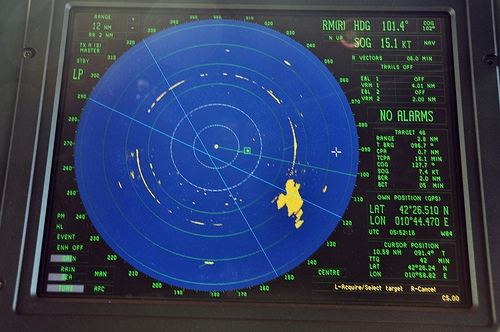
 The spoofed route of the White Rose of Drachs was not detected on the ship’s navigation monitors. Photo courtesy of University of Texas at Austin
The spoofed route of the White Rose of Drachs was not detected on the ship’s navigation monitors. Photo courtesy of University of Texas at AustinIn a startling experiment a research team from the University of Texas successfully spoofed a ship’s GPS-based navigation system sending the 213-foot yacht hundreds of yards off course — without raising alarms or triggering a hint of the course change on the onboard monitors.
In a startling experiment a research team from the University of Texas successfully spoofed a ship’s GPS-based navigation system sending the 213-foot yacht hundreds of yards off course — without raising alarms or triggering a hint of the course change on the onboard monitors.
Led by assistant professor Todd Humphreys, the group used equipment that started as a faint ensemble of civil GPS signals. Those signals gradually increased in strength until they overpowered the true GPS signals, enabling them to fool the ship’s navigation system. The team sent the ship through a series of subtle maneuvers that ultimately put it on a parallel course hundreds of meters off its intended track.
“The ship actually turned and we could all feel it, but the chart display and the crew saw only a straight line,” Humphreys said.
The equipment for the newly revealed experiment, which took place in June aboard the 213-foot superyacht White Rose of Drachs as it traversed the Mediterranean Sea, was set up on the ship’s upper deck, Humphreys told Inside GNSS. The equipment was there the entire time but, he stressed, that was really just a matter of convenience.
“We could have executed the same attack over the air from miles away,” Humphreys said. “Ultimately, we’re only limited by the curvature of the earth, because our spoofing signals want to go in straight lines. Power is not a problem — the authentic signals are so tenuous that it’s easy to overpower them even with a small amplifier.”
Humphreys led a team a year ago that used a similar technique to spoof an unmanned aerial vehicle or drone, directing it to fly lower than is was supposed to. Though successful, the spoof was hard to sustain because, once the drone dipped, it was difficult to hold the line of sight the spoofing equipment required.
“It’s easier to spoof a ship — even from a distance” said Humphreys, “because it’s easier to track the ship, and keeping continuous track of the ship’s true location allows the spoofer to not only confuse the ship, but to redirect it along a path the spoofer dictates. In other words, for precise control of the target ship, you’ve got to know its true position and velocity at all times, and a standard radar package will be adequate for this. It’s hard to track small or medium-sized UAVs on radar, so it’s hard to know their true position and velocity.”
Chandra Bhat, director of the Center for Transportation Research at The University of Texas at Austin, said that the experiment underscores the vulnerability of the transportation sector to such attacks.
“The surprising ease with which Todd and his team were able to control a (multimillion) dollar yacht is evidence that we must invest much more in securing our transportation systems against potential spoofing,” Bhat said in a statement.
Multi-Modal Spoofing
“This experiment is applicable to other semi-autonomous vehicles, such as aircraft, which are now operated, in part, by autopilot systems,” Humphreys said, in a statement. “We’ve got to put on our thinking caps and see what we can do to solve this threat quickly.”
An FAA study group put together last fall to investigate the problem of spoofing for aviation is “just the right thing to do,” Humphreys told Inside GNSS. He said he was also impressed with work being done by the GPS Directorate to see what it would take to add light cryptographic signatures to the civil signals.
“It would have been easy for the Directorate to say ‘It’s a civilian issue, so it’s not our problem.’ Instead, the Directorate is stepping up and devoting at least a small amount of funds and time to it,” he said.
He was less impressed with the response from the Department of Homeland Security. While noting the “extraordinary” work of individuals at the agency, such as John Merrill, he deemed the agency’s response overall to be “disappointing.”
“Last year, DHS claimed that UAV vulnerability to GPS hacking wasn’t their problem,” Humphrey’s said. “But GPS pervades all modes of transportation and is woven throughout our critical infrastructure. After this recent experiment, it will be harder for DHS to complain that it’s some other agency’s problem.”
Could Encourage New Receiver Designs
Receiver and signal expert Tom Stansell of Stansell Consulting deemed the ship-spoofing experiment “very, very valuable” in terms of getting the GPS community to think more fully about the problem. Customer interest in spoof-proof receivers generated by the experiment could spur manufacturers to step up with modifications to receiver software and hardware that solve the problem, he said, while avoiding the complexities of a major government effort.
One practical change, he suggested, would be a two-antenna receiver. “There’s a way of comparing the signals, if there are two antennas, and determining if you’re being spoofed or not.”
This approach would add some cost, Stansell noted, “but if you are a cruise ship (operator) worried about something like that, it would be a trivial expense. If you are an outboard motor enthusiast my guess is you probably wouldn’t worry about being spoofed anyway.”
For aircraft it would be possible to compare incoming GPS results to those of the inertial system or other inputs to see if a spoofing attack was underway, Stansell said. But people should not be afraid to fly today even if it takes time to work out solutions. Spoofing an aircraft is “close to impossible.”
“Receivers need to be suspicious,” said Logan Scott, a Colorado-based consultant and expert in radio frequency signal processing and waveform design. “When it comes to spoofing, most receivers are incredibly naïve; they blindly accept anything that looks like a GPS signal as being valid. Validating signals and establishing situational awareness is the key.”
Logan said receivers should be crafted to look for signal artifacts that shouldn’t be there and — as more GPS signals such as L5 and L1C become available and signals from GLONASS, BeiDou and Galileo come online — they should check those signals against each other for consistency.
At a systems level, he suggested, there should be a check for agreement between sensors with uncorrelated vulnerabilities. “We might look for agreement between GPS results, IMU results, atomic clock time, eLoran, and so forth,” Scott wrote in the current issue of Inside GNSS. “These last are potent because . . . they can’t be spoofed by the same measures being directed toward the GNSS receiver.”
Humphreys agreed that people should be on the lookout for discrepancies and said autopilots should be re-configured to not rely solely on GPS. But it is important, he added, that the public and policymakers understand that spoofing poses a threat that has far-reaching implications for transportation.
As things stand now, he said, “all commercial GPS receivers are spoofable.”
As part of an ongoing research project, funding and travel expenses for this latest spoofing experiment was supported by UT Austin’s Wireless Networking and Communications Group through its Industrial Affiliates program.