Recent presentations and publications have suggested that multi-frequency spoofing is infeasible using low-cost, off-the-shelf equipment, and that a good defense against any but well-funded and technically competent adversaries would be to use a multi-frequency capable survey grade receiver. The authors of this article wish to demonstrate that this is definitively false.
Authors: James T. Curran Independent Researcher Aiden Morrison Sintef Digital Cillian O’Driscoll Consultant
“It doesn’t have to be pretty, it just has to work”
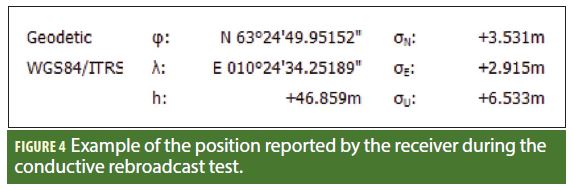
The spoofing of GNSS signals is a controversial and divisive topic within the satellite navigation community. Some believe that spoofing is virtually infeasible, while other industry insiders believe that spoofing is actually trivial. Referring to Figure 1, we present an example of a survey grade receiver, reporting that it is tracking each of L1 C/A, L2C, L1P(Y), L2P(Y) signals and generating a valid position solution in Norway while it is actually sitting on a desk in the Netherlands being fed a spoofed signal from an low-cost off-the-shelf “single frequency” software defined radio. Contrary to other assertions, it was possible to perform this using only 12 megahertz of instantaneous broadcast spectrum. This resulted in no measurable code-carrier divergence, nor was the spectrum quite as obviously distorted as has been suggested. Given that these apparently reasonable assumptions (that multi-frequency spoofing required a “multi-frequency” signal generator, and that spoofed signals will have obvious imperfections), were demonstrated to be unfounded, then we should perhaps revise our assumption, and reconsider our approach to the problem. 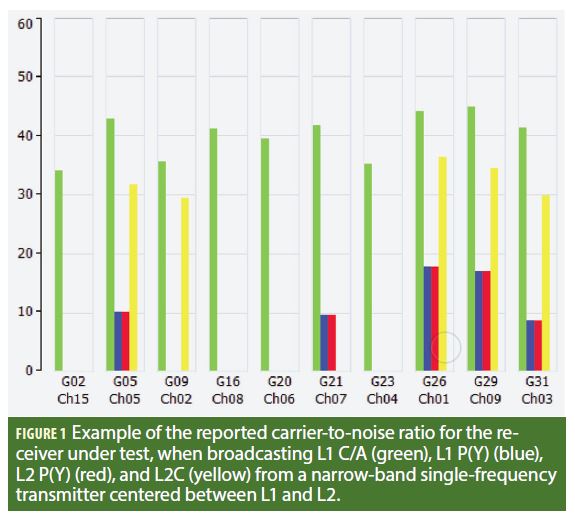
Background
The reliability of radionavigation equipment and the trust that can be placed in its correct functioning has become of increased importance as ever more aspects of modern infrastructure and civilian services have become dependent on it. Systems and techniques aimed at providing robustness or resilience against the malicious adversary come in a variety of forms: some are based on the augmentation of the receiver with sensors that are deemed inaccessible to the remote adversary, including inertial, odometer barometer sensors; some are based on spatial-signal processing techniques, including multi-element or synthetic-aperture antennas; some are based on signal fidelity tests, which assess whether certain characteristics of the received signal fulfill the expectation of the receiver, being power levels, data content, modulation, or the presence of certain signals.
The trust we can place in the receiver is therefore inherently tied to our estimate of the capabilities of the adversary, and how each of these relative capabilities might evolve over time. Unfortunately, advances in technology play in the favor of the ever-adapting adversary, not the user with installed equipment or infrastructure. There is a risk that if the capability of the adversary is underestimated, or the difficulty of signal generation is overestimated, then the user will be exposed. An additional challenge is that it can be difficult to envisage how the adversary might approach the problem. As engineers, we are often biased, even subconsciously, by best practices, rules-of-thumb, precedence, or general convention — we tend to use things in the way they are supposed to be used. In contrast, an adversary who is already committed to breaking the law is unlikely to hesitate to break some design rules too.
