaconing attack was applied and the receiver switched to tracking the replayed GNSS signals for most of the time when the signal power gradually decreased by about 10 dB [5].
As shown in Figure 5, the availability of the OSNMA service was significantly degraded during the attacks. Because navigation data is entirely replicated from an authentic source in a meaconing attack, wherever meaconing signals were tracked by the receiver, the navigation message was reported as authentic, except for the epochs where spoofing interference interrupted the reception of OSNMA-required data (blue) and thus the receiver raised the blue flags.
Although this is the expected behavior of the OSNMA module correctly validating the authentic navigation data, the position solution was spoofed. OSNMA, as indicated by its name, is designed to check for the authenticity of the navigation message as an asset embedded in GNSS signals, but not to be a spoofing detector for all scenarios.
Availability and Reliability of OSNMA
OSNMA protects navigation messages by making them unpredictable at a high level of security and affordable complexity. OSNMA is compatible with existing GNSS signals by exploiting leftover reserved bits and is tenable for civil applications as it monitors the validity of the received chain keys over a publicly known key verification technique. It has a flexible design that is optimized by using the same chain key for all satellites, allowing the cross-authentication of data transmitted by other satellites and improving the general availability of the service under different scenarios. However, there are limitations associated with OSNMA performance. Service availability and reliability are the main issues presented in this article. A more inclusive discussion on OSNMA benefits, challenges and limitations can be found in [7].
Availability Concerns
OSNMA exploits a limited number of reserved bits embedded within the navigation message, thus requires data accumulation to realize the verification process. This makes the availability of the OSNMA service vulnerable to dense and degraded environments when the reception of signals and data decoding are interrupted more frequently.
While the OSNMA service was shown to be available most of the time in open-sky, suburban and urban scenarios, its availability can drop to 80% in dense urban canyons. While this might not pose a problem in many applications because the receiver may be able to revert to the last validated set, it could be a concern for receivers operating in dense environments over an extended period. In general, for receivers connected to a network and running in challenging GNSS environments, decoding navigation data from live data may not be plausible due to lower availability and longer time to fix. An alternative solution for such applications could involve employing an assisted GNSS approach, which accesses navigation data from alternative sources.
Furthermore, given that OSNMA is presently confined to the L1/E1 band, in the event of E1 band jamming, a receiver will be unable to obtain the authentication data broadcast on the Galileo E1-B INAV message, as demonstrated in the Jammertest. In such situations, the receiver won’t be able to rely on signals from the E5 and/or E6 bands (without available NMA service) for position/time solutions.
Reliability Concerns
The navigation message is a critical part of the Positioning, Navigation and Timing (PNT) solution and once it is decoded and authenticated, it is trustworthy and can be used for hours. However, verifying the navigation message does not ensure the authenticity of the range or navigation solution.
As presented in Jammertest, a major concern includes meaconing and non-navigation message-based spoofing attacks, where authentic signals are re-broadcast or authentic navigation messages are recorded and replayed by spoofing signals to create an intended position/time offset. In this case, a stand-alone OSNMA module would validate the navigation data while the navigation solution could be spoofed. For an OSNMA-enabled receiver, however, the transmit time cannot be altered by the spoofer, so the whole spoofing process has to be fast (e.g., within a few milliseconds), otherwise, the imposed time-offset could be potentially detected by a tracking receiver or by a receiver with access to an external source of time information.
As a solution, navigation message authentication can be supplemented by other spoofing detection and
authenticity verification techniques. A Spreading Code Authentication (SCA) is proposed, where the spreading code can be generated by expanding the digital signature of the navigation message into pseudorandom bit sequences, known as public SCA [8]. Unlike both the intended user and the potential spoofer, the transmitting satellite possesses the complete navigation message and digital signature beforehand, allowing it to compute and transmit the spread spectrum security codes.
Summary
Besides the processing loads and implementation burden, OSNMA provides a certain level of integrity and reliability for civilian users by protecting navigation messages from being invisibly forged by an unauthorized party. However, OSNMA’s performance is influenced by the surrounding environment. While OSNMA shows promising results across most authentic scenarios, its availability degrades in dense and obstructed environments such as urban canyons.
