The GPS program is setting a new space-system standard for cyberdefense, and now the federal government is creating a framework to help operators of critical infrastructure that largely rely on GPS to do the same.
The need to raise the bar is clear. Malicious coders, often backed by hostile nation-states or criminal organizations, are using automated tools to continuously probe for weaknesses:
The GPS program is setting a new space-system standard for cyberdefense, and now the federal government is creating a framework to help operators of critical infrastructure that largely rely on GPS to do the same.
The need to raise the bar is clear. Malicious coders, often backed by hostile nation-states or criminal organizations, are using automated tools to continuously probe for weaknesses:
- British Petroleum told CNBC earlier this year that its systems are attacked more than 50,000 times a day.
- The Industrial Control Systems Cyber Emergency Response Team said this summer that there were more cyber incidents the first half of fiscal year 2013 than in all of fiscal 2012.
- The National Nuclear Security Administration within the Department of Energy gets up to 10 million attacks every 24 hours, according to U.S. News and World Report.
- Gen. Ken Alexander, the head of the National Security Agency and U.S. Cyber Command told the House Armed Services Committee in March that the Defense Department fends off more than 10 million attacks daily.
Cybersecurity is ”the fastest-growing threat facing United States of America,” Michael Morell, former deputy director of the CIA told Inside GNSS at a November 1 presentation sponsored by Bloomberg Government. “The threat is here today. The number of intrusions into government, military and commercial networks is massive.”
Cyber tools are also rapidly becoming part of military arsenals. The United States is integrating both offensive and defensive capability. In March 2012 the U.S.-China Economic and Security Review Commission published a study of Chinese research papers that said GPS jamming signals would be “coordinated with computer network attack tools against key command and control nodes and networks for comprehensive full spectrum attack.”
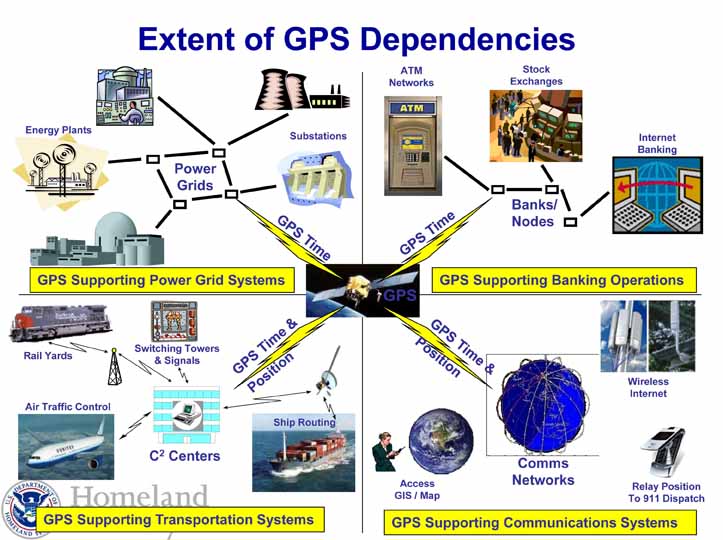
A successful attack on the GPS system could be particularly damaging because so many critical networks rely on its signals and on each other. Such interdependencies in the financial sector contributed to the collapse of the subprime mortgage market and crippled seemingly unrelated banks, said Jason Healey, director of the Cyber Statecraft Initiative at the Atlantic Council in Washington, D.C. A GPS failure could send a similar shock through power, safety, and communications networks and all the organizations that depend on them, he suggested.
OCX Cyberdefense
To help protect the GPS system, the U.S. Department of Defense (DoD) has made a special effort to beef up cyber defense in the new GPS ground segment. The Next Generation Operational Control System or OCX is a complete replacement of the old AEP or Architecture Evolution Plan control system with new software and hardware all around.
“We are not reusing any of AEP with the exception, maybe, of the ground antennas — and we’re even having to upgrade the ground antennas to meet security requirements,” said Steve Moran, director of GPS Mission Solutions at OCX contractor Raytheon.
Those antennas, at 17 monitoring stations scattered around the globe, will have their electronics updated. All of the equipment at the GPS Master Control Station (MCS) at Schriever Air Force Base near Colorado Springs, Colorado, and at the Alternate Master Control Station at Vandenberg Air Force Base in Lompoc, California, will be refreshed. The entire system is set to come on line in 2016.
Redundancy is built into the new architecture, as are checks and 24/7 monitoring to ensure that GPS spacecraft receive the correct commands from OCX uplinks. The control signals to the satellites are encrypted and, should anything happen to the Master Control Station, the alternate MCS is ready to replace it immediately, said Moran.
“All the databases and everything are duplicated. It is basically a warm backup, the only delay is the time it takes to get operators from Schriever to Vandenberg,” said Moran.
As for the software at the heart of the system, the OCX team is trained in encryption and in the best coding practices as determined by both DoD and computer security organizations such as the SANS Institute. In fact, said Mike Worden, a systems security engineer with the OCX program, the software architecture and implementation of DoD information assurance standards set OCX apart.
The OCX program has an ”unprecedented level of compliance” to DoD Instruction 8500.2 on Information Assurance (IA ) Implementation, said Worden. “I can think of only one fairly odd control that they have for systems that says if you’re attacked you need to shut down — and we certainly do not want to apply that to GPS.”
“The biggest challenge is integrating good security at all levels,” he said. “OCX is going to be sharing information on a much broader scale than what has happened in the past, and, so, what that means is we have to make sure there are protections for the networks, things like firewalls to protect your network connections.
“We need to make sure that the software that we’re designing is robust and there are no cracks in between what one software group is developing and what another one is doing. And on top of that we have to be able to demonstrate that by fulfilling those requirements. And so the real challenges, the two toughest things that keep me up at night, are secure software and integration of the entire security product.”