In this article, we examine this problem through an example of multi-frequency signal generation via existing off-the-shelf low-cost equipment which was dismissed as incapable of such signal generation. It has been generally held that the generation of multi-frequency GNSS signals is beyond the capability of an “entry-level” adversary, and so multi-frequency receivers are, to some extent, invulnerable. This belief is based on the observation that the low-cost software-defined transceivers support only a single transmit frequency and have insufficient instantaneous bandwidth to synthesize two adjacent GNSS bands. While it is true that if these devices are used as intended, they are not capable of producing multi-frequency signals; however, if they are appropriately abused, then they can, as is demonstrated here. In this example it is shown that a transceiver can be intentionally misconfigured, such that it produces an ensemble of GNSS signals at an “incorrect” frequency, but leaks harmonics into two different GNSS bands (both above and below the transmitted carrier frequency). It is further shown that if the generated signal is sufficiently strong then these harmonics can be acquired and tracked by a naive GNSS receiver — with the result that the receiver produces a dual-frequency position solution based on signals generated from a single narrow-band single-frequency transmitter.
The authors offer this as a cautionary example, suggesting that we do not underestimate the adversary, and note that if some technical feat has not yet been observed, it does not necessarily imply that it is impossible. It might only illustrate that it has not yet been provoked. Moreover, this principle might be extended beyond signal synthesis, to condition our general assumptions about what is, and what is not, technically feasible. Continuously challenging our assumptions and embracing a “red-team” approach might be necessary to more accurately quantify the risks.
Recent Developments
The spoofing of GNSS signals is controversial, with points of view on the topic ranging from the belief that spoofing is virtually infeasible, to the belief that it is trivial. Some hold that the act of spoofing is still only in the domain of state actors due to the extremely high resource requirements necessary to properly execute such an attack, while others assert that entire families of mass market receivers are vulnerable to the most simplistic of spoofing attacks. Both of these camps can be viewed as correct in light of specific recent events including ships in the Black Sea reporting that they were parked on the tarmac of a nearby international airport, to smartphones at the ION GNSS+ 2017 conference in Portland adamantly insisting that they had traveled through space and time to visit Europe circa 2014.
Throughout a variety of interesting presentations authors pointed out a number of signal characteristics that could be used to detect, and therefore mitigate, the low-cost spoofing threat. One popularly held belief is questioned here: that it is technically challenging to create a set of dual-frequency counterfeit GNSS signals having sufficient phase and delay fidelity to be acceptable to a dual-frequency GNSS receiver, and that the cost of doing so is significantly higher than the cost of creating a single-frequency counterfeit signal. By extension, it is held that dual- or multi-frequency GNSS receivers are far less vulnerable to spoofing than single-frequency receivers. This assertion caused the authors to utter a collective “hold my beer and watch this” as we set out to debunk it.
Further characteristics listed as red flags included: inconsistent navigation data; anomalous code-carrier divergence; and obvious spectral shaping indicating unexpectedly high received power levels, are discussed critically here in light of the questionable validity of the claim that dual-frequency signal generation is difficult.
Technological Barrier to Multi-Frequency Signal-Generation
In GNSS receiver design, we are very much conditioned to strive for quality and precision, tend to use extremely high quality components, and take great measures to minimize receiver losses. For this reason we might overlook the simple “ugly” shortcuts that might be available to a less fastidious adversary. The adversary is only interested in the minimum passing standard, not the best that can be achieved, so equipment and techniques that might be unthinkable to a receiver engineer might be perfectly acceptable to him.
To explore this idea, it is worth noting that there can be a large difference between: i) what the satellite actually generates, ii) what the receiver expects, iii) what signals and features the receiver actually looks for, iv) what signals the adversary is obliged to generate to satisfy this expectation, and v) what other signals the adversary can get away with producing. Therefore, the adversary can put many things into the spectrum that is observed by the receiver, provided it also includes the expected signal, and provided any extra signals are not obviously anomalous. More importantly, the spoofer can put virtually anything into the spectrum that the receiver does not observe. Under certain circumstances this fact can be exploited.