As shown, a stand-alone OSNMA solution is also vulnerable to meaconing and low-latency record-and-play spoofing attacks, but when paired with other measures, it can contribute to a resilient PNT solution. In a nutshell, with limitations in service availability and detecting non-navigation message-based spoofing attacks, OSNMA on its own may appear insufficient for integrity-assured navigation, but it still offers a rigid complementary layer of protection to be accompanied by other security features and monitoring techniques for full protection.
References
(1) Galileo Open Service Navigation Message Authentication (OSNMA) Receiver Guidelines. (January 2024). Issue 1.3, European Union.
(2) Galileo Open Service Navigation Message Authentication Internet Data Distribution Interface Control Document (OSNMA IDD ICD). (July 2023). Issue 1.0, European Union.
(3) Galileo Open Service Navigation Message Authentication (OSNMA) Signal-In-Space Interface Control Document (SIS ICD). (December 2022). Issue 1.0, European Union.
(4) European GNSS (Galileo) Open Service Signal-In-Space Interface Control Document (OS SIS ICD). (January 2021). Issue 2.0, European Union.
(5) Broumandan, A. Pirsiavash, A. Tremblay, I., & Kennedy, S. (2024). Hexagon | NovAtel’s Jamming and Spoofing Detection and Classification Performance During the Norwegian JammerTest 2023. Proceedings of the 2024 International Technical Meeting of The Institute of Navigation, 23-25 January, Long Beach, California, pp. 467-480.
(6) Pirsiavash, A., Broumandan, A., & Kennedy, S. (2024). OSNMA: A Step Toward Multi-Layered GNSS Security. Hexagon’s Autonomy & Positioning division’s Velocity Magazine 2024.
(7) Pirsiavash, A., Broumandan, A., & Kennedy, S. (2024). Galileo Open Service Navigation Message Authentication (OSNMA) Benefits, Challenges, and Limitations. Proceedings of the 37th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2024), 16-20 September, Baltimore, Maryland.
(8) Hein, G. W., Kneissl, F., Avila-Rodriguez, J. A., & Wallner, S. (2007). Authenticating GNSS Proofs against Spoofs Part 2. Inside GNSS+, Sept/Oct 2007, pp. 71-78.
Authors
Ali Pirsiavash is a research associate at Hexagon’s Autonomy & Positioning division and has over 10 years of academic and industrial experience in telecommunications and satellite-based navigation systems. He earned his Ph.D. in Geomatics Engineering from the University of Calgary in 2019, specializing in Positioning, Navigation, and Wireless Location. He also received B.Sc. and M.Sc. degrees in Electrical Engineering, specializing in Communication Systems, from K. N. Toosi University of Technology in 2008 and 2011, respectively. Ali’s current research interests include signal processing and receiver design for precise and resilient GNSS applications.
Ali Broumandan is a principal research associate with Hexagon’s Autonomy & Positioning division. He leads the resilient PNT team in the applied research group, which focuses on improving GNSS receivers’ performance in challenging operational environments. Ali received his Ph.D. degree from the Geomatics Engineering Department at the University of Calgary in 2009. He has over 20 years of experience in signal processing focusing on positioning, navigation and timing applications.
Sandy Kennedy is vice president of innovation at Hexagon’s Autonomy & Positioning division. She is responsible for directing applied research activities to support the vision of: Autonomy and Positioning–Assured. Drawn to the University of Calgary for its Geomatics Engineering program (and proximity to good ski hills), she completed both her B.Sc. and M.Sc. degrees in 2000 and 2002, respectively. During her time in R&D at NovAtel and Hexagon A&P, she has had fascinating experiences developing leading-edge positioning technology and working with a diverse, global customer base. Her experience includes GNSS/INS integrated systems, GNSS receiver design with an emphasis on both precision and resilience, and precise multi-frequency multi-constellation positioning.