The OCX program is using commercial and open-source software like Linux, to keep costs in line, said Matthew Gilligan, OCX program manager and vice president in the Raytheon Intelligence, Information and Services business. The coding team, however, is refactoring — that is, editing and updating this software as necessary to address the latest threats and erase the imprint of old, less-than-secure coding habits.
“Our security engineers go back and check the code as part of fulfilling the IA requirements,” said Worden, “because what we found is that software that’s two or three years old doesn’t keep up with all the great hacking ideas that are happening around cyberspace. So, what we’re doing is taking lessons learned and applying them to our software baseline on an ongoing basis. Right now, that’s turning into re-factoring well over two million lines of code so it’s more secure and demonstrably secure.”
“The nice thing about open source, in our case,” Worden explained, “is that we can take a look at the source code and look for those vulnerabilities or those backdoors that might jeopardize our security. And, in fact we’ve done that. I’ve personally run well north of 12 million lines of open source code through a tool, looking for just those things so we can fix them before they get deployed in the system. The upshot is that we trust those COTS (commercial off-the-shelf) and FOSS (free and open-source software), but we are also going and testing and verifying — a very Reaganesque kind of approach to security.”
Defense in Depth and Breadth
The software incorporates forensics elements, alerts, intrusion detection, and a receipts-based approach to verifying interactions, Gilligan and Worden told Inside GNSS. That level of security is also being pushed out to the sites with which OCX communicates — improving their security. This gives those sites “a degree of trust that the information that they get from the GPS control segment is accurate and complete,” said Worden.
Although OCX does connect with a number of other systems, it does so only through DoD’s networks.
“We do not have direct connections to the Internet,” said Worden. “As a security guy I’m very happy about that. That buffering from us and the Internet provides a little bit better degree of protection that I really like.”
Worden said a sort of “crumple zone” is built into the system to give program managers time to react if OCX is eventually attacked successfully. Say we are attacked via one of our external connections with a normally trusted agency,” he said. “We would identify that — and we have several network controls, secure software, and then that forensic auditing that we talked about — that would give us time to react and decide what the appropriate response is. Everything from ignore it and just power through, to shutting that connection off, to anything in between that we would have to do to make sure that the GPS signal, is in fact, still being broadcast appropriately.”
“We have layers of security at the network layer,” added Worden, “all that encryption that we talked about that protects all the connections. We have authentication of users and processes. Within the system we have a lot of forensic auditing because among the things that we would be concerned with is the malicious insider, what would he or she be able to do, how quickly. . . . We’ve done several demos and scenarios where we tried to see how quickly we could find that out.”
The OCX team finished integrating the majority of the IA software into the overall program software in July. To accelerate work on the IA code, the work had been spun off at the end of 2011. Now some 70 percent of the IA coding is done and integrated into the baseline, that is, into the overall program.
“The bottom line,” said Gilligan, “is that we’ve taken a very robust, multifaceted threat assessment and then, based on that, built a system with the right layers of security in the right places so that you can detect when something is happening and then properly respond.”
And the work will continue as the threat evolves, said Moran. These efforts, he said, will give GPS users a particular level of confidence that the GPS signals are trustworthy.
“I would just suggest that one of the key advantages of GPS in the future over other GNSS systems is going to be this information assurance advantage,” he told Inside GNSS. “I don’t know of any other system that is taking the level of information assurance steps that we are with OCX to protect this critical information structure.”
“If you are a user who has access to receivers [that] can take things from multiple GNSS systems out there, you can rest assured that the signals that you’re getting from the GPS system are secure,” said Gilligan. “Nobody’s broken in. Nobody’s sent nefarious signals up to the satellite.”
Cybersecurity for GPS Users
But cybersecurity is not just for the GPS program. GPS users need to implement security measures too, experts agree, especially those managing elements of the nation’s critical infrastructure. To help organizations improve their defenses the National Institute of Standards and Technology released on October 22 a cybersecurity framework outlining a methodical approach to cybersecurity and a long list of standards and best practices.
Improving Critical Infrastructure Cybersecurity, which was developed with input from industry, “provides guidance to an organization on managing cybersecurity risk” with an objective of encouraging organizations to consider cybersecurity risk as a priority similar to financial, safety, and operational risk.
The core of the NIST framework, like the OCX program, includes identifying risks and resources, protecting systems, detecting cyber-intrusions, responding to attacks including containing their impact and recovering from cyberbreak-ins.
The document lays out a list of potential action areas with notes on existing standards and resources that can help those trying to develop or improve a cybersecurity program. It also has guidelines for organizations to measure their progress.
“It is best to think of it, given how NIST does things, as sort of an annotated bibliography of steps you can take to improve your network security,” said James Lewis, senior fellow and director at the Technology and Public Policy Program at the Center for Strategic and International Studies. “It doesn’t tell you how to do it; it is kind of like getting a menu at a restaurant. You get to pick.”
Although adopting the framework is officially voluntary, ignoring it could ultimately have legal consequences, ” suggested Lewis. “The NIST framework inadvertently, and much to the shock and horror of some people, creates the possibility of defining due diligence,” Lewis told the audience at the American Bar Association’s 23rd Annual Review of the Field of National Security Law. “And if you aren’t exercising due diligence you should be liable.”
Dan Sutherland, associate general counsel at the National Protection and Programs and Directorate within the Department of Homeland Security — the agency that would be in charge of pushing companies to implement the measure — agreed with Lewis. “NIST developing this framework is one way that we can make a contribution, essentially trying to establish a set of industry-wide best practices that would allow people to see where they need to be shooting to.”
NIST will be taking comments on the framework until December 13. It will likely issue the final version of the framework in February, Sutherland said.