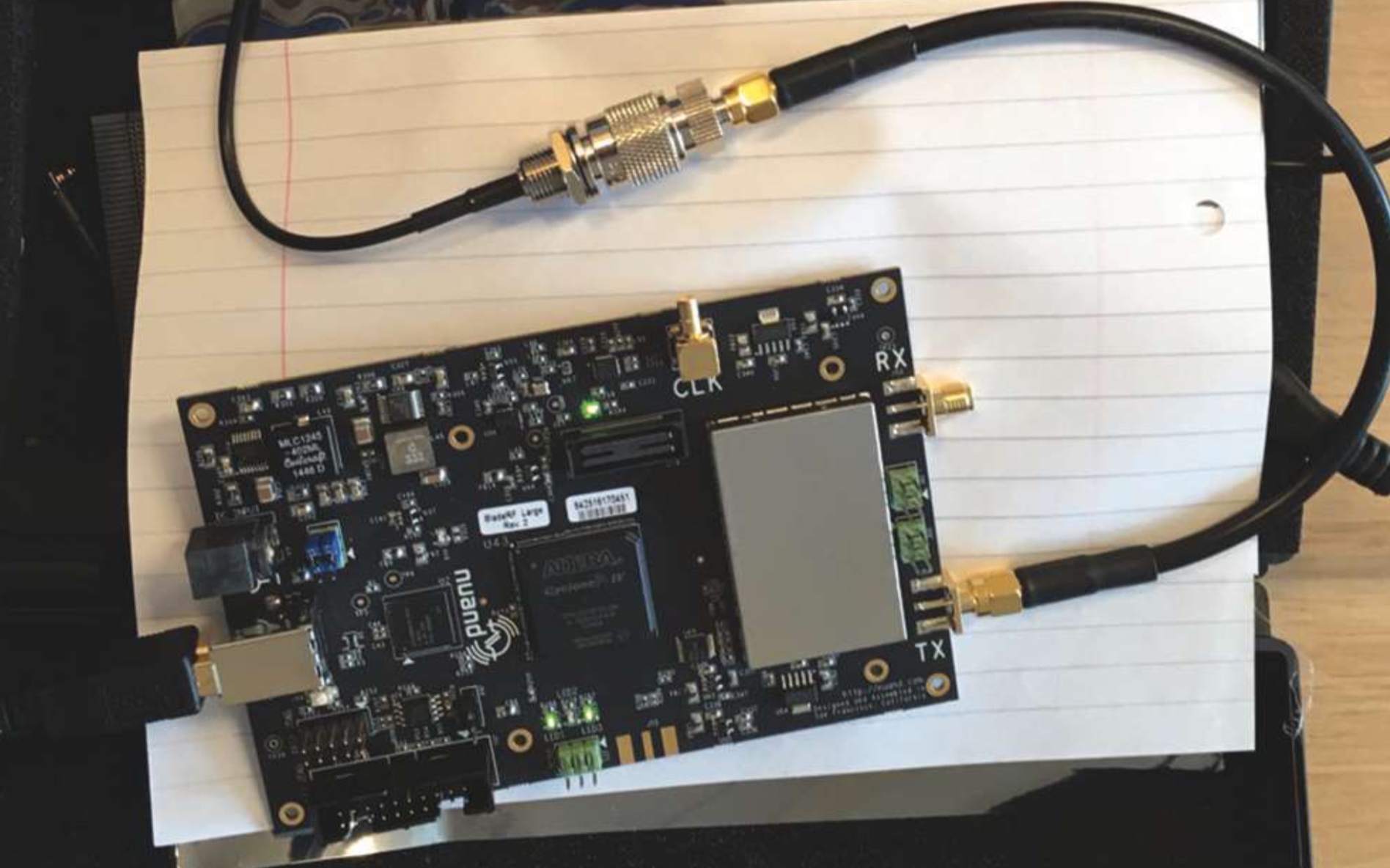
In this example, we consider a typical type of SDR transceiver that has been used in numerous demonstrations of single-frequency (L1) GNSS spoofing, however this particular device is very similar to other popular and similarly priced pieces of equipment available. These devices typically have a USB 2.0 or 3.0 interface to the host computer, produce from 20 to 40 megahertz of instantaneous bandwidth, and can modulate a baseband signal to a carrier in the range of approximately 100 megahertz to 6 gigahertz. The challenge was to perform dual-frequency spoofing with such a device. Conductive tests were performed on a commercial multi-frequency survey-grade receiver, as shown in Figure 2.

Without revealing too many details (so as not to encourage misbehavior), what follows is a brief description of the concept. It was noted that if the front-end “reconstruction” filter were disabled or removed from a transmitter, then the signal synthesized at the digital-to-analog converter (DAC) would alias across the entire spectrum. Secondly, it was noted that if the L2 signals were present in the L1 band, they would likely go unnoticed by the receiver, and vice-versa for L1 signals in the L2 band. Noting these two facts, it was clear that if a single composite baseband signal consisting of all of the L1 C/A, L1 P(Y), L2C, and L2 P(Y) signals were generated and broadcast somewhere between L1 and L2, then it would be possible, with appropriate tuning, to cause genuine-looking signals to appear at L1 and again at L2. Because of this unusual generation technique, these signals were attenuated by approximately 23 decibels relative to the total broadcast power, that is, less than 0.5% of the total broadcast power appears as a useful signal. Nonetheless the signals are present in a useful form. An example of the resultant spectrum is shown in Figure 3. This is the signal processing equivalent of playing a xylophone with a cat; it is ugly and illegal, but it works.
Given that the spectrum aliasing could be used to repeat the broadcast signals across the required bands, what remained was to remove the high-power signal and adjust the power accordingly. Fortunately, when performing a conductive test, (or a very-close range broadcast), then achieving sufficient power is not a challenge, and even though over 99.5% of the power was spent in Nyquist bands not observed by the receiver, the remaining 0.5% was sufficient. Also, it was noted that most commercial receivers implement relatively sharp band-pass filtering on the RF spectrum such that the large `interference’ signal residing in the middle of the band was rejected. An example of the carrier-to-noise ratio observed by the receiver under test is shown in Figure 1. Note that all four signals were tracked, although the P(Y) codes appeared to suffer somewhat from the narrow-bandwidth of the re-broadcast. In the figure, note also that only five of the satellites were L2C-enabled. The receiver tracked steadily for over 30 minutes, and produced a steady code-only position solution, an example of which is shown in Figure 4. While the signals might be considered `ugly hacks’ (which they are), it is important to note that contrary to popular belief neither the need for two center frequencies nor the lack of bandwidth on existing SDR platforms posed a particular problem. Moreover, although this article has demonstrated only a dual-frequency spoofing, the underlying principle can readily be extended to three or four center-frequencies. This has its most immediate value in the generation of GLONASS signals for spoofing mass-market L1-only receivers.
Detection of Spoofing Based on Signal Anomalies
Further characteristics that are popularly listed as red flags included: inconsistent navigation data; anomalous code-carrier divergence; and obvious spectral shaping indicating unexpectedly high received power levels. In light of the questionable validity of the claim that dual-frequency signal generation is difficult, these further points are briefly discussed.
Excessive code-carrier divergence observed in the received signal is not a function of whether or not a signal is counterfeit, but rather is related to the particular method used in the generation of the signal. In many cases, equipment that has been designed for use in telecommunications applications does not offer very precise carrier frequency tuning, and although it may report that it is tuned to, for example, L1, it may in fact be tuned to the nearest frequency that can be achieved with its synthesizer. For example, the device shown in Figure 5 uses a 20-bit fractional PLL and 30 megahertz reference (where the reference clock is first multiplied by three), and so can only tune with a resolution of approximately 28 hertz. Similarly, the device used in one example at ION GNSS+ 2017, uses a 22-bit fractional-N synthesizer, and can only tune with a resolution of approximately 8.5 hertz that, given its 38.4 megahertz reference, matches almost exactly the 1.7 m/s reported excess code-carrier divergence. By calculating this residual frequency error it can be compensated with a non-zero IF at signal-synthesis, at no extra cost. Once this code-carrier divergence anomaly becomes part of the “spoofing defense”, the adversary will simply correct them in the signal-generation stage. As such, this kind of detection scheme is temporary, at best.

To demonstrate this, a simple GPS/Galileo L1/E1 spoofer was assembled and used to spoof a survey receiver. The signal generation function was carefully configured to address the synthesizer considerations discussed above, such that the exact carrier frequency was known, and the delta frequency to L1 was injected as a digital IF in the signal generation stage.
The spoofer itself was based on a software-defined radio constellation simulator, written specifically to adhere to the resource constraints of a micro-computer such as the Raspberry-Pi and therefore uses very limited memory. The digital baseband GNSS signal ensemble is generated with a transmit bandwidth of 8 megahertz and is streamed via USB 2.0 to the transceiver board at an 8-bit sample depth. The device upconverts this signal to RF and broadcasts to the target receiver. The spoofer is controlled using a simple command-line interface that can be a accessed via SSH, enabling it to be controlled remotely via cell-phone, as shown in Figure 6. The complete spoofer has an off-the-shelf build cost of approximately $400 (USD).
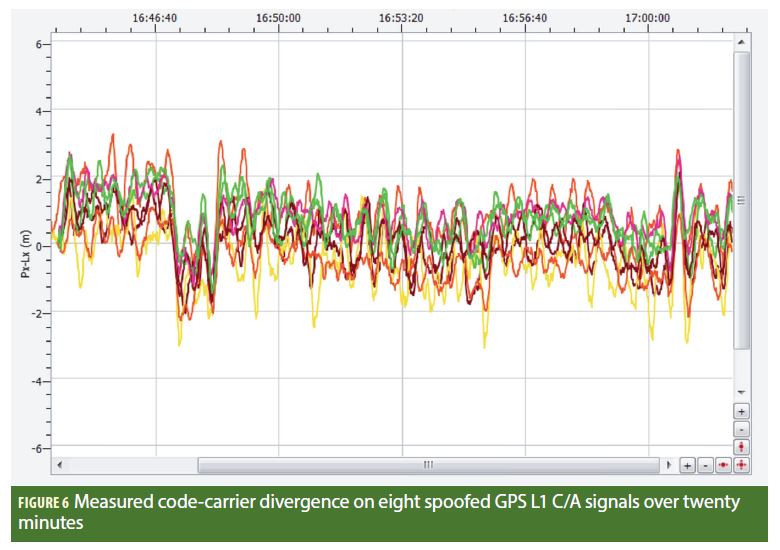
The test spoofed a static position with between eight and 10 satellites in view (owing to rising and setting satellites). A one hour test was conducted and the receiver measurements were logged as RINEX 3.02 for post-processing. The pseudorange and carrier phase were loaded from the RINEX file and code-carrier difference was formed for the GPS L1 C/A signals. These are plotted in Figure 5 for the first 20 minutes of the test for eight of the satellites observed. As can be seen, the code and carrier are coherent and do not diverge with time. As such, provided the spoofing hardware is appropriately configured (and regardless of whether it is low-cost or expensive) it is unlikely that it is possible to effect any level of spoofing detection based on the code-carrier coherency.
Inconsistent navigation data is simultaneously a very good and very bad way to isolate a spoofed signal from a real one. In one sense it is an effective approach for a user with multiple sources of information and who can, at the very least, flag navigation data inconsistencies as deserving of a closer look. In another sense it can be viewed as a weak approach, given that an adversary might generate any arbitrary navigation message, and might take relatively simple steps to ensure that the navigation data carried by the counterfeit signals matches that which would be expected.
That said, given the results of the unintentional spoofing at ION GNSS+ 2017, it appears that even when a consumer device has access to three or more streams of location and timing data (GNSS, LTE, WiFi), many implementations will happily travel three years back in time if their GNSS radio says to — implying that although the capability to detect message inconsistency is present in these devices, it is not necessarily exploited. While this aspect of spoofing resistance can certainly be improved, it might not be advisable to view it as robust against a moderately well prepared adversary who, for example, also might have an internet connection. Looking forward, even cryptographic message content that the attacker cannot generate can appear to be predicted given a small delay, and a clever attacker might find a way to insert one.
In terms of the fidelity of the physical layer of counterfeit signals, a number of authors have pointed to excessive code carrier divergence or spectrum abnormalities as being indicative of spoofing. While this might be the case in some crude implementations, in light of the discussion here, it is perhaps naive to assume that once a receiver begins to monitor these features, that the adversary will be incapable of adapting.
Obvious spectral deformation due to the use of a high spoofing power level is a parameter that can offer caution to a user in some cases, but may not actually be a wise choice of metric to base a security system on. While it is much easier for an adversary who does not care about collateral disruption to set their transmit power level to an extreme level, a more careful adversary might readily tune to within +/- 6 dB of a desired power level even on a relatively close and moving target. A crafty adversary could just as easily pre-filter their side-lobes to make their presence less obvious at the cost of a bit more computation and a bit higher code tracking noise in the output, depending on the receiver model. Additionally, since it is completely reasonable that users might want to make use of their GNSS receivers with simulators or in areas where unintentional RFI may be present, declaring the signal to be compromised based only on spectral bumps might result in an undesirably high false-alarm rate. Systems that make use of 12 megahertz clocks can produce RF spurs at 1572 megahertz, while those that use 24 megahertz clocks may produce one at 1560 megahertz or 1608 megahertz which have potential aliasing concerns. Considering how prevalent 12 and 24megahertz oscillators are in modern electronics we highlight that devices using USB 1.0, 2.0 or 3.0 will likely have at least one of these frequencies present. Moreover, it is well known that many USB 3.0 devices generate broadband interference in the L-band observable in the vicinity of their connectors. The short summary being that whether we want it or not, the modern connected world is rich in useful devices that can cause artifacts in the L-band, and declaring a navigation fault or malicious attack whenever one is detected may not be the best way to serve the end users.
Outlook
In summary, while we are glad the threat of spoofing is being discussed, it is worth noting that it is probably dangerous to adopt an industry posture that either exaggerates or minimizes the scope of the threat. It is not the case that we are adopting a new technology (GNSS), and doing so in full knowledge of the calculated risks — rather, we find ourselves having already fully embraced this technology, and only now are the risks coming to light. As users of GNSS receivers — consumer-grade equipment with scientific-grade precision — we are in some sense perfectionists, and so may have trouble identifying the dirty short-cuts that can be taken. It is worth remembering that from the perspective of the adversary, it doesn’t have to be pretty, it just has to work. While this article might at first appear to be pessimistic, suggesting that the adversary is boundlessly capable, the authors suggest that to believe the contrary, and to rely on the adversary to sleep through their comms-theory lectures and misconfigure their radio, is also probably not a good idea.
Manufacturers
The transceiver that has been used in numerous demonstrations of single-frequency (L1) GNSS spoofing is the Nuand BladeRF from Nuand LLC, Rochester, N.Y. USA, while the similarly priced pieces of equipment available refer to the HackRF from Great Scott Gadgets, Evergreen, Colorado, USA and the LimeSDR from Lime Microsystems, Surrey, United Kingdom.
Further Reading
LimeSDR https://www.crowdsupply.com/lime-micro/limesdr
BladeRF https://nuand.com/
HackRF: https://greatscottgadgets.com/hackrf/
GSA: https://www.gsa.europa.eu/system/files/reports/gnss_user_technology_report_webb.pdf
Septentrio: https://www.septentrio.com/insights/gps-spoofing-your-receiver-ready-attack
New America: https://www.newamerica.org/international-security/future-property-rights/blog/price-precision-dual-frequency/
Black Sea Incident: https://www.insidegnss.com/node/5555
ION GNSS+ Spoofing: https://www.insidegnss.com/node/5661
Authors
James T. Curran received a Ph.D. in electrical engineering from University College Cork, Ireland. Over the past decade has worked in radio navigation research at the University of Calgary, Canada, the Joint Research Center of the European Commission, Italy, and for the European Space Agency, ESTEC, Netherlands.
Aiden Morrison received his Ph.D. in 2010 from the University of Calgary, where he worked on ionospheric phase scintillation characterization using multi-frequency civil GNSS signals. He works as a research scientist at SINTEF Digital in Trondheim, Norway
Cillian O’Driscoll received his Ph.D. degree from University College Cork, Ireland. He has worked as a senior research engineer with the PLAN Group at the University of Calgary, as a Grantholder with the European Commission, and as a research support officer at University College Cork, and is currently an independent consultant specializing in GNSS signal processing.